User Guide
Licensing
Export
Contents
Upgrading the NVG Software
Snmp Agent 183
Copyright 2007-2008 Nortel Networks
Preface
Who Should Use This Book
VPN Gateway 6.0 Application Guide for SSL Acceleration
Related documentation
Product Names
Appendices
How This Book Is Organized
Users Guide
Adding User Preferences Attribute to Active Directory
Host# telnet IP Address
Typographic Conventions
AaBbCc123
Getting help from the Nortel Web site
How to Get Help
VPN
Introducing the VPN Gateway
SSL Acceleration
VPN
Hardware Platforms
Web Portal
Feature List
Software Features
User Authorization
Transparent Mode Access
User Authentication
Client Security
Secure Service Partitioning
Accounting and Auditing
Networking
SSL Acceleration
Branch Office Tunnels
Portal Guard
Public Key Infrastructure
Scalability and Redundancy
Certificate and Key Management
Supported Handshake Protocols
Supported Key and Certificate Formats
Hash Algorithms
Cipher Suites
Secure Portable Office SPO Client
Virtual Desktop
Introducing the VPN Gateway
Introducing the ASA 310-FIPS
HSM Overview
FIPS140-1 Level 3 Security
Extended Mode vs. Fips Mode
Wrap Keys for ASA 310-FIPS Clusters
Concept of iKey Authentication
Types of iKeys
CODE-USER
Available Operations and iKeys Required
HSM-SO HSM-US
Additional HSM Information
Introducing the ASA 310-FIPS
Initial Setup
New and Join
Clusters
Configuration is Replicated among Master NVGs
Clustering Over Multiple Subnets
IP Address Types
Ports
Two-Armed Configuration
Interfaces
One-Armed Configuration
Two-Armed Configuration without Application Switch
Setup Menu
Configuration at Boot Up
Setting Up a One-Armed Configuration
Installing an NVG in a New Cluster
Step Action Choose new from the Setup menu
Specify the port you want to use for network connectivity
Enter a Management IP address MIP
Enter a default gateway address
Enter network mask and Vlan tag ID
Specify the host IP address for the current VPN Gateway
Setting Up a Two-Armed Configuration
Configure the management interface port number
Specify a new port number for the traffic interface
Enter a default gateway address on the traffic interface
Specify a host IP address on the traffic public interface
Interface gateway IP address
Select
Complete the New Setup
Press Enter if correct
Enter if correct
Wizard
To accept
Enter to accept
Create the account
Enter Network mask for the pool range Creating IP pool
10.10.20.99
Settings Created by the VPN Quick Setup Wizard
Default Network
Basic VPN Setup
Default Services
Joining a VPN Gateway to an Existing Cluster
Enter the VPN Gateway ’s host IP address
Specify the port to be used for network connectivity
Enter the Management IP address MIP of the existing cluster
Step Action Choose join from the Setup menu
Accepts
Specify the VPN Gateway type
Complete the Join Setup
Enter the default gateway on the traffic interface
As slave
Wait until the Setup utility has finished
Admin user
Installing an ASA 310-FIPS in a New Cluster
Installing an ASA 310-FIPS
Use Fips or Extended Security Mode? fips/extended
HSM-SO password
HSM-SO password, or use the same HSM-SO password as for Card
Press Enter to select new
Adding an ASA 310-FIPS to an Existing Cluster
Setup Menu Join Join an existing iSD cluster New
Adding an ASA 310-FIPS to an Existing Cluster
For this HSM card
Re-enter to confirm HSM-SO iKey has been updated
Cluster
Verify that CODE-SO iKey black is inserted in card
That you used in Step
End
Log in as user boot, password ForgetMe
Reinstalling the Software
If correct
Continue y/n? y Press Enter to continue
Tag id or Enter
Restarting system Alteon WebSystems,I nc C Booting Login
Upgrading the NVG Software
Main# boot/software/download
Performing Minor/Major Release Upgrades
Enter the host name or IP address of the server
Activating the Software Upgrade Package
Enter hostname or IP address of server server host
Name or IP
Software Management# cur
At the Software Management# prompt, enter
Here
Activate ok, relogin
Main# boot/software/cur
Upgrading the NVG Software
Managing Users and Groups
User Rights and Group Membership
