WEP
Short for Wired Equivalent Privacy, a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. WEP is designed to provide the same level of security as that of a wired LAN.
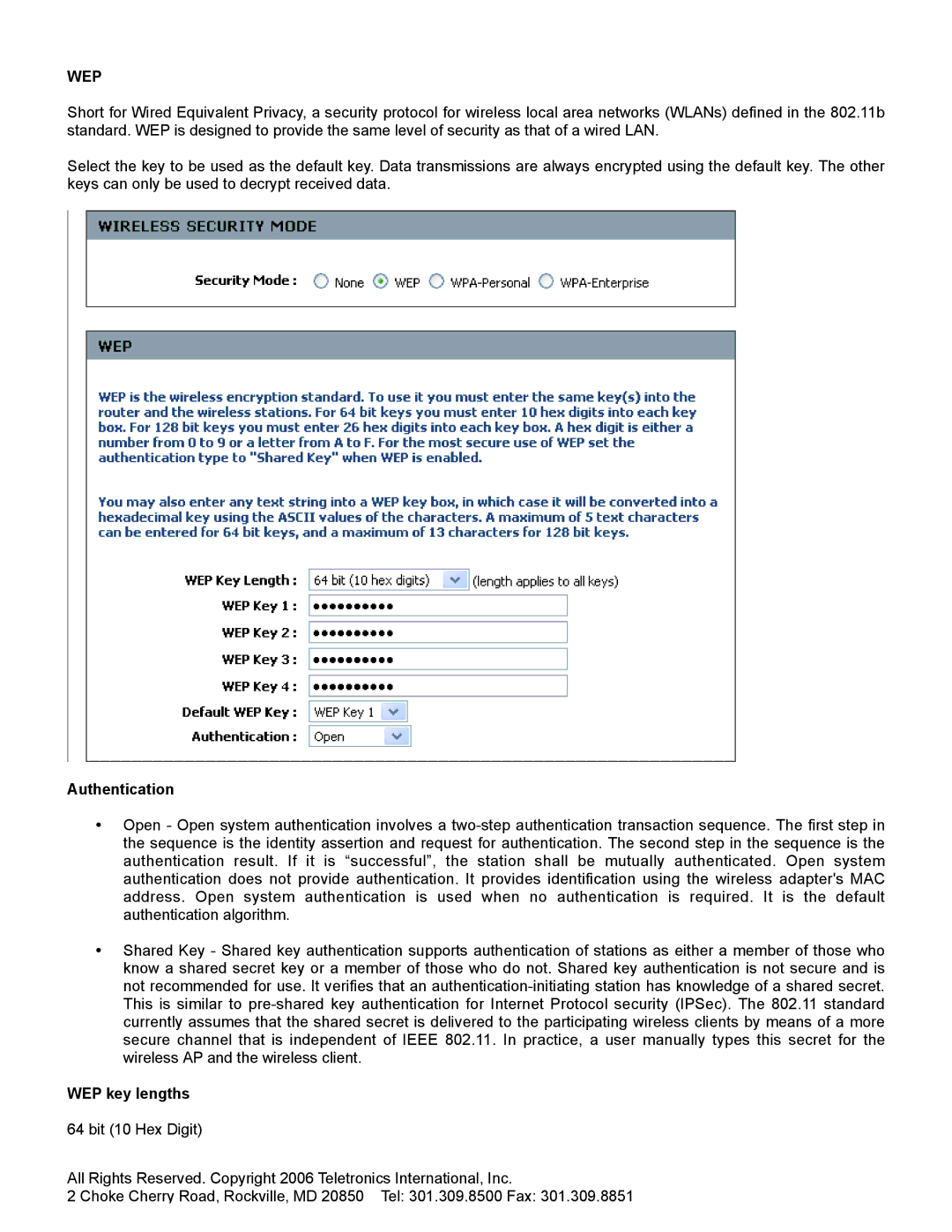
Select the key to be used as the default key. Data transmissions are always encrypted using the default key. The other keys can only be used to decrypt received data.
Authentication
•Open - Open system authentication involves a two-step authentication transaction sequence. The first step in the sequence is the identity assertion and request for authentication. The second step in the sequence is the authentication result. If it is “successful”, the station shall be mutually authenticated. Open system authentication does not provide authentication. It provides identification using the wireless adapter's MAC address. Open system authentication is used when no authentication is required. It is the default authentication algorithm.
•Shared Key - Shared key authentication supports authentication of stations as either a member of those who know a shared secret key or a member of those who do not. Shared key authentication is not secure and is not recommended for use. It verifies that an authentication-initiating station has knowledge of a shared secret. This is similar to pre-shared key authentication for Internet Protocol security (IPSec). The 802.11 standard currently assumes that the shared secret is delivered to the participating wireless clients by means of a more secure channel that is independent of IEEE 802.11. In practice, a user manually types this secret for the wireless AP and the wireless client.
WEP key lengths
64 bit (10 Hex Digit)
All Rights Reserved. Copyright 2006 Teletronics International, Inc.
2 Choke Cherry Road, Rockville, MD 20850 Tel: 301.309.8500 Fax: 301.309.8851