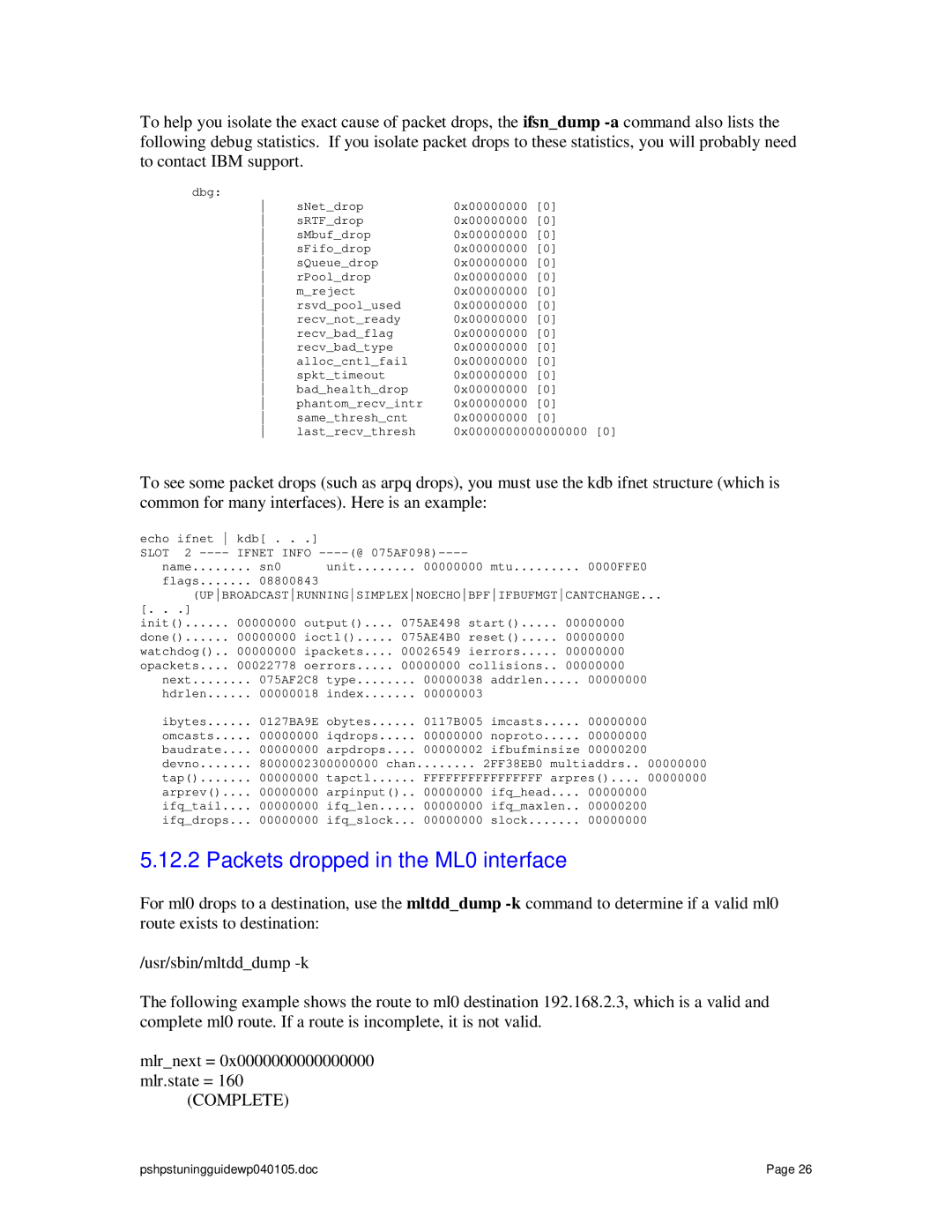
To help you isolate the exact cause of packet drops, the ifsn_dump
dbg:
sNet_drop | 0x00000000 | [0] | |
sRTF_drop | 0x00000000 | [0] | |
sMbuf_drop | 0x00000000 | [0] | |
sFifo_drop | 0x00000000 | [0] | |
sQueue_drop | 0x00000000 | [0] | |
rPool_drop | 0x00000000 | [0] | |
m_reject | 0x00000000 | [0] | |
rsvd_pool_used | 0x00000000 | [0] | |
recv_not_ready | 0x00000000 | [0] | |
recv_bad_flag | 0x00000000 | [0] | |
recv_bad_type | 0x00000000 | [0] | |
alloc_cntl_fail | 0x00000000 | [0] | |
spkt_timeout | 0x00000000 | [0] | |
bad_health_drop | 0x00000000 | [0] | |
phantom_recv_intr | 0x00000000 | [0] | |
same_thresh_cnt | 0x00000000 | [0] | |
last_recv_thresh | 0x0000000000000000 [0] | ||
To see some packet drops (such as arpq drops), you must use the kdb ifnet structure (which is common for many interfaces). Here is an example:
echo ifnet kdb[ . . . | ] |
|
|
|
|
| ||
SLOT | 2 | IFNET INFO |
|
|
|
| ||
name | sn0 |
| unit | 00000000 | mtu | 0000FFE0 |
| |
flags | 08800843 |
|
|
|
|
| ||
| (UPBROADCASTRUNNINGSIMPLEXNOECHOBPFIFBUFMGTCANTCHANGE... | |||||||
[. . . | ] |
|
|
|
|
|
|
|
init() | ...... | 00000000 output().... | 075AE498 start() | 00000000 |
| |||
done() | ...... | 00000000 ioctl() | 075AE4B0 reset() | 00000000 |
| |||
watchdog().. | 00000000 ipackets.... | 00026549 ierrors | 00000000 |
| ||||
opackets.... | 00022778 oerrors | 00000000 collisions.. 00000000 |
| |||||
next | 075AF2C8 | type | 00000038 | addrlen | 00000000 |
| ||
hdrlen | 00000018 | index | 00000003 |
|
|
| ||
ibytes | 0127BA9E | obytes | 0117B005 | imcasts | 00000000 |
| ||
omcasts | 00000000 | iqdrops | 00000000 | noproto | 00000000 |
| ||
baudrate.... | 00000000 | arpdrops.... | 00000002 | ifbufminsize 00000200 |
| |||
devno | 8000002300000000 chan | 2FF38EB0 multiaddrs.. | 00000000 | |||||
tap() | 00000000 | tapctl | FFFFFFFFFFFFFFFF arpres().... | 00000000 | ||||
arprev().... | 00000000 | arpinput() | .. 00000000 | ifq_head.... | 00000000 |
| ||
ifq_tail.... | 00000000 | ifq_len | 00000000 | ifq_maxlen.. 00000200 |
| |||
ifq_drops... | 00000000 | ifq_slock... | 00000000 | slock | 00000000 |
| ||
5.12.2 Packets dropped in the ML0 interface
For ml0 drops to a destination, use the mltdd_dump
/usr/sbin/mltdd_dump
The following example shows the route to ml0 destination 192.168.2.3, which is a valid and complete ml0 route. If a route is incomplete, it is not valid.
mlr_next = 0x0000000000000000 mlr.state = 160
(COMPLETE)
pshpstuningguidewp040105.doc | Page 26 |