Contents
Introduction
Configurable Igmp timers and counters
Query solicitation rapid recovery from topology changes
How clients leave groups queries and timers
Example of bad choices for timer values
Products and software versions this note applies to
Igmp feature Software versions Products
4 AlliedWare OS How To Note Igmp
Queriers and Snoopers
5 AlliedWare OS How To Note Igmp
Igmp overview
6 AlliedWare OS How To Note Igmp
Messages
IP address, binary
7 AlliedWare OS How To Note Igmp
Choosing group addresses
MAC address, hex
8 AlliedWare OS How To Note Igmp
Avoid x.0.0.y, x.0.1.y, x.128.0.y, and x.128.1.y
Example
9 AlliedWare OS How To Note Igmp
Igmp snooping
Configure switch
10 AlliedWare OS How To Note Igmp
11 AlliedWare OS How To Note Igmp
Explanation of Igmp snooping
Group List Entry timeout 257 Secs Ports All Groups 235
Using Show command output to investigate Igmp state
Group List Entry timeout 136 secs Ports None
12 AlliedWare OS How To Note Igmp
13 AlliedWare OS How To Note Igmp
Group Last Adv
14 AlliedWare OS How To Note Igmp
When a client leaves a group
Group List Entry timeout 247 secs Ports
15 AlliedWare OS How To Note Igmp
Multiple potential Igmp queriers
16 AlliedWare OS How To Note Igmp
17 AlliedWare OS How To Note Igmp
When there are no group members
Other Querier timeout .. secs
All Groups Entry timeout Secs Ports
When a client joins a group
Group List Entry timeout 225 secs Ports
18 AlliedWare OS How To Note Igmp
Group List Last Adv
19 AlliedWare OS How To Note Igmp
Group List
20 AlliedWare OS How To Note Igmp
21 AlliedWare OS How To Note Igmp
Igmp proxy
Switch 3 is an Igmp Proxy
22 AlliedWare OS How To Note Igmp
23 AlliedWare OS How To Note Igmp
Group List Entry timeout 122 secs Ports None
All Groups Entry timeout 145 Secs Ports
Explanation of Igmp proxy
Group Entry timeout Secs Ports
24 AlliedWare OS How To Note Igmp
Group Entry timeout 182 secs Ports
25 AlliedWare OS How To Note Igmp
How query solicitation works
Query solicitation rapid recovery from topology changes
26 AlliedWare OS How To Note Igmp
27 AlliedWare OS How To Note Igmp
Initial state
Example
Why convergence takes so long without query solicitation
28 AlliedWare OS How To Note Igmp
Explanation from the perspective of switch 2, the snooper
29 AlliedWare OS How To Note Igmp
All Groups Entry timeout 236 secs Ports
30 AlliedWare OS How To Note Igmp
31 AlliedWare OS How To Note Igmp
Explanation from the perspective of switch 1, the querier
Group Entry timeout 18 secs Ports
Shows this entry
Group Entry timeout 115 secs Ports
32 AlliedWare OS How To Note Igmp
33 AlliedWare OS How To Note Igmp
Speeding up Igmp convergence in a non-looped topology
34 AlliedWare OS How To Note Igmp
Switch 1 sends GQ
35 AlliedWare OS How To Note Igmp
Igmp filtering controlling multicast distribution
36 AlliedWare OS How To Note Igmp
Types command
Set switch port=1 igmpfilter=1
Switch 3 is also an Igmp Snooper
37 AlliedWare OS How To Note Igmp
38 AlliedWare OS How To Note Igmp
Received Passed Dropped
39 AlliedWare OS How To Note Igmp
No group memberships
40 AlliedWare OS How To Note Igmp