Access the User Menu
Step Action Log in to the NVG cluster as the admin user
Adding a New User
Add the new user and designate a user name
User# edit certadmin
Define a login password for the user
Assign the new user to a user group
Verify and apply the group assignment
Apply the changes
Groups# /cfg/sys/user User# edit certadmin
Verify and apply the changes
Remove the admin user from the certadmin group
User# edit admin
Adding Users through Radius
Step Action Log in to the NVG cluster
Login certadmin
Changing a Users Group Assignment
User admin# groups/add Enter group name certadmin
Type the passwd command to change your current password
Changing a Users Password
Changing Your Own Password
Type the password command to initialize the password change
Changing Another Users Password
Apply the changes
Deleting a User
User# del certadmin
User# list Oper Root Admin Certadmin User# apply
Certificates and Client Authentication
Generating and Submitting a CSR Using the CLI
~ ! @ # $ % * / \ ?
Save the private key to a file
Apply your changes
Save the CSR to a file
Open and copy the CSR
KEY----- and -----END RSA Private KEY
Submit the CSR to Verisign, Entrust, or any other CA
PEM NET DER
Adding Certificates to the NVG
Copy-and-Paste Certificates
Copy the contents of your certificate file
Certificate 1# apply Changes applied successfully
Copy-and-Paste Private Key
Copy the contents of your private key file
Paste the contents of the key file at the command prompt
Using TFTP/FTP/SCP/SFTP to add Certificates and Keys
Name or IP address
Enter the desired file name
Add your private key if in a separate file
End
Create a New Certificate
Update Existing Certificate
Step Action Check the certificate numbers currently in use
Add a certificate with a new certificate number
Step Action
Configure a Virtual SSL Server to Require a Client Certificate
Main# cfg/cur ssl
Apply your settings
SSL# server
Require
Enter for client certificate
Generating client certificates
Specify the validity period, key size, and serial number
Key size 512/1024 Serial number of client certificate
Main# cfg/ssl/server
Cert.pfx
Export Client Certificate
Com
Transmit Private Key and Certificate to User
Download and add a CRL from a TFTP/FTP/SCP/SFTP server
Revoking Client Certificates Issued by an External CA
Managing Revocation of Client Certificates
Crl.der
Crl.ascii
Creating Your Own Certificate Revocation List
Automatic CRL Retrieval
Main /cfg/cert 1/revoke/automatic
Http//10.42.128.30/server.crl
Info/certs command
Click Connect
Enter the password in the Ndic login screen Click Connect
Client certificate support
Paste the CSR
Signing CSRs
Main# cfg/ssl/server #/adv/sslconnect/verify/cacer
Provide the requested information
Generate Test Certificate
Step Action Specify an unused certificate number
Automatic CRL Retrieval
Show Certificate Information
General Commands
Show Subject Information
Check if Key and Certificate Match
Show Key Information
Show Key Size
Certificates and Client Authentication
Virtual Desktop
Licensing vdesktop
Running the Virtual Desktop on Client Computers
Click Save
Launch Vdesktop from Portal
Virtual Desktop Operations
Command Line Interface
Procedure
Connecting to the VPN Gateway
Establishing a Console Connection
Requirements
Running Telnet
Enabling and Restricting Telnet Access
Establishing a Telnet Connection
Enabling and Restricting SSH Access
Establishing a Connection Using SSH Secure Shell
Running an SSH Client
Telnet IP address
Establishing a Connection Using SSH Secure Shell
Accessing the NVG Cluster
ForgetM
User Access Level Description Default Account Group Passwo
CLI vs. Setup
Command Line History and Editing
Idle Timeout
Troubleshooting the NVG
Check the Access List
Enable Telnet or SSH Access
Cannot Connect to VPN Gateway through Telnet or
Verify the Current Configuration
Check the IP Address Configuration
Cannot Add an NVG to a Cluster
Cannot Contact the MIP
Add Interface 1 IP Addresses and MIP to Access List
# /cfg/sys/accesslist/add
Troubleshooting the NVG
Console Connection
