Security Checking from UNIX to Mainframe
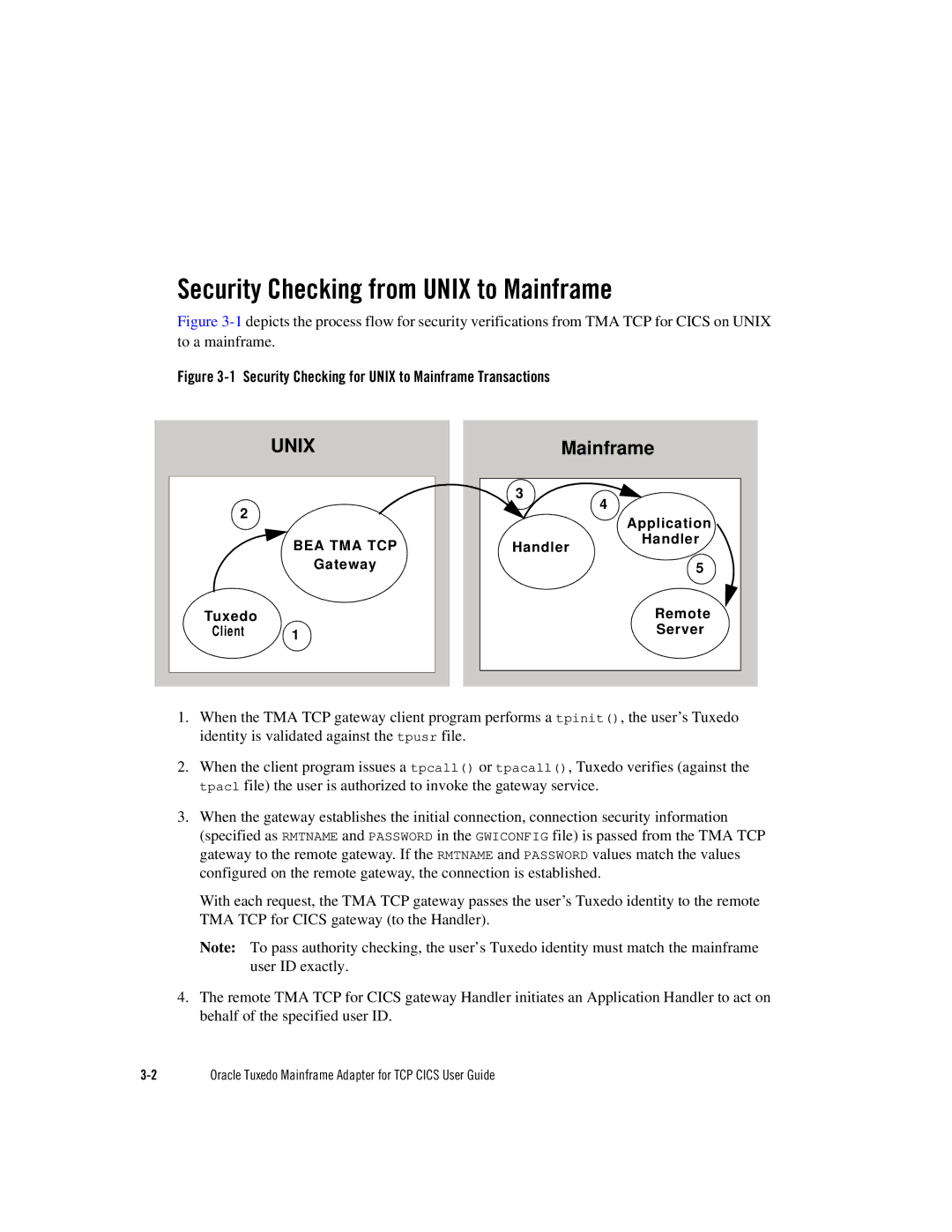
Figure 3-1 depicts the process flow for security verifications from TMA TCP for CICS on UNIX to a mainframe.
Figure 3-1 Security Checking for UNIX to Mainframe Transactions
| UNIX |
2 |
|
| BEA TMA TCP |
| Gateway |
Tuxedo |
|
Client | 1 |
| Mainframe | |
3 |
| 4 |
|
| |
|
| Application |
Handler | Handler | |
| ||
|
| 5 |
|
| Remote |
|
| Server |
1.When the TMA TCP gateway client program performs a tpinit(), the user’s Tuxedo identity is validated against the tpusr file.
2.When the client program issues a tpcall() or tpacall(), Tuxedo verifies (against the tpacl file) the user is authorized to invoke the gateway service.
3.When the gateway establishes the initial connection, connection security information (specified as RMTNAME and PASSWORD in the GWICONFIG file) is passed from the TMA TCP gateway to the remote gateway. If the RMTNAME and PASSWORD values match the values configured on the remote gateway, the connection is established.
With each request, the TMA TCP gateway passes the user’s Tuxedo identity to the remote TMA TCP for CICS gateway (to the Handler).
Note: To pass authority checking, the user’s Tuxedo identity must match the mainframe user ID exactly.
4.The remote TMA TCP for CICS gateway Handler initiates an Application Handler to act on behalf of the specified user ID.
Oracle Tuxedo Mainframe Adapter for TCP CICS User Guide |