41 AlliedWare OS How To Note Igmp
42 AlliedWare OS How To Note Igmp
43 AlliedWare OS How To Note Igmp
44 AlliedWare OS How To Note Igmp
45 AlliedWare OS How To Note Igmp
46 AlliedWare OS How To Note Igmp
When we deny groups instead of replacing them
Modify switch 2 Configuration
Group 224.12.13.11 Entry timeout 255 secs Ports 224.12.13.12
47 AlliedWare OS How To Note Igmp
48 AlliedWare OS How To Note Igmp
Static Igmp
Switch 2 is an Igmp Snooper
49 AlliedWare OS How To Note Igmp
50 AlliedWare OS How To Note Igmp
Explanation of Static Igmp
Group Entry timeout Infinity Ports
51 AlliedWare OS How To Note Igmp
52 AlliedWare OS How To Note Igmp
When we add a static entry on another switch
Modify switch 3 Configuration
MulticastPkts 675826
All Groups Entry timeout 247 secs Ports
53 AlliedWare OS How To Note Igmp
54 AlliedWare OS How To Note Igmp
Group Entry timeout Infinity Ports 5,26
55 AlliedWare OS How To Note Igmp
MulticastPkts 14756
56 AlliedWare OS How To Note Igmp
MulticastPkts 36350
57 AlliedWare OS How To Note Igmp
When a static entry’s port goes down
Group Entry timeout Infinity Ports None
58 AlliedWare OS How To Note Igmp
How clients leave groups queries and timers
Querier timer values
Overview of leave process
Snooper timer values
59 AlliedWare OS How To Note Igmp
Consequences for high-loss and high-lag networks
Comparing the Querier and Snooper timers
60 AlliedWare OS How To Note Igmp
Describes the new behaviour
61 AlliedWare OS How To Note Igmp
Igmp fast leave
Switch 1 is an Igmp Querier
62 AlliedWare OS How To Note Igmp
63 AlliedWare OS How To Note Igmp
Explanation of Igmp fast leave
64 AlliedWare OS How To Note Igmp
When fast leave is disabled
Group Entry timeout 2 secs Ports
Fast Leave Off
Group Entry timeout Secs Ports None
When you enable fast leave on switch
It is safe to ignore the group entry on switch
65 AlliedWare OS How To Note Igmp
When you set fast leave on all interfaces
66 AlliedWare OS How To Note Igmp
To specify single mode, use either of the commands
Multiple host mode for fast leave
To specify multiple mode, use the command
67 AlliedWare OS How To Note Igmp
68 AlliedWare OS How To Note Igmp
69 AlliedWare OS How To Note Igmp
Configurable Igmp timers and counters
Timer and counter relationships
70 AlliedWare OS How To Note Igmp
Initial configuration
Each example modifies the following base configuration
Software versions
71 AlliedWare OS How To Note Igmp
Last Member Query Count and Last Member Query Interval
Default values
72 AlliedWare OS How To Note Igmp
What these counters do
73 AlliedWare OS How To Note Igmp
Potential problems with changing these counters
How to change these counters
Last Member Query Interval 255 10secs
74 AlliedWare OS How To Note Igmp
Last Member Query Count
Robustness Variable
Potential problems with changing this counter
How to change this counter
What this counter does
Potential problems with changing this timer
Default Query Interval
What this timer does
How to change this timer
Query Response Interval 100 10secs
77 AlliedWare OS How To Note Igmp
Query Response Interval
78 AlliedWare OS How To Note Igmp