NVG Stops Responding
Telnet or SSH Connection to the Management IP Address
Administrator User Password
User Password is Lost
Operator User Password
Root User Password
An ASA 310-FIPS Stops Processing Traffic
Password enter the admin user password
# /info/events/alarms
Main# maint/hsm/login
Password associated with the HSM-USER iKey for card
Resetting HSM Cards on the ASA 310-FIPS
Main# /boot/delete
End
Step Action
Existing
Enter the same secret passphrase as was used Former cluster
Transfer the cluster wrap key to card
Same secret passphrase as was used in the former Cluster
Wait for the setup of the added ASA 310-FIPS to finish
Main# cfg/gtcfg
Main# maint/starttrace
User Fails to Connect to the VPN
Aaa
Ike
Dns
Ssl
Ipsec
Ippool
Ftp
Upref
Smb
Netdirectpacket
Netdirect
Is Net Direct enabled and configured correctly?
Netdirectpacket
End
Cannot download the NetDirect Zipped file from client PC
Network Diagnostics
System Diagnostics
Installed Certificates and Virtual SSL Servers
# /stats/dump
# /cfg/sys/cur
# /info/ethernet
# ping IP address of virtual server
Error Log Files
Active Alarms and the Events Log File
# /cfg/ssl/server #/trace/ssldump
# /info/events/download
Unable to download NetDirect from VPN server
Troubleshooting the NVG
Supported Ciphers
Appendix Supported Ciphers
Supported Ciphers cont’d
Cipher List Formats
Modifying a Cipher List
Cipher Strings and Meanings
Supported Cipher Strings and Meanings
Cipher Strings and Meanings cont’d
Appendix Snmp Agent
SNMPv2-MIB
Supported MIBs
SNMP-TARGET MIB
SNMP-FRAMEWORK-MIB
Limitations
SNMP-USER-BASED-SM-MIB
IP-MIB
IANAifType-MIB
ALTEON-ISD-PLATFORM-MIB
Following Snmp traps are supported by the VPN Gateway
Supported Traps
Snmp Agent
Appendix Syslog Messages
List of Syslog Messages
Config filesystem corrupt beyond repair
Operating System OS Messages
Root filesystem corrupt
Missing files in config filesystem
Config filesystem corrupt
System Control Process Messages
System started isdssl-version
Name singlemaster
Name isddown
Name logopenfailed
Name makesoftwarereleasepermanentfailed
Name license
Name copysoftwarereleasefailed Sender IP
Name sslhwfail
Name hsmnotloggedin
Name partitionednetwork
Name softwareconfigurationchanged
Name ssimipishere
Name licenseexpiresoon
Traffic Processing Messages
Vbscript error reason for hostpath
Javascript error reason for hostpath
Jscript.encode error reason
Css error reason
Socks error reason
Html error reason
Bad Ipport data line in hc script
Bad regexp expr in health check
Proxy connect host name too long host
Certificate CRL handling errors
TPS license limit limit exceeded
Gzip error reason
License expired
Certificate CRL handling warnings
Startup Messages
AAA Subsystem Messages
Configuration Reload Messages
Host host ip is up accounted for in the license pool
Log functionality
Ldap backends unreachable Vpn=\id\ AuthId=\authid\
IPsec Subsystem Messages
PFS is required but not provided by %s
All credits are exhausted for IPSec SA
Ignoring request to roam from %s to %s
Error while decoding certificate DER Id
Bad clicert, Can’t find issuer in clicert
Failed to allocate IP addr from empty pool
Failed to decode client cert
Revocation byte length %d
Deleting the QM replaced by new rekeyed QM
Loaded ca certificate %s
Loaded server cert %s
Syslog Messages in Alphabetical Order
Syslog Messages in Alphabetical Order
Syslog Messages in Alphabetical Order cont’d
Config filesystem re-initialized
Down
AAA
Html
IPsec Isakmp SA Established Isddown
Cfg/sys/cur command
Gateway but /cfg/vpn # /ser
Loaded server id *will not Processing
Received Delete Isakmp SA
Socks error reason
System started isdssl-version
VPN LoginFailed Vpn=id
Appendix License Information
OpenSSL License Issues
Original SSLeay License
GNU General Public License
GNU General Public License
Terms and Conditions for COPYING, Distribution Modification
227
License Information
No Warranty
Apache Software License, Version
231
License Information
Scope
Appendix HSM Security Policy
Overview
Applicable Documents
Algorithm How it is used by the HSM module Used Fips Mode?
