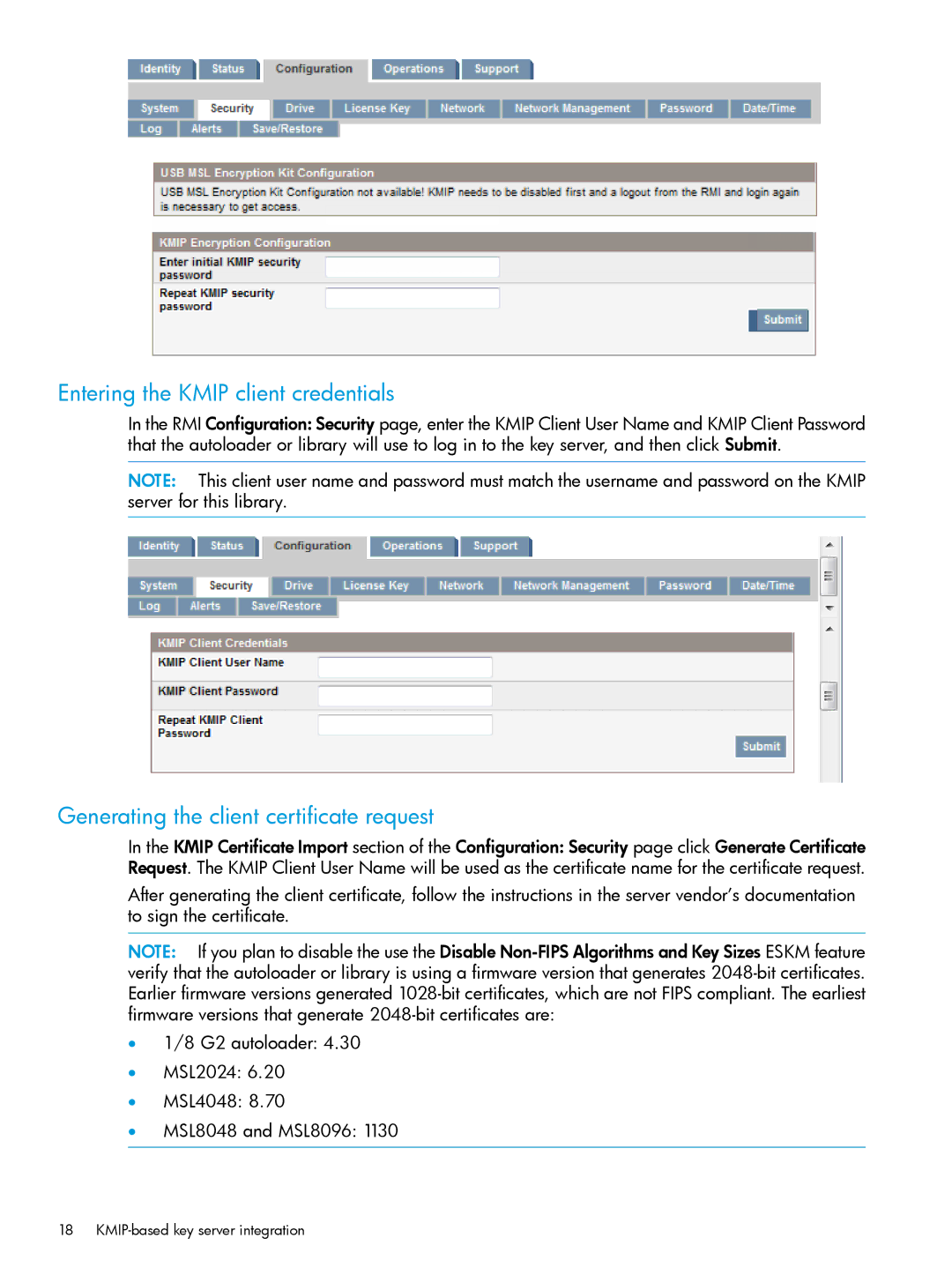
Entering the KMIP client credentials
In the RMI Configuration: Security page, enter the KMIP Client User Name and KMIP Client Password that the autoloader or library will use to log in to the key server, and then click Submit.
NOTE: This client user name and password must match the username and password on the KMIP server for this library.
Generating the client certificate request
In the KMIP Certificate Import section of the Configuration: Security page click Generate Certificate Request. The KMIP Client User Name will be used as the certificate name for the certificate request.
After generating the client certificate, follow the instructions in the server vendor’s documentation to sign the certificate.
NOTE: If you plan to disable the use the Disable
•1/8 G2 autoloader: 4.30
•MSL2024: 6.20
•MSL4048: 8.70
•MSL8048 and MSL8096: 1130