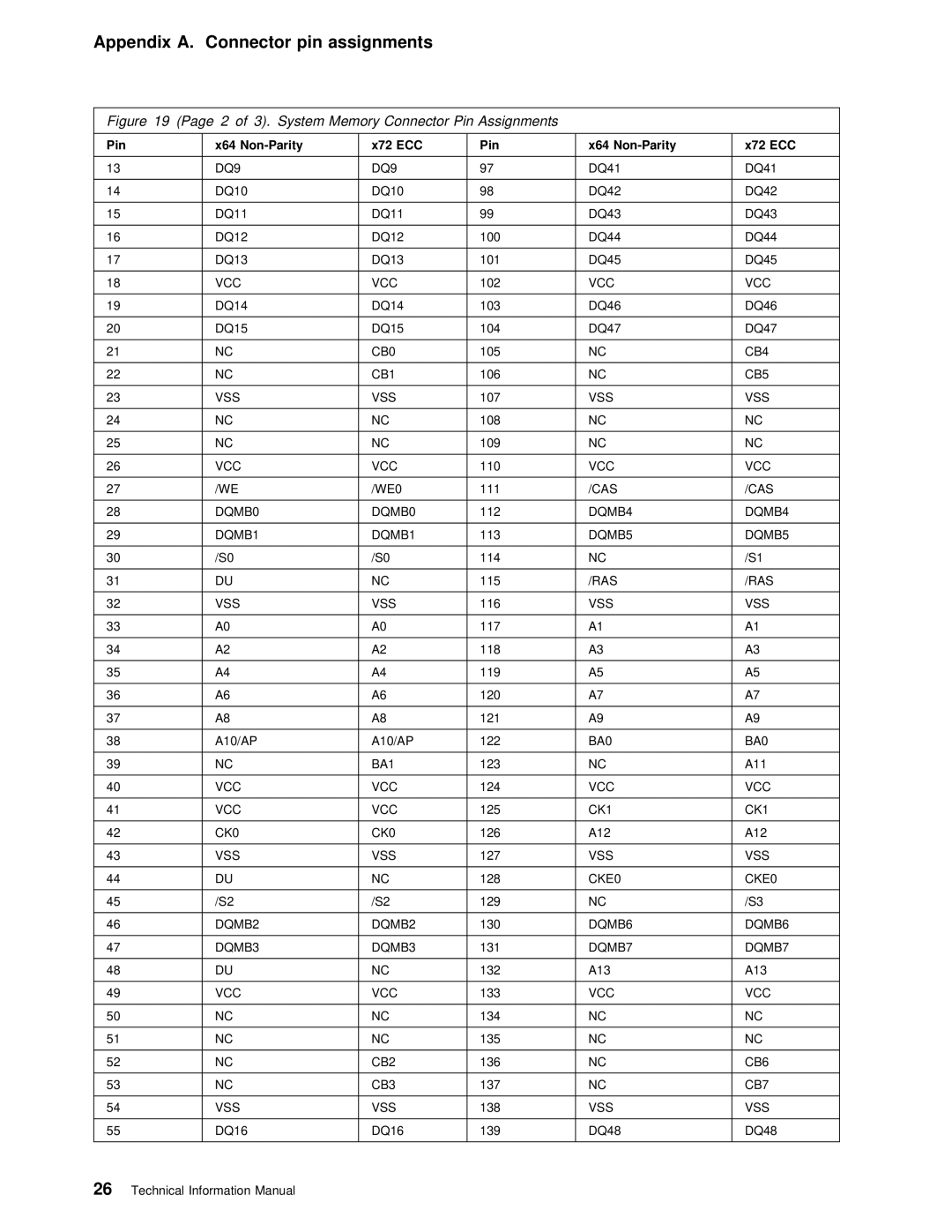
6278, 6268, 6288 specifications
The IBM 6278, 6288, and 6268 are part of IBM's extensive lineup of mid-range computers, specifically tailored for business environments in the late 1980s and early 1990s. These systems were designed to handle substantial data processing tasks, facilitating efficient business operations with robust performance and reliability.The IBM 6278 was notable for its high-performance capabilities, making it suitable for a variety of applications ranging from transaction processing to complex computations. One of the main features of the 6278 was its multiprocessing capability, which allowed it to run multiple tasks concurrently. This was achieved through a combination of advanced hardware and software that optimized performance and resource allocation.
Similarly, the IBM 6288 was recognized for its versatility and scalability. This system incorporated enhanced memory management and was capable of handling larger workloads than its predecessors. The 6288 was designed with user-friendly interfaces and supported various input/output devices, making it easier for organizations to integrate into existing IT infrastructures. Additionally, it provided improved connectivity options, essential for modern networking needs at the time.
The IBM 6268, on the other hand, offered a balance between cost and performance, appealing to smaller businesses or those with less intensive data processing requirements. Despite being less powerful than the 6278 and 6288, the 6268 still managed to include essential features such as reliable data storage, effective processing speed, and compatibility with IBM's extensive software ecosystem.
All three models utilized IBM's proprietary operating systems, which were well-known for their robustness and security features. They were built with technologies such as error detection and correction, ensuring the integrity of data processing tasks. The architecture of these systems also allowed for easy upgrades, enabling businesses to expand their capabilities without a complete overhaul of their IT infrastructure.
In summary, the IBM 6278, 6288, and 6268 represented a significant advancement in mid-range computing technology during their era. Their main features encompassed multiprocessing, scalability, and user-friendly interfaces, making them valuable assets for businesses seeking reliable and efficient computing solutions. These systems laid the groundwork for future innovations in business computing, and despite their age, they remain a significant part of IBM's legacy in the computing industry.