Capabilities
SHA-1
Module Interfaces
Physical Security
Components
Definition of Security Relevant Data Items
HSM Security Policy
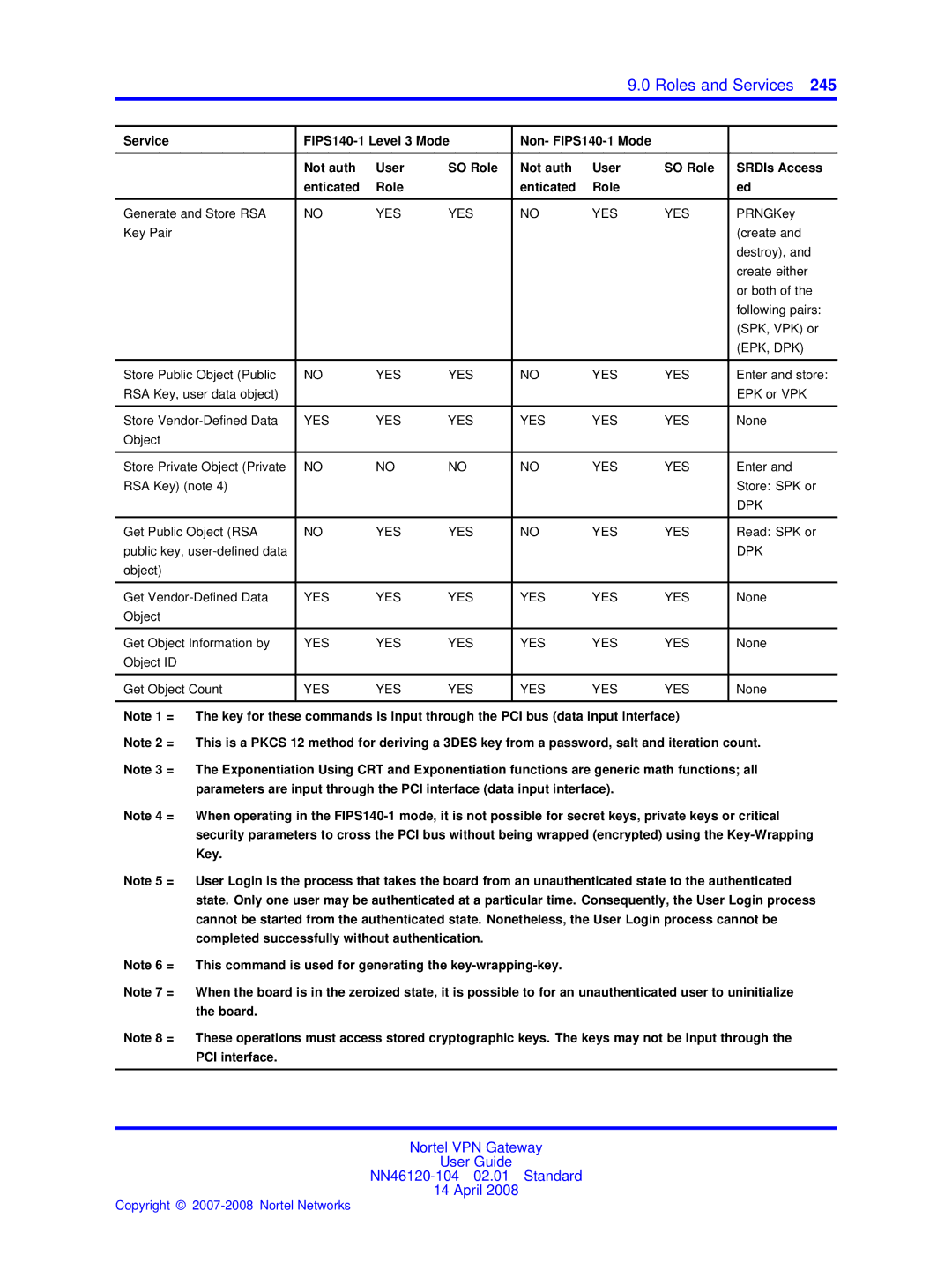
Roles and Services
User Creation
Services
YES
Service FIPS140-1 Level 3 Mode
EPK, DPK
EPK
MK, Sopin
Key Generation
Key Management
Key Distribution
Key Storage
Key Entry and Output
Modes
Fips 140-1 Mode
Key Destruction
Key Archiving
Self-Tests
Non-FIPS 140-1 Mode
RC4 KAT
Conclusion
Appendix Definition of Key Codes
Allowed Special Characters
Syntax Description
Allowed Special Characters Explanation
Redefinable Keys
Example of a Key Code Definition File
Appendix SSH host keys
Methods for Protection
VPN Gateway
SSH host keys
261
Step Action Click Start and select Run
Install All Administrative Tools Windows 2000 Server
Register the Schema Management dll Windows Server
Add Standalone Snap-in window is displayed
Create a Shortcut to the Console Window
Under Snap-in, select Active Directory Schema and click Add
Click Continue
Permit Write Operations to the Schema Windows 2000 Server
Right-click Attributes, point to New and select Attribute
Create the nortelSSLOffload class as shown
Create New Class
Create the isdUserPrefs attribute as shown Click OK
Click Next Click Finish
Add isdUserPrefs Attribute to nortelSSLOffload Class
