ÉÂÔ
Page
ÉÂÔ
Third Edition May 1999
Contents
With
SQL
Chapter
Service Program
Exception
Vi ILE
Vii
Working with Files and Devices
Files
RPG
ILE
Appendixes
Index
Copy
Apply
Does
Any
Law
Programming Interface Information
Trademarks and Service
Marks
Trademarks Or se Marks Others
Page
Xiv ILE RPG for AS/400 Programmers Guide
Guide
About This Guide
Who Should Use This
III
Prerequisite and Related Information
How to Send Your Comments
Release?
What New This
UCS-2
Risc
INZ*USER
INZ*EXTDFT
Element
CCSID*GRAPH
Changes
To this Guide
Since
For AS/400
Xxii ILE RPG for AS/400 Programmers Guide
Program creation strategies
ILE RPG Introduction
ILE RPG for AS/400 Programmers Guide
Control Specifications
RPG IV Specifications
Input Specifications
RPG IV Overview
Cycle Programming
The.When You Let Compiler Provide Logic For Your
Indicators
Subprocedure logic
First
Last
Program
Operation Codes
Example of an ILE RPG
Example of an ILE RPG Program
Second file
File Description Specifications
Program
Bonus
Output Specifications
Chain
Eval
Heading Lines That Contain Constant String Payroll
Subprocedure
ILE RPG
Not
Fqsysprt Printer
Entire Source Program
Return
Bonus PAY
Rate
10U 0 Value
Not *IN99 Eval
Interacting with the System
Commonly Used Control Language Commands
OS/400 System
System Library
Application Development Manager
System Offers Full Set Tools That You May find usef
ILE R
Services
AS/400 Tools
Overview of the RPG IV Programming15 Language
AS/400 Tools
Program Creation
RPG Programming in ILE
RPG Programming in ILE
ILE RPG, ILE C, ILE Cobo
Language You can Create
CRTSRVPGM, and Crtpgm commands. They can also Specified
Program Management
Procedure Followed Zero Or more subprocedures
Program Call
ILE
While the progra
Source Debugging
Bindable APIs
Multithreaded Applications
Accesses Are Also Threadsafe
AS/400 now supports multithreading. ILE
Does Not Directly
RPG Programming in ILE
Strategy 1 OPM-Compatible Application
Program Creation Strategies
Method
OPM-Compatible Application
Effect of ILE
Example of OPM-Compatible Program
Strategy 2 ILE Program
ILE Program Using Crtbndrpg
Related Information
Shows Run-time view Application in which an ILE CL pr Calls
ILE Program Using Crtbndrpg Example of ILE Program
XYZ
Although Actual Storage Not Deleted As it
Strategy 3 ILE Application
ILE Application Using Crtrpgmod
Using
Single-Language ILE Application
Scenario
Mixed-Language ILE Application Scenario
Single-Language Application Using Crtrpgmod and Crtpgm
Advanced Application Scenario
Strategy to Avoid
Strategy to Avoid
Activation Group
Multiple Procedures Module
Creating an Application Using Multiple Procedures
Procedures
Overview
What a module might
Prototyped Calls
Like with Multiple Dures
Module
FmtCust Name 100A Address
Using prototyped calls you can call with the same syntax
NumToChar
Numparm 30P 0 Value
Order to format Name Address Properly
Example of Module with
Made Expression Shows Call
Multiple
DDS
Example of Module with Multiple Procedures
ISO Move
Else
Procedures
ZIP
That
STATE, ZIP
Meaning that it consists only of subprocedur
Module
Module, by Coding
Keyword on the control specificati
Fcustfile Disk Fcustrpt Printer
Entire Arrsrpt Program
Icustrec
Copy QRPGLE,CVTPROCP
Callp
Endsr
Arrsrpt
Following About
ISO Move Duedate
Return Else Endif
DDS
Coding Considerations
When Coding Module with multiple procedures You Will Want
General Considerations
Coding Considerations
Subprocedure Considerations
Main Procedure Considerations
Contain a program entry procedure and only a
Cannot Contain Bound Procedure Calls
Subprocedures
Main Procedures
