IEEE 802.11b/g Wireless USB 2.0 Adapter | Version 1.2 |
you may associate with your network. This feature comes in handy when you need to work at several locations where there are different network settings. Using this you can configure a different profile for each of your networks.
hClient Name: Enter any name to describe the profile.
hSSID1: Enter the SSID of the network. The SSID is a unique name shared among all points in your wireless network. The SSID must be identical for all points in the network, and is
hClick on the OK button to continue.
3.2.3Security
The next tab displayed is the Security tab. Here you can configure the authentication and encryption method that is used on your network. There are five types of security methods available: none, WPA,
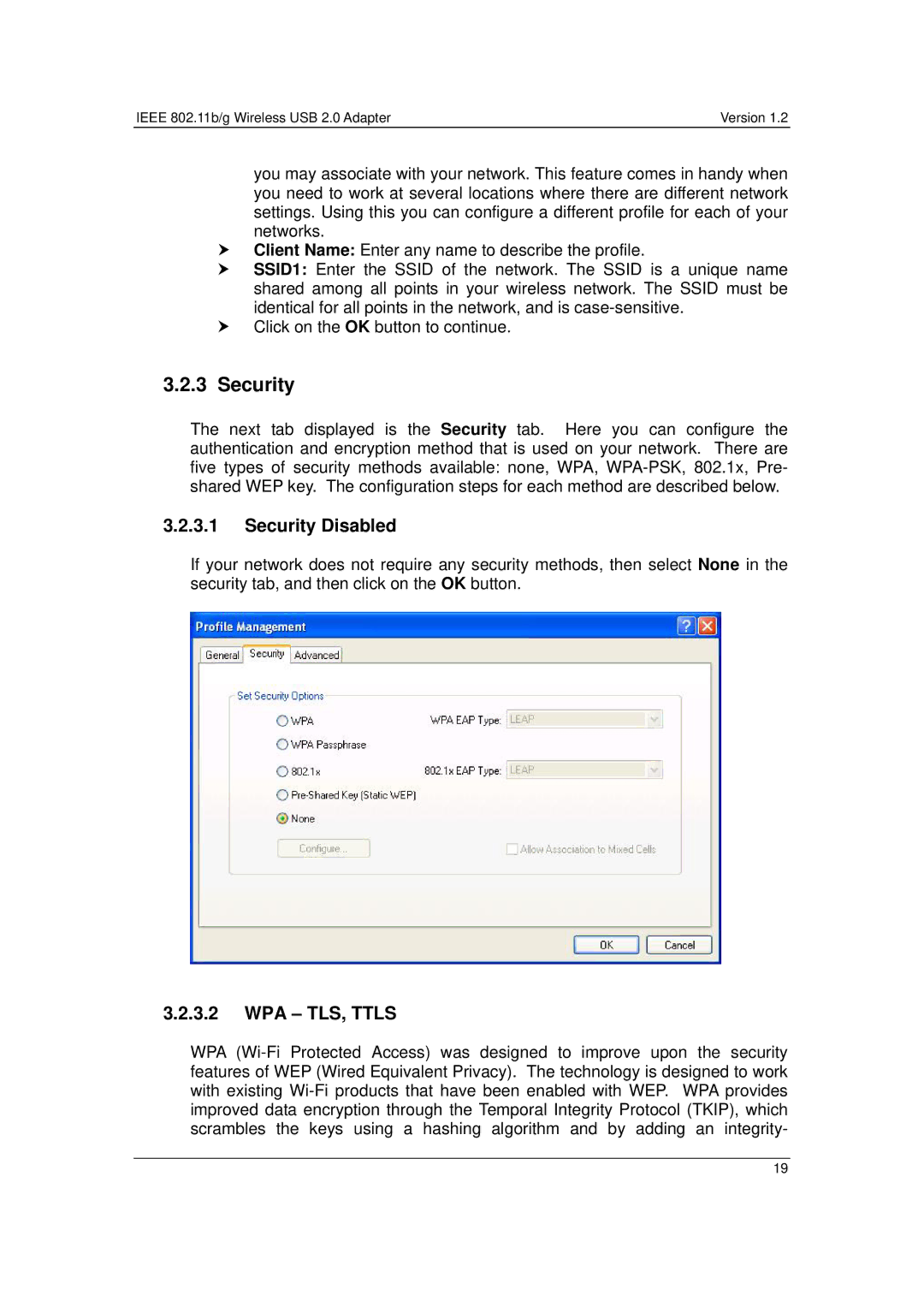
3.2.3.1Security Disabled
If your network does not require any security methods, then select None in the security tab, and then click on the OK button.
3.2.3.2WPA – TLS, TTLS
WPA
19