Add the nortelSSLOffload Class to the User Class
Click OK
Adding User Preferences Attribute to Active Directory
Appendix Using the Port Forwarder API
General
=1&c=1
Creating a Port Forwarder
Demo Application
Content.zip file
Example
Creating a Port Forwarder Authenticator
Example
Using the Port Forwarder API
Adding a Port Forwarder Logger
Using the Port Forwarder API
Example
Connecting Through a Proxy
Statistics
Monitoring the Port Forwarder
Status
Using the Port Forwarder API
CLI Command Line Interface
Access Rules
Glossary
Base Profile
Console Connection
Cluster of VPN Gateways
CRL Certificate Revocation List
CSR Certificate Signing Request
DPort Destination Port
DIP Destination IP Address
DTE Data Terminal Equipment
Extended Profile
IP Interface
Http Proxy
Master
MIB Management Information Base
NTP Network Time Protocol
Nslookup
Passphrase
PEM Privacy Enhanced Mail
Portal
Setup Utility
Port Forwarder
Real Server Group
Slave
SIP Source IP Address
Snmp Simple Network Management Protocol
SPort Source Port
SSL VPN client
SSL Secure Sockets Layer Protocol
STP Spanning Tree Protocol
TLS Transport Layer Security
Virtual Router
VIP Virtual Server IP Address
Virtual SSL Server
Vlan Virtual Local Area Network
509
Index
HSM
SSL
298
Page
User Guide