For Further Information
For
For Further Information
Prototyped Call
Running an
Application
ILE RPG for AS/400 Programmers Guide
File
Statements
Source
Creating a Library
Entry Utility
Using the Source Entry Utility
Using SEU
Ipcx
IPC
IPP
Ippr
Saved
Press F3 Exit To the Exit display. Type Y Yes to save
Using SQL Statements
Using SQL Statements
Statements Calculation specification Start Your
DB2 UDB
Refer toADTS thefor AS/400 Source Entry
Reference for more
Utilitymanual for Information about How SEU handles
Statement Syntax Checking
With
Command
Using the Crtbndrpg Command
Shows Their Default Values
You can use the Crtbndrpg Command interactively Batch From
Creating a Program for Source Debugging
Debugged Using a Source View Program Type
List
Creates View similar Compiler listing
Creating a Program with Static
Binding
This example you create Program
Display Module Source
Bnddir
Command
¹ Wrkjob
¹ Wrkoutq queue-name
Chain Emprec Not *IN99
Disk Fqsysprt Printer
Payroll Register Date
Empname Emprate
Using a Compiler Listing
Using a Compiler Listing
Listing
Obtaining a Compiler
Customizing a Page Heading
Customizing a Compiler Listing
Compiler Listing
Xref
Customizing the Spacing
Last Update
Indenting Structured Operations
PAGE/LINE
Listing
Errors
Either Create
This Will Add Sec Level text to the messages listed Message
FLD2
Using In-Line Diagnostic Messages
FLD1
SEU
Using Additional-Diagnostic Messages
Correcting Run-time Errors
Browsing a Compiler Listing Using SEU
Source Entry Utility
Expdds these are the defaults
Using a Compiler Listing for Maintenance
Coordinating Listing Options with Debug View Options
Specified, and in the column labeled as Sta Ment
Data
Area
Accessing the Returncode Data Area
Accessing the Returncode Data Area
Creating
Commands
Module Object
Chapter
You Create a Module using the Create
Command
Using the Crtrpgmod
Requested
Creating a Nomain Module
Creates a compiler listing which
Crtrpgmod MODULEMYLIB/TRANSSVC SRCFILEMYLIB/QRPGLESRC
Then Select option Display4 spooled
¹ Dspjob
Files
Related Files N/A Related Source Transrpt
Endsl
Other
Endsl Return
Prototype for TransInc
Creating a Module for
Prod
Prototype for ProdName
QTY
Ftrnsdta Disk Fqsysprt Printer
Itrnsrec
RPG, mainthe procedureis
Related CL Commands
Additional Examples
Modules
Binder
Binding Modules into a Program
Binding Modules into a Program
Command
Using
Into a
Crtclmod
Group
Concepts for
Export
Modules
Trpt
Using a Binder Listing
Using a Binder Listing
Changing a Module or
Changing a Module or Program
Level
Using the Updpgm Command
Reducing an Objects
Removing Observability
Size
Changing a
Changing a Module or Program
Service Program Overview
Creating a Service Program
Service Program Overview
Dspsrvpgm Payroll DETAIL*PROCEXP *DATAEXP
Creating a Service Program Using Crtsrvpgm
Strategies for Creating Service Programs
Creating a Service Program
Using Crtsrvpgm
Service Program Using Crtsrvpgm
Changing a Service Program
API
Sample Service Program
Sample Service Program
Const OPTIONS*VARSIZE
Opdesc
OPTIONS*VARSIZE
Ceedod
Enddo
Exsr
Begsr Eval
DIV MVR
Parameters Crtsrvpgm command
Creating the Service Program
Strpgmexp Signaturecvthex Export Symbolcvttohex Endpgmexp
Input String Charactern Output Hex string Character2 * n
Create the program by typing
Binding to a Program
Crtrpgmod MODULEMYLIB/CVTHEXPGM SRCFILEMYLIB/QRPGLESRC
Call Cvthexpgm
Clear Callp
Copy RPGGUIDE/QRPGLE,CVTHEXPR
Except
Clear
Sample Binder Listing
Updating the Service
Basic Binder listing for Cvthexpgm
Sample Service Program
Running a Program Using
Running a Program Using the CL Call Command
