Using the Web-Based Advanced User Interface
Table of Contents | sections | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
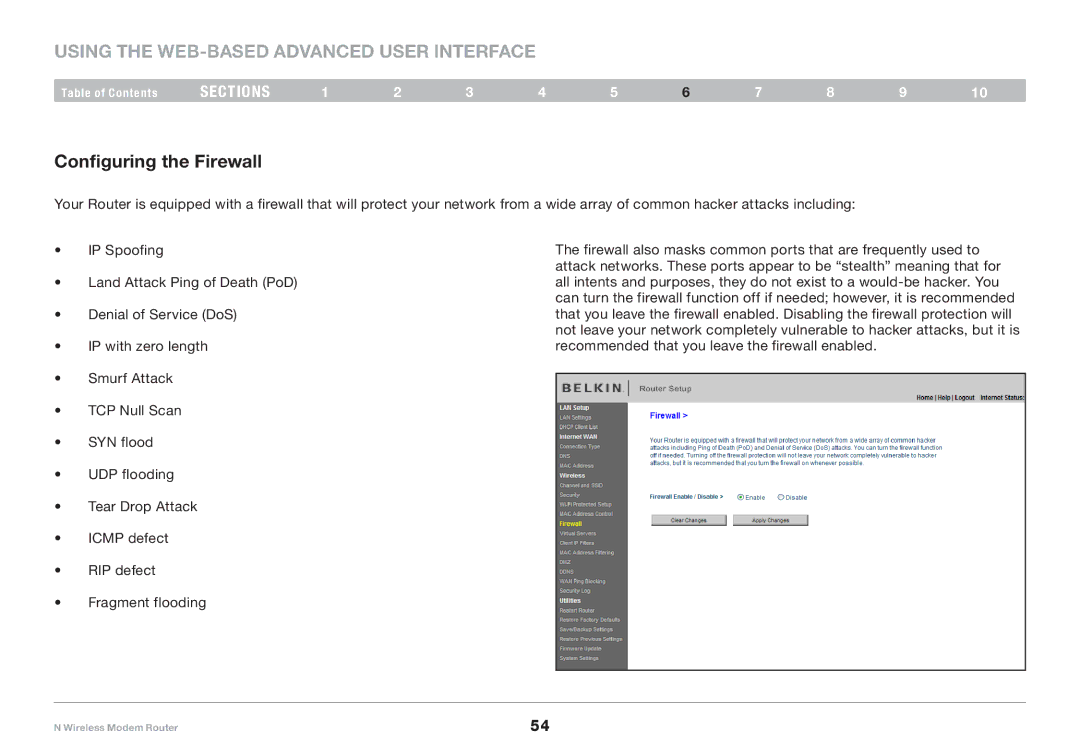
Configuring the Firewall
Your Router is equipped with a firewall that will protect your network from a wide array of common hacker attacks including:
• | IP Spoofing | The firewall also masks common ports that are frequently used to |
|
| attack networks.. These ports appear to be “stealth” meaning that for |
• | Land Attack Ping of Death (PoD) | all intents and purposes, they do not exist to a |
|
| can turn the firewall function off if needed; however, it is recommended |
• | Denial of Service (DoS) | that you leave the firewall enabled.. Disabling the firewall protection will |
|
| not leave your network completely vulnerable to hacker attacks, but it is |
• | IP with zero length | recommended that you leave the firewall enabled.. |
•Smurf Attack
•TCP Null Scan
•SYN flood
•UDP flooding
•Tear Drop Attack
•ICMP defect
•RIP defect
•Fragment flooding
N Wireless Modem Router | 54 |