| Table |
| ||
|
|
|
| |
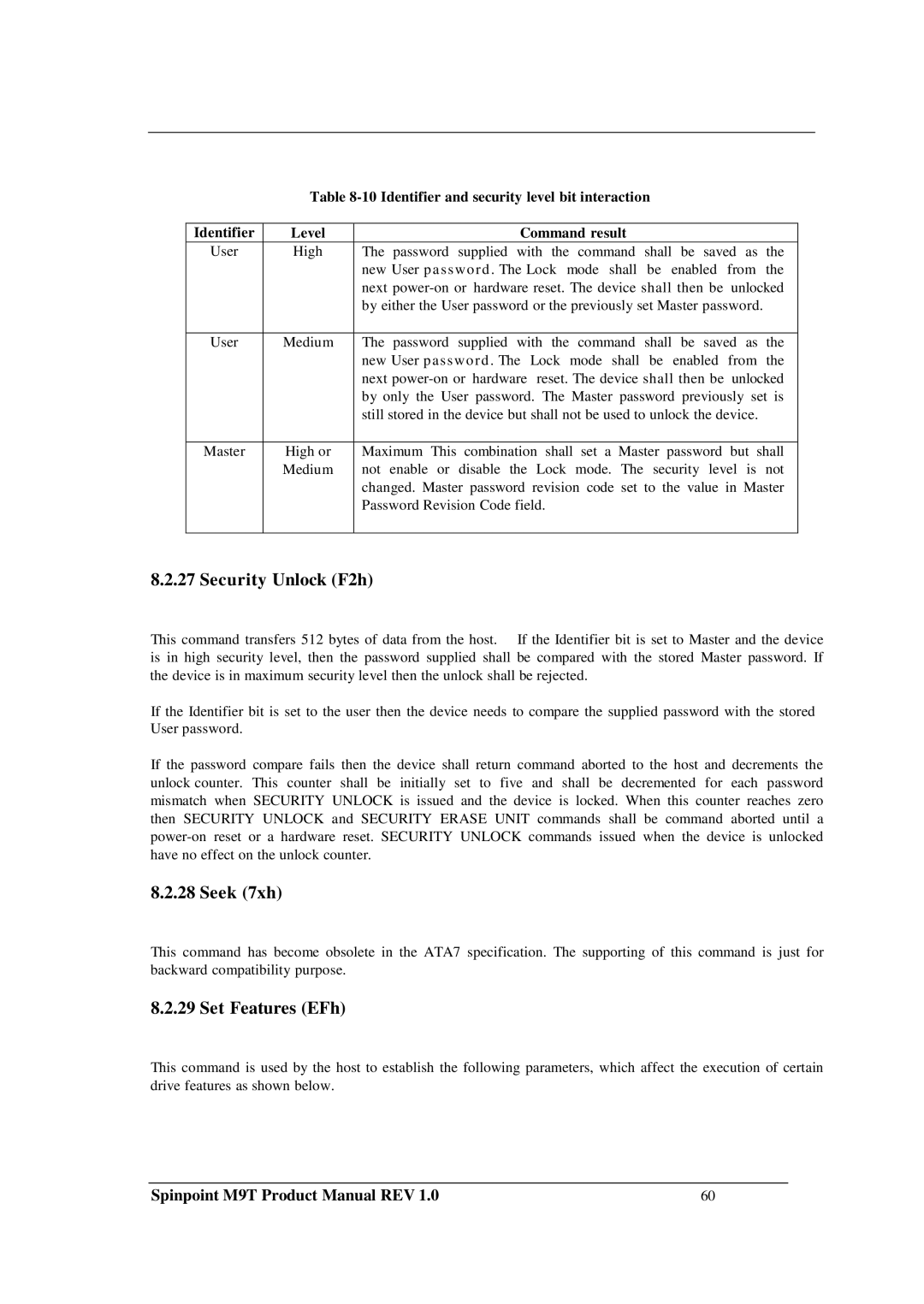
Identifier | Level | Command result |
| |
User | High | The password supplied with the command shall be saved as the | ||
|
| new User password. The Lock mode shall be enabled | from the | |
|
| next | unlocked | |
|
| by either the User password or the previously set Master password. | ||
|
|
| ||
User | Medium | The password supplied with the command shall be saved as the | ||
|
| new User password. The | Lock mode shall be enabled | from the |
|
| next | reset. The device shall then be | unlocked |
|
| by only the User password. The Master password previously set is | ||
|
| still stored in the device but shall not be used to unlock the device. | ||
|
|
| ||
Master | High or | Maximum This combination shall set a Master password but shall | ||
| Medium | not enable or disable the Lock mode. The security level is not | ||
|
| changed. Master password revision code set to the value in Master | ||
|
| Password Revision Code field. |
| |
|
|
|
|
|
8.2.27 Security Unlock (F2h)
This command transfers 512 bytes of data from the host. If the Identifier bit is set to Master and the device is in high security level, then the password supplied shall be compared with the stored Master password. If the device is in maximum security level then the unlock shall be rejected.
If the Identifier bit is set to the user then the device needs to compare the supplied password with the stored User password.
If the password compare fails then the device shall return command aborted to the host and decrements the unlock counter. This counter shall be initially set to five and shall be decremented for each password mismatch when SECURITY UNLOCK is issued and the device is locked. When this counter reaches zero then SECURITY UNLOCK and SECURITY ERASE UNIT commands shall be command aborted until a
8.2.28 Seek (7xh)
This command has become obsolete in the ATA7 specification. The supporting of this command is just for backward compatibility purpose.
8.2.29 Set Features (EFh)
This command is used by the host to establish the following parameters, which affect the execution of certain drive features as shown below.
Spinpoint M9T Product Manual REV 1.0 | 60 |