Running a Program
103
Passing Parameters using
106 shows DDS That is Referenced by the EMPRPT2 Source
Running a Program From a Menu-Driven Application
Application
Running a Program From a
Selecting Option Design menus
RPGCHG, or Rpgadd respectively
You Run Menu by Entering
Rpginq
Running a Program Using User-Created
Command
Replying to Run-Time Inquiry Messages
Replying to Run-Time Inquiry
Groups
Ending an ILE Program
Managing Activation
Wheresequence-no
Specifying an Activation
Managing Activation Groups
Group
OFF
Compatibility
Default
Running in the OPM
Activation
Deleting an Activation
Reclaim Resources Command
Group
Activation Groups Such
Referenceto Abridged
Managing the Default Heap Using RPG Operations
Dsply
Managing Dynamically-Allocated Storage
INZ*NULL
Elem@ = next@
AddName 40A
Alloc
Namelen = %len%trimrname
= *NULL
Null DOW
Dealloc
Heap Storage Problems
Managing Your Own Heap
RPG procedure This
Bindable APIs
Call Somepgm
Dynarray
SeeAPI theReference
Ceecrhp
Copy Dynarri
Ceegtst
Subsalloc
Initalloc
Dynainit
Reset
ADD Initalloc
Enddo Dynainit
Ifgt
Dynaset Export
Exsr Realloc Endif Eval
Realloc Begsr
Enddo Endsr Dynaset
Else ADD Subsalloc
Dynaget Export
Ifle
Crtsrvpgm
Get Heap Storage
Program/Procedure Call Overview
Calling Programs and Procedures
Program/Procedure Call Overview
127
Static
Calling Procedures
Calling Programs
Stack
Call Stack
Call stack
That Most r Stack Entry is Bottom
Recursive Calls
Recursive calls are only allowed For
Recent Caller
Parameter-Passing Considerations
Program/Procedure Call Overview
¹ Subprocedures in the same module
Using the Callp Operation
RPG Prototyped calls Are also Known
Callp
Calling within an Expression
Using a Prototyped Call
31A
30P
Passing Prototyped Parameters
Examples of Free-Form Call
Parameter Passing Styles
Passing by Reference
Figures below
Passing by Value
Extprocdocalc
Passing
Docalc Export
Docalc
Ceetsta Extprocceetsta
Using Operational Descriptors
ILE CEE API
Omitting Parameters
When Calling Procedure You may sometimes want Leave Out Par
OPTIONS*OMIT
Omit
Leaving Out Parameters
Passing *OMIT
OPTIONS*OMIT*NOPASS
API Qcmdexc
Psds
Passing Prototyped Parameters Checking for the Number
OPTIONS*NOPASS Const
Copy Fmtaddrp
Eval Address = %TRIMRCSTREET# + +
Trimrprovince Return
Endif Endsr
Begsr Movel
Check
OPTIONS*NOPASS
144
Ctdata
5P 0 DIM2 Ctdata
Passing Less Data Than Required
To create PRTADDR, using the source in on page 144, typ
Parameters
To create the program, PRTADDR, type
Effect
Order of Evaluation
Interlanguage Calls
Calling Considerations
Interlanguage
To obtain Actual Returned value
DCL &RET2 TYPE*CHAR LEN2 DCL &RET1 TYPE*CHAR LEN1
Fixed-Form
Call Operations
Operation Operation extender is Used With
Using the Fixed-Form Call Operations
For Callb only
Examples of Call and Callb
Passing Parameters Using Parm
Operations
Operation
Plist
Using the Plist Operation
Fixed-Form Call Operations
Procedure
Returning from a Main Procedure
Normal End
Returning from a Called
Entry Parm operation is perfor
Returning from a Called Program or Procedure
Abnormal End
Without
Returning from a Subprocedure
For the AS/400 Reference
Retu
Returning using ILE Bindable
Using Bindable APIs
Subprocedure ends abnormally
APIs
Calling a Graphics Routine
Examples of Using Bindable APIs
Calling a Graphics Routine
Ceeutx
Multithreading Considerations
Calling Special Routines
Multithreading Considerations
TheGDDM Programming Guide
Share Data
How to
Across
Will Wait For MOD1 Unlock. Procedures Not
Example, consider the situation where two procedures Called
How
To Avoid Deadlock
PROC1
Considerations
