Se rvi ce Re quest Pro cess ing wi th Securi ty
5.The Application Handler calls the specified service using system security to check authorization.
Note: You may need to update your surrogate security definitions to allow the successful invocation of the CICS application program (EXEC CICS START TRANSID). See your mainframe security administrator if your site has this requirement.
Security Checking from Mainframe to UNIX
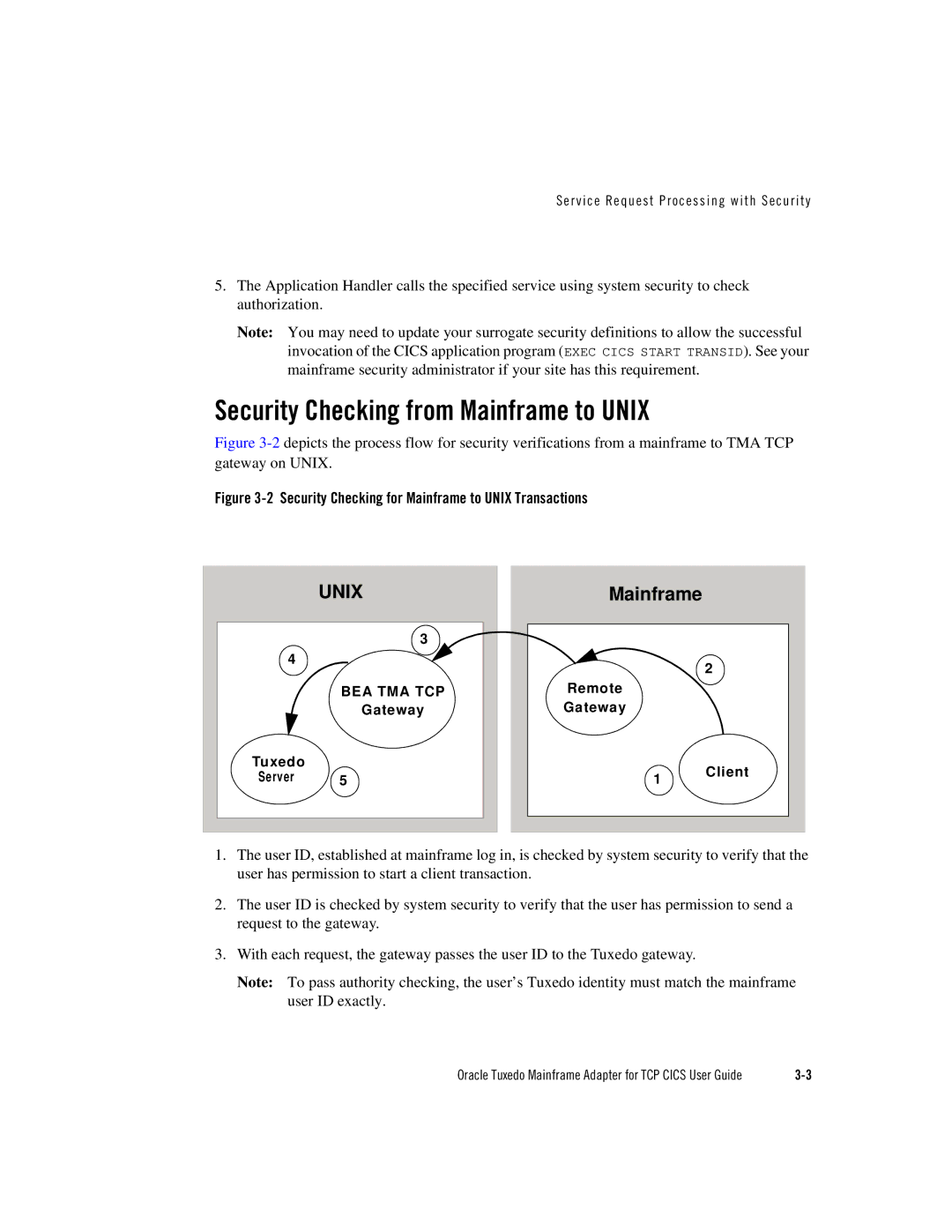
Figure 3-2 depicts the process flow for security verifications from a mainframe to TMA TCP gateway on UNIX.
Figure 3-2 Security Checking for Mainframe to UNIX Transactions
| UNIX |
| 3 |
4 |
|
| BEA TMA TCP |
| Gateway |
Tuxedo |
|
Server | 5 |
Mainframe |
|
| 2 |
Remote |
|
Gateway |
|
1 | Client |
|
1.The user ID, established at mainframe log in, is checked by system security to verify that the user has permission to start a client transaction.
2.The user ID is checked by system security to verify that the user has permission to send a request to the gateway.
3.With each request, the gateway passes the user ID to the Tuxedo gateway.
Note: To pass authority checking, the user’s Tuxedo identity must match the mainframe user ID exactly.
Oracle Tuxedo Mainframe Adapter for TCP CICS User Guide |