Protecting the user
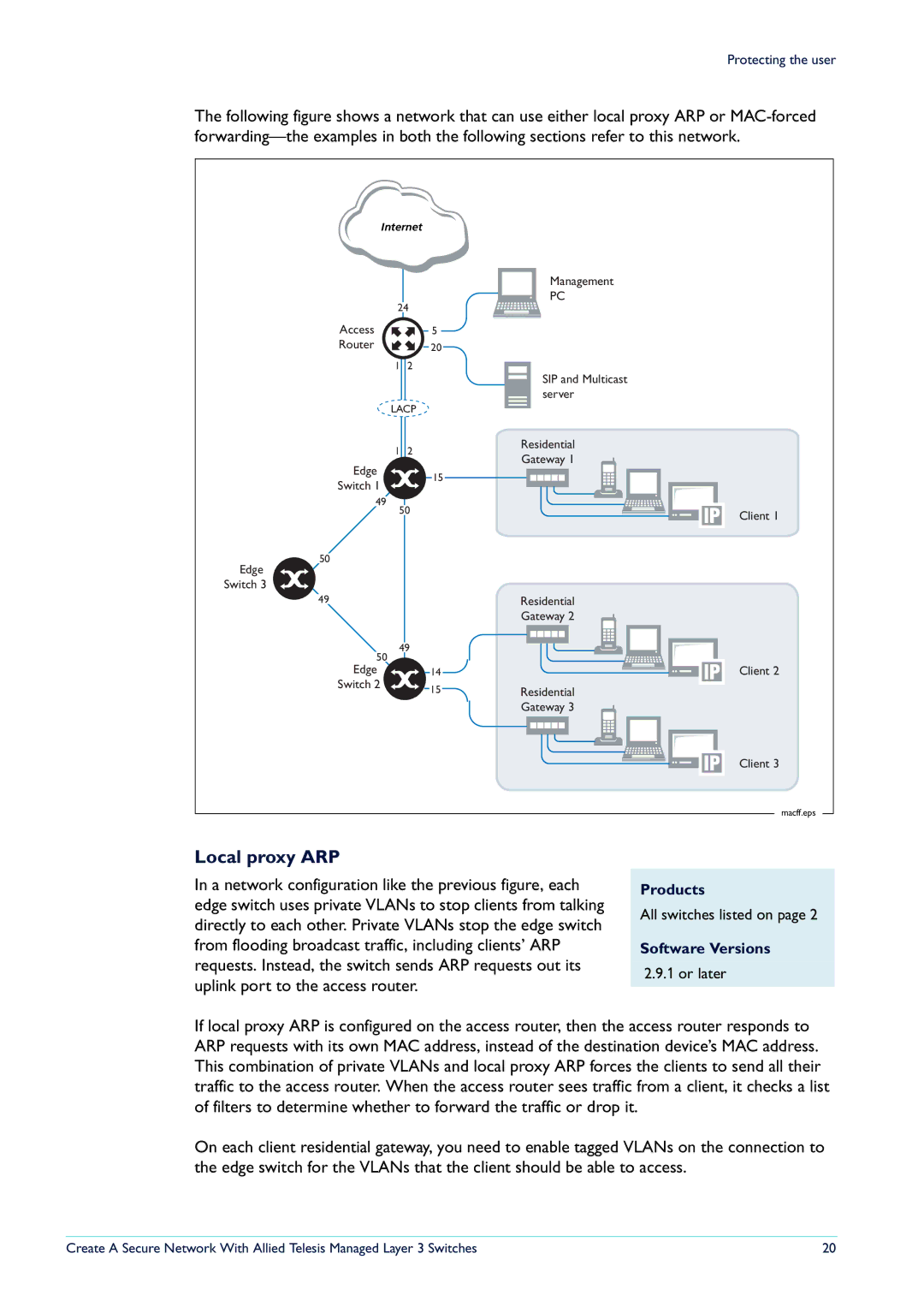
The following figure shows a network that can use either local proxy ARP or
Internet |
| ||
|
| Management | |
24 | PC | ||
| |||
Access | 5 |
| |
Router | 20 |
| |
1 | 2 | SIP and Multicast | |
|
| ||
|
| server | |
LACP |
| ||
1 | 2 | Residential | |
Gateway 1 | |||
Edge |
| ||
15 |
| ||
Switch 1 |
| ||
|
| ||
49 |
|
| |
50 | Client 1 | ||
|
| ||
50 |
|
| |
Edge |
|
| |
Switch 3 |
|
| |
49 |
| Residential | |
|
| Gateway 2 | |
49 |
| ||
50 |
|
| |
Edge | 14 | Client 2 | |
Switch 2 | 15 | Residential | |
| |||
|
| Gateway 3 | |
|
| Client 3 | |
|
| macff.eps | |
Local proxy ARP
In a network configuration like the previous figure, each edge switch uses private VLANs to stop clients from talking directly to each other. Private VLANs stop the edge switch from flooding broadcast traffic, including clients’ ARP requests. Instead, the switch sends ARP requests out its uplink port to the access router.
Products
All switches listed on page 2
Software Versions
2.9.1 or later
If local proxy ARP is configured on the access router, then the access router responds to ARP requests with its own MAC address, instead of the destination device’s MAC address. This combination of private VLANs and local proxy ARP forces the clients to send all their traffic to the access router. When the access router sees traffic from a client, it checks a list of filters to determine whether to forward the traffic or drop it.
On each client residential gateway, you need to enable tagged VLANs on the connection to the edge switch for the VLANs that the client should be able to access.
Create A Secure Network With Allied Telesis Managed Layer 3 Switches | 20 |