MOD2
MOD1
161
Debugging and Exception Handling
ILE RPG for AS/400 Programmers Guide
ILE Source Debugger
Debugging Programs
ILE Source Debugger
163
Attr
Debug Commands
Equate
Eval
Thread
Tbreak
Watch
Find
Preparing a Program for Debugging
Order Debug it using
Preparing a Program for
Source
Options On the Dbgview parameter for Either
Creating a Root Source View
Crtbndrpg PGMMYLIB/DEBUGEX SRCFILEMYLIB/QRPGLESRC
Crtrpgmod MODULEMYLIB/DBGEX SRCFILEMYLIB/QRPGLESRC
View
Listing View
Dbgview
Module
Program for Debugging
View
OPMSRC*NO
Starting the ILE Source
Starting the ILE Source Debugger
Strdbg Example
Setting Debug Options
Start a Debug Session for the sample debug program Debugex
Into
OPM source debug support field,
SET
Example of Removing ILE Programs from a Debug Session
Example of Adding a Service
Adding/Removing Programs from a Debug Session
Debug Session
Viewing the Program Source
Viewing the Program Source
Cobol
Lstdbg ILE
Libl PGM
Viewing a Different
Dbgex
Module
Changing the View of a
Several Different views
Cproc
Setting and Removing Breakpoints
Setting and Removing Breakpoints
Specified You Not Erate Breakpoints Specify
OPTION*NODEBUGIO
With the source positioned at the line where the breakpoint
Setting and Removing
Debug Command to set a job breakpoint
Breakpoints
Breakpoint
Setting an
Job
Debug Command Sets a Thread breakpo Single Current
Setting and Removing Unconditional Thread Breakpoints
Debug
Greater Than Equal To one
Breakpoints
Job
Line
Example of Setting a Conditional Job Breakpoint Using F13
Conditional Breakpoint
Work with Module Breakpoints
Setting a Conditional Job Breakpoint Using
Command
Break 128 when BigDate=1994-09-30
National Language Sort Sequence Nlss
Sort Sequence
Control Spec Tion Is not available
One procedure per module,procedurethe -namecan Either
On the debug command line
Main procedure or one of the subprocedures
Varia
Set a breakpoint for Module With
This Example Statement View Is used to Set Breakpoint For
Set Breakpoint For Module with
Listing, type
Using the Work with Module Breakpoints Display
Setting and Removing Conditional Thread Breakpoints
Procedurevariables-name and statement-number
Main Procedure Exit
Setting and Removing Watch Conditions
Debug Commands
Removing All Job
Conditions
Display
Characteristics of Watches
Program statemen
You Debug One Job From Another
On the debug command line, without any parameters
Setting Watch Conditions
Watch
Salary
Payroll
¹ To specify a variable or expression to be watched, type
Payroll ABC PGM
Removing Watch Conditions
Displaying Active Watches
Enddbg
IPL
Example of Setting a Watch Condition
Example of Setting a Watch Condition
BlankDisplay Module Source
Display as shown below. Instead
Stepping Through
Object
Stepping Through the Program Object
Subroutines You Can
Over Into Subprocedures
Stepping Over Call Statements
TIP
Stepping Into Call Statements
Step Into
This example, you use F22 Step Into to step Into the OPM
F22
From Program
Debugex
Step completed at line
This example, you use F22 Step Into to Subpr Which Module
InputParm
Else
Switch
Displaying Data and Expressions
Const
On page 201 shows Use
Scalar Fields RPG Definition
Unexpected Results when Evaluating Variables
Based Fields
Date, Time, Timestamp Fields
Displaying the Contents of a Table
Displaying the Contents of an Array
Eval DS12
Displaying Data Structures
Which is discussed Below
Displaying Indicators
Character Format
Displaying Fields as Hexadecimal Values
Displaying Variable-Length Fields
Data
By Pointers
Displaying Null-Capable Fields
String = 1ABCD6
STRING=%SUBSTRBIGDATE 1 4 =
