Using the TPM Security Device (Optional) |
| Chapter 3. | 69 | |||||
| Using the computer | |||||||
| Select a Security Platform Feature and set a basic user |
|
|
|
|
| ||
3 password. | Using the TPM program |
| ||||||
4 | Complete the registration according to the instructions. |
| For more information about using the TPM program, refer to | |||||
|
|
|
| the online help for the program. |
| |||
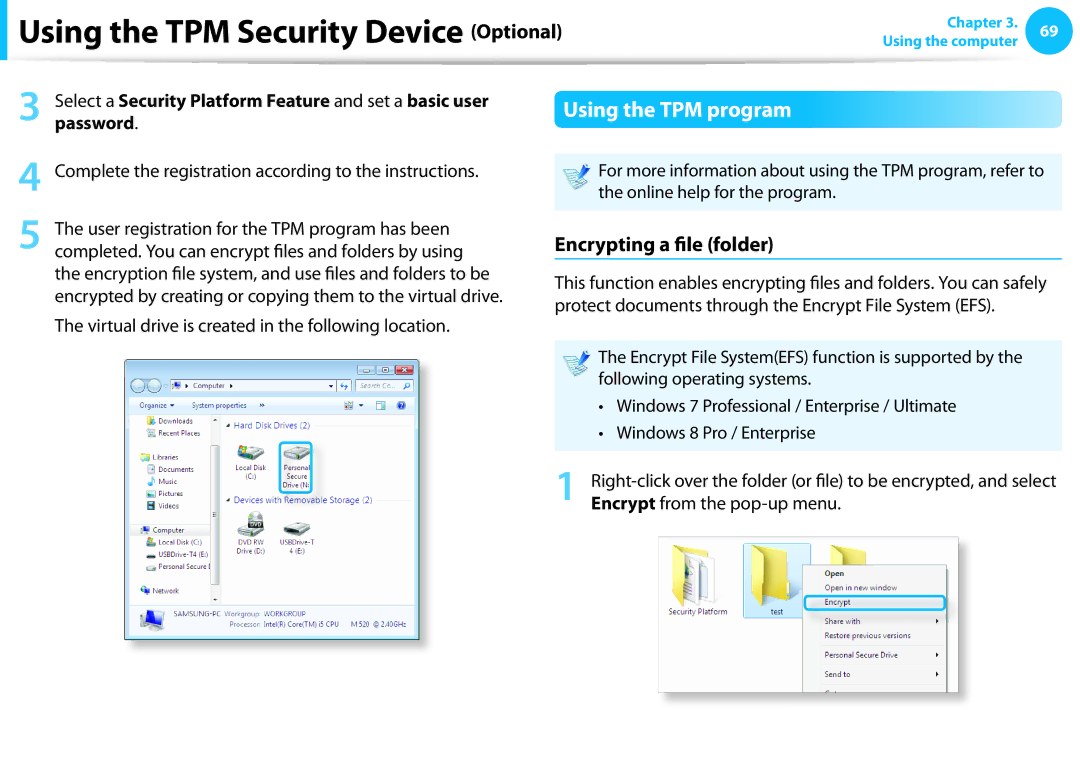
| The user registration for the TPM program has been |
|
|
|
|
| ||
5 completed. You can encrypt files and folders by using | Encrypting a file (folder) |
| ||||||
| the encryption file system, and use files and folders to be | This function enables encrypting files and folders. You can safely | ||||||
| encrypted by creating or copying them to the virtual drive. | |||||||
| protect documents through the Encrypt File System (EFS). |
| ||||||
| The virtual drive is created in the following location. |
| ||||||
|
|
|
|
|
| |||
|
|
|
|
| The Encrypt File System(EFS) function is supported by the |
| ||
|
|
|
|
|
| |||
|
|
|
|
| following operating systems. |
| ||
|
|
|
|
| •• Windows 7 Professional / Enterprise / Ultimate |
| ||
|
|
|
|
| •• Windows 8 Pro / Enterprise |
| ||
|
|
|
| 1 | ||||
|
|
|
| Encrypt from the |
| |||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|