Default Timeout Interval
Synchronisation of timers
Default Timeout Interval = 2*130 + 100/10 = 270 seconds
79 AlliedWare OS How To Note Igmp
80 AlliedWare OS How To Note Igmp
Default Timeout Interval = 2*125 + 100/10 = 260 seconds
Default Timeout Interval 280 Secs
Query Response Interval 200 10secs
Default Timeout Interval 180 Secs
81 AlliedWare OS How To Note Igmp
Default Query Interval 200 Secs Default Timeout Interval 410
82 AlliedWare OS How To Note Igmp
Commands to configure these settings are
Example of bad choices for timer values
Imagine the following changes to the configuration
83 AlliedWare OS How To Note Igmp
Problem 3 Default Timeout Interval too short
Problem 1 Last Member Query Interval too short
Problem 2 Query Response Interval short
Last Member Query Interval was set to 5, using the command
For more information, see Synchronisation of timers on
85 AlliedWare OS How To Note Igmp
86 AlliedWare OS How To Note Igmp
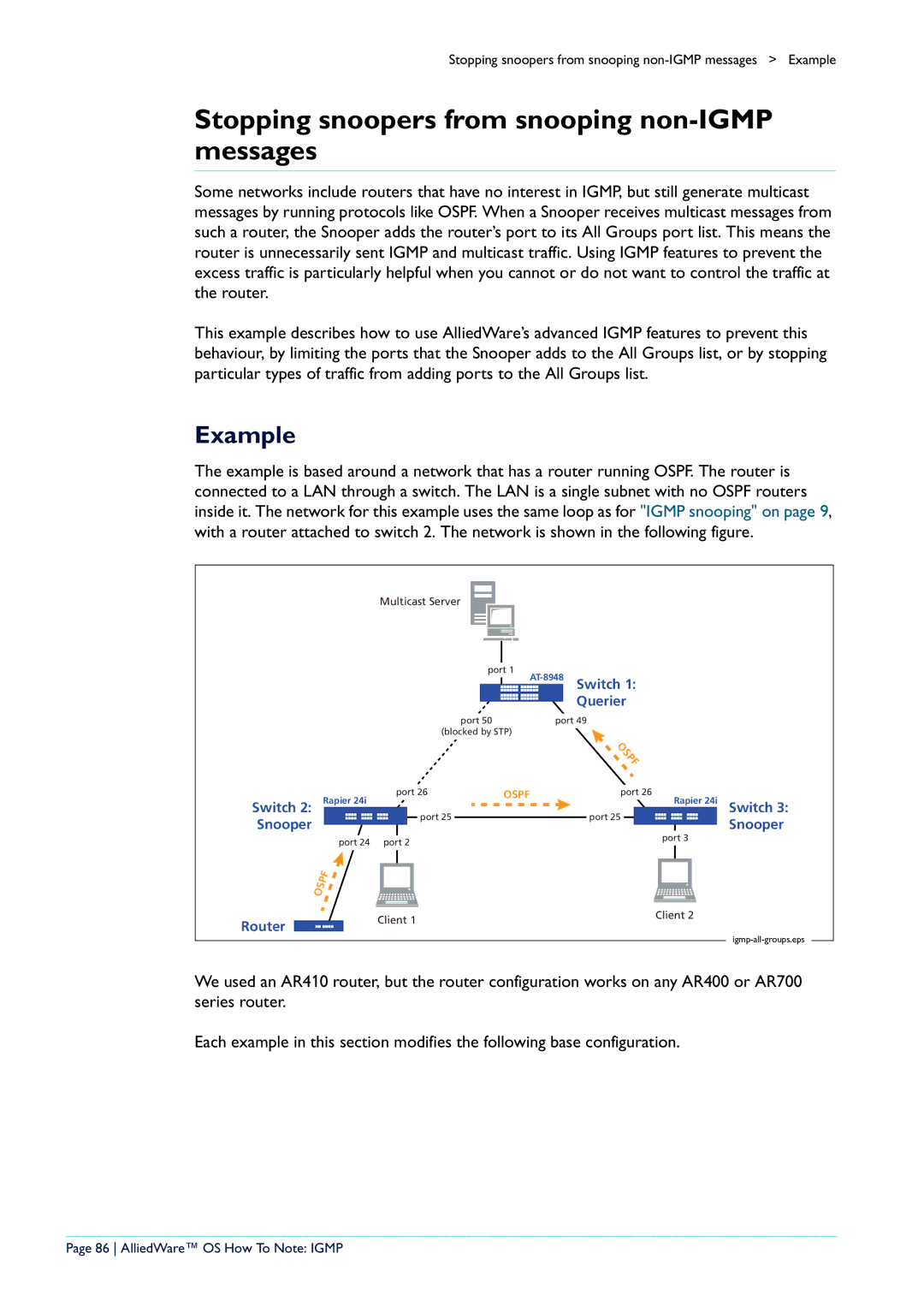
Stopping snoopers from snooping non-IGMP messages
87 AlliedWare OS How To Note Igmp
Router uses Ospf
Configure the router
88 AlliedWare OS How To Note Igmp
Ports 24
89 AlliedWare OS How To Note Igmp
Ports 25
Preventing an All Groups entry for a port
Disabled All-groups Ports
90 AlliedWare OS How To Note Igmp
Disabling All Groups entry for a port
Entry timeout 216 Secs
Check the group entry timeout values
Reset port 24’s packet counters
Enabling All Groups entry again
92 AlliedWare OS How To Note Igmp
Check the group entry timeout values again
Entry timeout Secs
MulticastPkts
93 AlliedWare OS How To Note Igmp
Enable Igmp debugging
Entry timeout 259 Secs
94 AlliedWare OS How To Note Igmp
MulticastPkts 914
95 AlliedWare OS How To Note Igmp
Controlling which addresses create All Groups entries
224.0.0.5
Configuring switch
96 AlliedWare OS How To Note Igmp
97 AlliedWare OS How To Note Igmp
Adding other router addresses
Configuring switches 1
98 AlliedWare OS How To Note Igmp
224.0.0.254
Returning to the default list
99 AlliedWare OS How To Note Igmp
Using the other routermode options
100 AlliedWare OS How To Note Igmp
Check the current Igmp snooping entries
101 AlliedWare OS How To Note Igmp
Statically specifying that a port is a router port
Statically add port 6 as a router port attached to Vlan
To remove the static configuration, simply delete it
102 AlliedWare OS How To Note Igmp
Stop port 6 from being a static router port
Client joins a group
103 AlliedWare OS How To Note Igmp
Igmp debugging
Client leaves a group
IgmpSnoopMembershipQuery setting timer at 2 secs for group
104 AlliedWare OS How To Note Igmp
Several minutes later the group entry times out
Port entry times out
Manager Switch 3 del vlan=100 port=5
105 AlliedWare OS How To Note Igmp
Snooped ports change
Port in the All Groups list is unplugged
106 AlliedWare OS How To Note Igmp
Report is filtered out
107 AlliedWare OS How To Note Igmp
Output for show ip igmp changes
Appendix STP state
Switch
108 AlliedWare OS How To Note Igmp
State Forwarding
109 AlliedWare OS How To Note Igmp
Manager Switch 3 show stp port=25-26