Fields
= Abcdef
Changing the Value of Fields
Equating a Name with a Field, Expression, or Command
Or Command
Displaying Attributes of a Field
Equating a Name with
Examples
For
Sample Source for Debug Examples
Sample Source for Debug Examples
Program using Source 215, type
To create the program DEBUGEX, type
First Module
DS1
DIM3 Ctdata
Inzabcde
DS2
Call Rpgpgm
Occur DS2 Move
Plist Parm
Else Eval
Dump Seton
Entry Plist Parm
Dsply Seton
Source for C Procedure cproc. cproc is called by Dbgex
Exception Handling Overview
Handling Exceptions
Exception Handling Overview
217
Program Procedure P1 is Contro Boundary
Indicates That Severe error has been detected
Describes Status Work Being done by a program
Call st
Active on
Exception Message
Exception Handling within
Dure will Only Handle Errors That Subprocedure
ILE RPG Exception Handling
Operation For
PGM C
OPM
Using Exception Handlers
Using Exception Handlers
Exception Handler Priority
Nested Exceptions
Escape Message
For other Types Messages
PGM2
PRC1
Operation as well
Example of Unhandled Function Check
PGM1
PGM2, each Containing a procedur
Optimization Considerations
Using RPG-Specific Handlers
For More Information Optimization See Changing Level
Built-in-functions
Infsr error Subroutines, on Exsr Operation Code Infds
This Section Provides Some Examples How to Use Each These R
Extender
ILE RPG For AS/400 Reference provides
Program Error
Using an Error Subroutine
Operation. If Either
Explicitly c
Using a File Error Infsr Subroutine
Disk Ftrnbacklg O Fprint Printer
INFSRPrdInfsr INFDSPrdInfds
PrdInfds PrdStatus
Status
Infds
Position Definition Specification Enter
Using a Program Error Subroutine
After Keyword
Operation With Factor Entry
Proc Body of Code Goes Here
Parms
Pssr Begsr
Move Getin
If control reaches ENDSR, the procedure will fail
If this is a divide-by-zero error, add 1 to the divisor
TAG DIV
Try again Err =
Pssr
Exceptions Order Show how to avoid looping Within
Which is designed to ge
Subrou
Else ADD
After the Else
Move Inlr
OFL
Specifying a Return Point
ILE Condition Handlers
Using a Condition Handler
ILE Condition Handlers
Handlers
Printer Rpghdlr
132
LIKECondTok
Action 10I OutCondTok LIKECondTok
Is registered Procedure Parameters Include Pointer
Shows Source For Procedure
Condition Handler
Communication Area Which Contains Pointer
Ceehdlu
ARR1
Noopt
Procptr
SDS Noopt
Proc
Begsr Callp
Subst
244
Cancel Handlers
Ceertx
Ceeutx ILE
Pssr has a Return operation, so the call from the main
Procedure to SubProc will not fail
Subproc Pssrdsply
Return Endsr
Callb Ceertx Parm
INZ0 Static
Parm Omit
Select When
Condition Handlers Enabled Using
RPG using
Cancel Hdlr Dsply Msg CanHdlr
Likely Occur With
Endif Return
Condition Handler that Ignores CPF4906
MsgSev = Warning
Handle information or warning messages, otherwise percolate
ILE RPG for AS/400 Programmers Guide
Using the Dump Operation Code
Using the Dump Operation Code
Obtaining a Dump
Obtaining an ILE RPG Formatted Dump
Does not Occur
Formatted Dump
¹ If a Dump operation is bypassed By a Goto operation,
Dump
Qspl
Example of a Formatted Dump
Dump
Agement
Part 1 of 2. Data section of Formatted Dump
125 Part Data section of Formatted Dump
Order Which they are defined Gaps
Beginning of user variables, listed in alphabetical order,
259
Working with Files and Devices
ILE RPG for AS/400 Programmers Guide
Associating Files with Input/Output Devices
Defining Files
Associating Files with Input/Output Devices
261
Operation Device Dependent Device dependency Is that
Compilation Time Certain
Operation Code is Valid Only
Write
Types of File Descriptions
