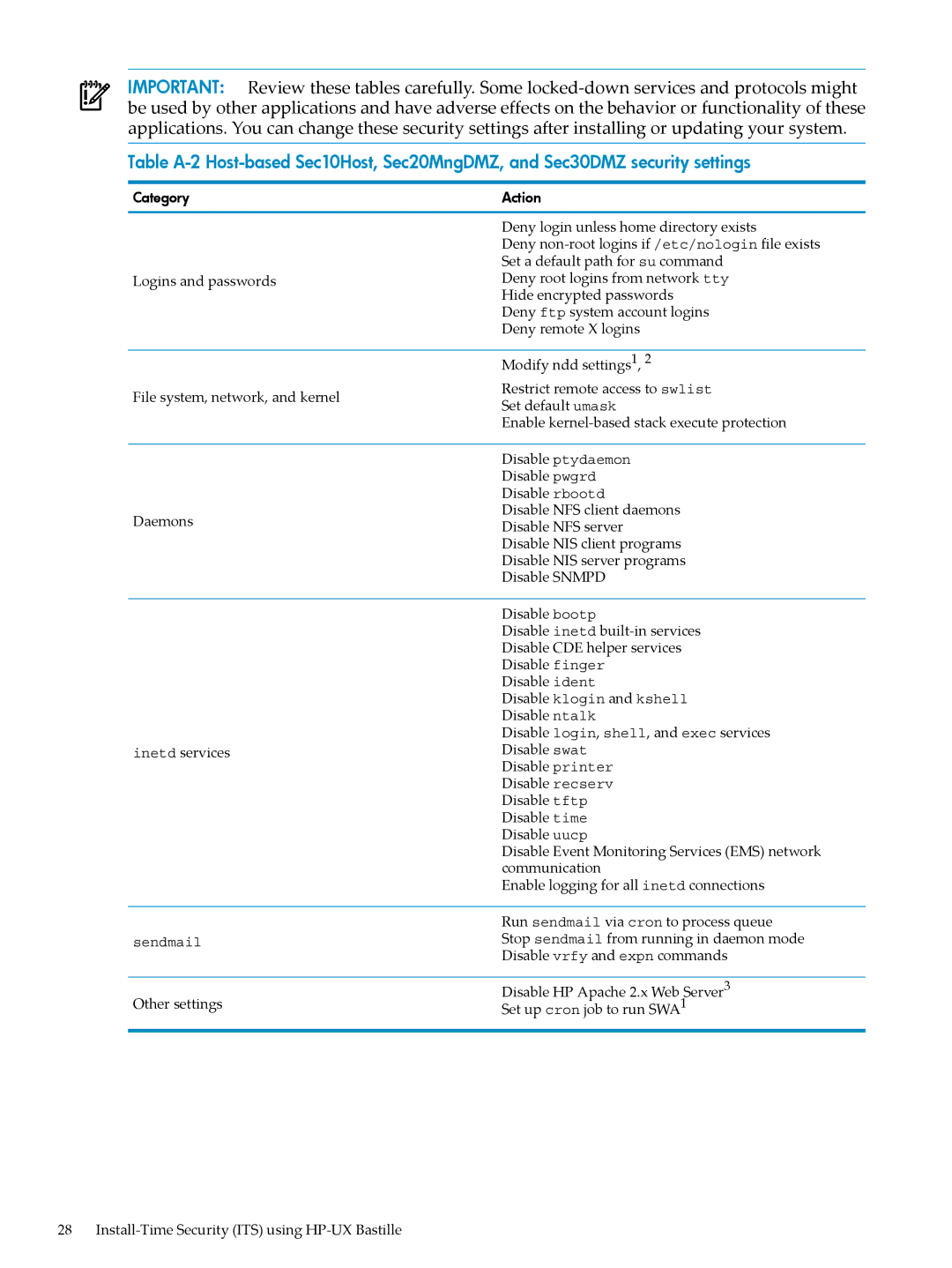
IMPORTANT: Review these tables carefully. Some
Table
Category
Logins and passwords
File system, network, and kernel
Daemons
inetd services
Action
Deny login unless home directory exists
Deny
Deny root logins from network tty Hide encrypted passwords
Deny ftp system account logins Deny remote X logins
Modify ndd settings1, 2
Restrict remote access to swlist Set default umask
Enable kernel-based stack execute protection
Disable ptydaemon
Disable pwgrd
Disable rbootd
Disable NFS client daemons
Disable NFS server
Disable NIS client programs
Disable NIS server programs
Disable SNMPD
Disable bootp
Disable inetd
Disable ident
Disable klogin and kshell Disable ntalk
Disable login, shell, and exec services Disable swat
Disable printer Disable recserv Disable tftp Disable time Disable uucp
Disable Event Monitoring Services (EMS) network communication
Enable logging for all inetd connections
sendmail
Other settings
Run sendmail via cron to process queue Stop sendmail from running in daemon mode Disable vrfy and expn commands
Disable HP Apache 2.x Web Server3 Set up cron job to run SWA1