Single port KVM over IP switch
delivery, this certificate and the underlying secret key is the same for all IP-KVM switch ever produced and certainly will not match the network configuration that will be applied to the IP-KVM switch cards by its user. The certificate's underlying secret key is also used for securing the SSL handshake. Hence, this is a security risk (but far better than no encryption at all).
However, it is possible to generate and install a new certificate that is unique for a particular IP-KVM switch card. In order to do that, the IP-KVM switch is able to generate a new cryptographic key and the associated Certificate Signing Request (CSR) that needs to be certified by a certification authority (CA). A certification authority verifies that you are the person who you claim you are, and signs and issues a SSL certificate to you.
The following steps are necessary to create and install a SSL certificate for the IP-KVM switch:
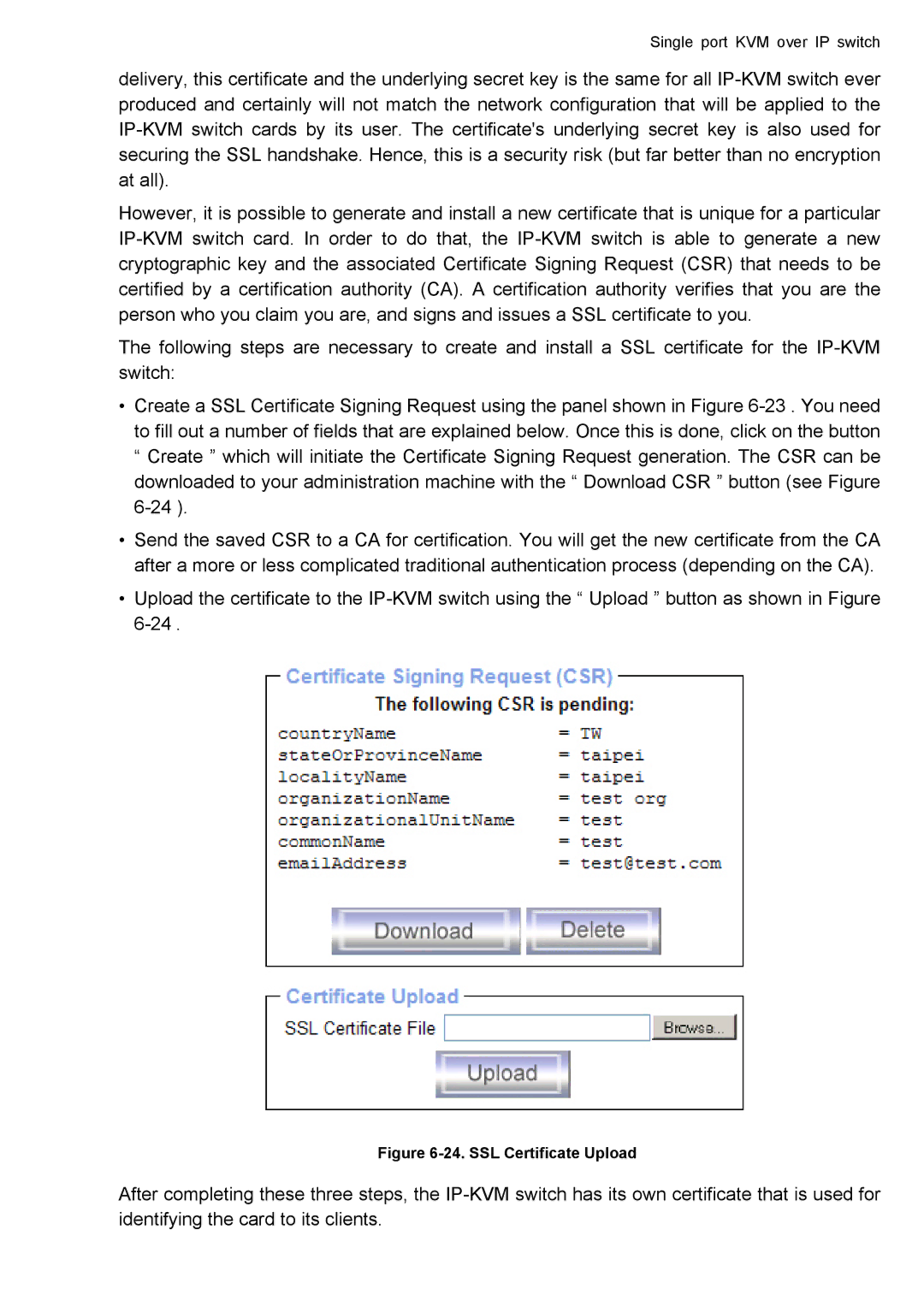
•Create a SSL Certificate Signing Request using the panel shown in Figure 6-23 . You need to fill out a number of fields that are explained below. Once this is done, click on the button “ Create ” which will initiate the Certificate Signing Request generation. The CSR can be downloaded to your administration machine with the “ Download CSR ” button (see Figure 6-24).
•Send the saved CSR to a CA for certification. You will get the new certificate from the CA after a more or less complicated traditional authentication process (depending on the CA).
•Upload the certificate to the IP-KVM switch using the “ Upload ” button as shown in Figure 6-24 .
Figure 6-24. SSL Certificate Upload
After completing these three steps, the IP-KVM switch has its own certificate that is used for identifying the card to its clients.