Naming Files
Types of File Descriptions
Program-Described
Using Files with
Files
Example of Some Typical Relationships between
OPTION*EXPDDS
Defining Externally Described Files
Defining Externally Described
Ignoring Record Formats
Renaming Record-Format Names
Renaming Field Names
Nbrofcharreplaced. Figure
Modify an
Using Input Specifications
Description
External
Indicator Record
You Then Fixed Name Specification Will Get Error
Files
Used Program This Example Field
Using Output Specifications
For Character Fields zero
Level Checking
Is written
ALL
Data Management Operations and ILE RPG I/O Operations
Defining Program-Described Files
RPG I/O Operations
SEQ Special
Delete
Data Management Operations and ILE RPG I/O Operations
Overriding and Redirecting File Input and Output
File Considerations
Overriding and Redirecting File Input and Output
273
Input Output
Input Output
Example of Redirecting
FMT1
File Locking
File Locking
Data Management manual
Program Can Chang Allocate Object
Record Locking
Record Locking
Path
See Using
Sharing an Open Data
Control For More Information
Spooling
Spooling
Program Details System Open Options Allowed for Each
Can Specify
Program Versus
Output Spooling
SRTSEQ/ALTSEQ
Database Files
Accessing
Physical Files and Logical Files
Data Files and Source
Record Format Specifications
Using Externally Described Disk Files
Access Path
Using Externally Described Disk Files
Unique
Contained Physical file CUSMSTP, which is Identified
Unique
Basdat Edtcdey
Dstref Distribution Application Field Reference
Cust Checkmf
Addr Reffldname
Disk
Valid Keys for a Record File
City
Edtcdej
Referring to
Arguments
Partial Key
Used,
Record Blocking and Unblocking
Using Program-Described Disk Files
Using Program-Described Disk Files
Indexed File
Valid
Logical file ORDDTLL. For the two fields
Keyword specifies position 15 as the starting po
Record Address File
Sequential File
10AIDISK
Move Order KEY Chain
Limits Records
Methods for Processing Disk Files
Relative Record Numbers
Methods for Processing Disk Files
ADD
Consecutive Processing
Subsequent Text Describes Each Method Processing
Examples of Sequential-by-Key Processing
Sequential-by-Key Processing
Database Programming
Database Programming manual
Weekly hours worked
Example, the employee master record
Fprint
YTDRPT1 Related Files EMPL1
FEMPL1 Disk
Iemprec Ircweek
Setoff Read EMPL1 Goto Eofend Move Enum Empno
YTDRPT2 Related Files EMPL1
Seton Endif
Eofend TAG Seton
Records Are Processed as Matching records With
For Processing Disk Files
ADD Ehwrk Tothrs
ADD Tothrs Totovt Setoff
SUB Enhrs Ovthrs
ADD Ovthrs Totovt Seton Endif Oprint
Example of Random-by-Key Processing
Random-by-Key Processing
Emstupd Descriptions
Nnhrs
Fchange
Sequential-within-Limits Processing
Change
Disk Files
Examples of Sequential-within-Limits Processing
Limits
ESWLIM1 Related Files Empmst
Flimits Disk
3PIDISK KEYLOC1 Fprint
Fempmst Disk Fprint
Relative-Record-Number Processing
ESWLIM2 Related Files Empmst
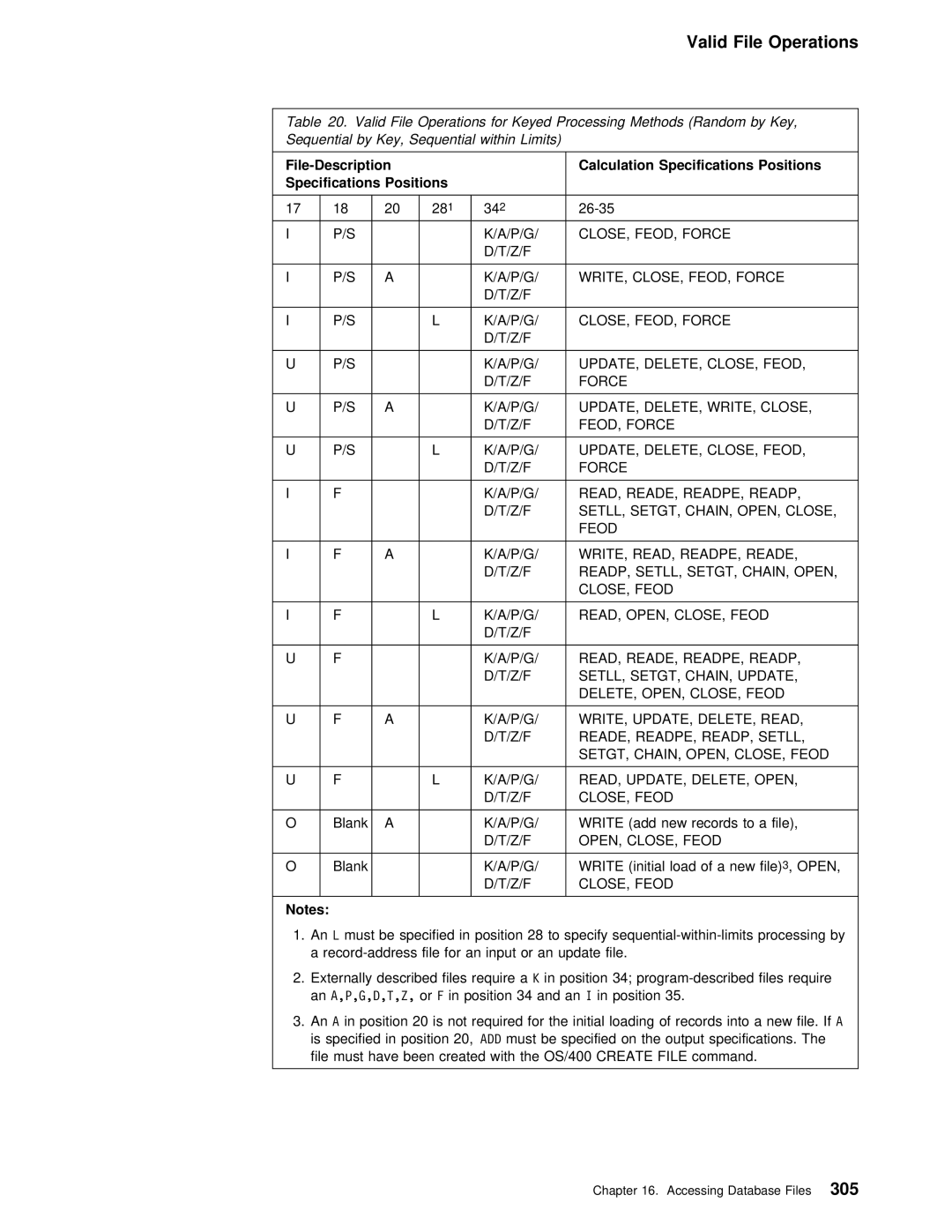
Valid File Operations
Valid File Operations
Z/F
Recno
Starting and Ending Commitment
Using Commitment Control
Using Commitment Control
Abridged for
See theBackup and Recovery manual
Commitment Control Locks
Files For
Using
Specifying
Concepts,
Journal
Example of Using Commitment Control
Receiver
Update Mastrec Tranrec
This command calls the program Revise
Control
Disk Commit Ftrans
DDM Files
Cycle
DDM Files
ReferDistributedto the Data
Pre-V3R1 DDM
DDM Files
Types of Device Files Chapter
Accessing
Attached
315
Accessing Printer Devices
Accessing Printer Devices
Specifying Printer Files
Handling Page Overflow
Overflow
On an and notline,anoverflowthe linelineis
Example of Printing a Field on Every
Example of Printing Headings on Every
OANL2
Account
Overf
Using the Fetch-Overflow
Routine in Program-Described Files
Overflow Printing Setting of the Overflow Indicator
Example of Specifying Fetch Overflow
Fetch Overflow
OPM Prtctl data structure
Changing Forms Control
File
Forms
Values Contained First four subfields
Dat
Accessing Tape Devices
Accessing Tape Devices
Print
File Name Associated Data Structure is
Using Sequential Files
Accessing Display Devices
Using Sequential Files
Ovrdbf
Using Special Files
Using Special Files
File
Program name
Description
Error
Status
Special Pgmnameuserio
Example of Using a Special File
FLD
Spcl Plist Parm FLD1 Movel Hello Write Excptn Outbuf Seton
Userio
Are Added To the end of the RPG-created Parameter list
Program User-written routine
Function
Using Workstn Files
Using Externally Described Workstn Files
On page 333 shows an example of the DDS for a display-devic
¹ Output
Prompt
Refdstref
Overlay
Descrp
Device
Specifying Function Key Indicators on Display Device Files
Specifying Command Keys Display
Processing an Externally Described Workstn File
Using Subfiles
Sfile
Field
You press Specified Function key During Read
Use of Subfiles
Name Search
SFL TEXTSubfile Record
Subfil
Using Program-Described Workstn Files
Using Program-Described Workstn Files
With
Using a Program-Described
Calculation Specifications
Input Specifications
Name
Format
Input File
Valid Workstn File Operations
Output File
Combined File
Read Operation
Exfmt Operation
Write Operation
Multiple-Device Files
Keyword. This field Initialized
Is updated
Devid
Multiple-Device Files
Database Physical File
Example of an Interactive Application
Database Physical File
345
DDS for a
Inquiry
Display Device
Main Menu Inquiry
Cusmain RPG Source
Main menu will appear as in on
Using Crtrpgmod Create Program By entering
First option specifies that the first module in the list
File Maintenance
File Maintenance
CUSMSTL1 DDS for a
Logical
Device
Display
Edtcdez
Mode
70DATE Edtcdey
Cusmnt RPG Source
Record Format contains Constant Customer File Maintenance
Else Move OFF
Subroutine Addsub Purpose
Addsub Begsr Cstkey Chain CMLREC1 Not *IN50 Move
Move Update Mode When
Move ADD Mode When
Move Delete Mode When
Move Display Mode Endsl MODE1 Endsr
Customer File Maintenance
Display Mode
Cstinq
223021
223106
On page 357 a new customer is added to the Customer Mast
30/94 Customer 00007
223143
Bathurst Avenue
ADD Mode
Delete Mode
Search by
Zip
Search by Zip Code
Code
Related Files CUSMSTL2
Szipmenu
File SZIPMENU. IT has
REFCUSMSTL2 Printqsysprt Indara
Indicates when to display Subfile When Indicator 55 is
Schzip RPG Source
ADD Zero Recnum Endsr
Write Subctl Move OFF
Move OFF
Zip
File indicator 71 on th
Routine Fills Subfile Record Read From
Subfile Is written to the screen as shown in on
Search and Inquiry by Name
Search and Inquiry by Name
For Database File Used This Program Defines one reco
Identifies Name field Key Fields
Snammenu DDS for a Display
Device File
FOOT2
Subfile
Schnam RPG Source
Records Using Subfiles
This Program Prompts the User for the Customer
File by the Setll OPERATION. then IT Displays
Example of an Interactive 367Application
File Record Count
File Indicator On the Read operation
Recnum
Inc
Judah Gould
233948 30/94 Customer 00012 Name
Inquiry by Name
Gould
Yorktown
371
Appendixes
ILE RPG for AS/400 Programmers Guide
For AS/400
RPG/400 ILE
Appendix
Differences
Debugging and Exception
Running
RPG III
RPG/400 Will Issue
Will issue the RNQ1222 inquiry Message
Will issue the RNQ1022 inquiry Message
Will Issue
Dbcs Data in Character Fields
Compiler Such Programs Will Get Compilation errors
Differences Between OPM RPG/400
Conversion Overview
Appendix B. Using
379
Hurry
File Record Length
File Considerations
USE
Log File
Conversion Aid Tool Requirements
Converting Your Source
Wont Do
Converting Your Source
Aid
Cvtrpgsrc Command
Libl
Fromfile
Curlib
Frommbr
Qrpglesrc
Tofile
None
Tombr
YES
Expcpy
Cvtrpt
Seclvl YES Insrtpl
Source
Defaults
Converting a Member Using
Performing a Trial Conversion
Converting All Members in a File
Converting Some Members
Cvtrpgsrc FROMFILEOLDRPG/QRPGSRC Frommbrpayroll TOFILE*NONE
Converting Auto Report
Obtaining Conversion Reports
Source Members
CVTRPT*NO
Data
Inserting Specification Templates
Example of Source Conversion
Example of Source Conversion
Converted source is shown in on
Example Source Conversion
To convert this source, enter
ARR2
Analyzing Your Conversion
III specifications for ARR2. The Conversion Aid
Analyzing Your Conversion
DS1
Shows Command summary for a sample Conversion
Using the Conversion
Report
Conversion Aid generates a conversion report if you specify
Call PROG1
Your
Using the Log File
Lgdate Colhdgcvt Date
Qrncvtfm Lgcent Colhdgcvt Cent
Ymmdd
Lgtime Colhdgcvt Time
Compilation Errors in Existing RPG III Code
Resolving Conversion Problems
Unsupported RPG III Features
Use of the /COPY
TEST1
Records Using
Context-Sensitive Problems
Members in the converted RPG IV source member
Comp
Use of Externally
Command Or manually Correct Code After Conversion
Structures
Char
Merging an Array with an Externally Described DS Subfield
When converted
Initializing
Extrec
Behavior With
Run-time Differences
XYZ
Dsone Extnameextrec Char
Resolving Conversion Problems
Using CL Commands
Appendix C. The Create Commands
How to Interpret Syntax Diagrams
Reading Syntax Diagrams
Crtbndrpg Command
Crtbndrpg Command
Values
KEYWORDREQUIRED-VALUE
Appendix C. The Create Commands407
PGM
Description of the Crtbndrpg Command
Program-name
Srcfile
Genlvl
Srcmbr
Text
Srcmbrtxt
Noxref
Option
GEN
Nogen
Elseif
Noext
Dbgview
Eventf
Stmt
List
Output
ALL
Print
Optimize
Datetime
Cvtopt
Graphic
Varchar
Replace
Langid
Usrprf
User
Change
Issued
USE
Exclude
Zoned
Fixnbr
Tgtrls
PRV
Inputonly
Alwnull
Bnddir
Binding-directory-name
Actgrp
Usrlibl
Qile
NEW
Crtrpgmod Command
Crtrpgmod Command
Prfdta
Nocol
Appendix C. The Create Commands421
Usrprf
Description of the Crtrpgmod command
PF4
PF1
423
Appendix D. Compiler Listings
Compiler Listings
Compiler Listing
Which was Compiled Using
Reading a
Crtb
Source member
Module or Program
Compiler options
Indentation Mark
Eject
Section
Endif
Sequence Numbers Root
Listings
Part 1 of 3. Sample Source Part of the Listing
Part 2 of 3. Sample Source Part of the Listing
Line Number
1a/ *NOSRCSTMT Source Heading
Ruler Line
Do Number
Additional
Diagnostic
Copy Member Table
Output Buffer Positions
Total Number of Characters Altered
Compile-Time Data
Character to be Altered
Alternate Sequence
Cross-Reference Table
Key Field Information
Duedate
External References List
Final Summary
Message Summary
N a L M M a R Y
Code Generation and Binding Errors
Compiler Listings
439
Bibliography
Iddu
ILE RPG
ILE RPG for AS/400 Programmers Guide
Characters
Special
443
See
Ceeutx
See AlsoILE
Control-record format, subfile Create Program
Dbcs
Describing
Dsppgmref
Binder Listing 100 Exception Service
Find
See halt
See file
See last
See long
Plist
Methods
Qual
OA-OG, OV
SEU
See DB2
Totc
ILE RPG for AS/400 Programmers Guide
Éâôù