VoIP/(802.11g) ADSL2+ (VPN) Firewall Router
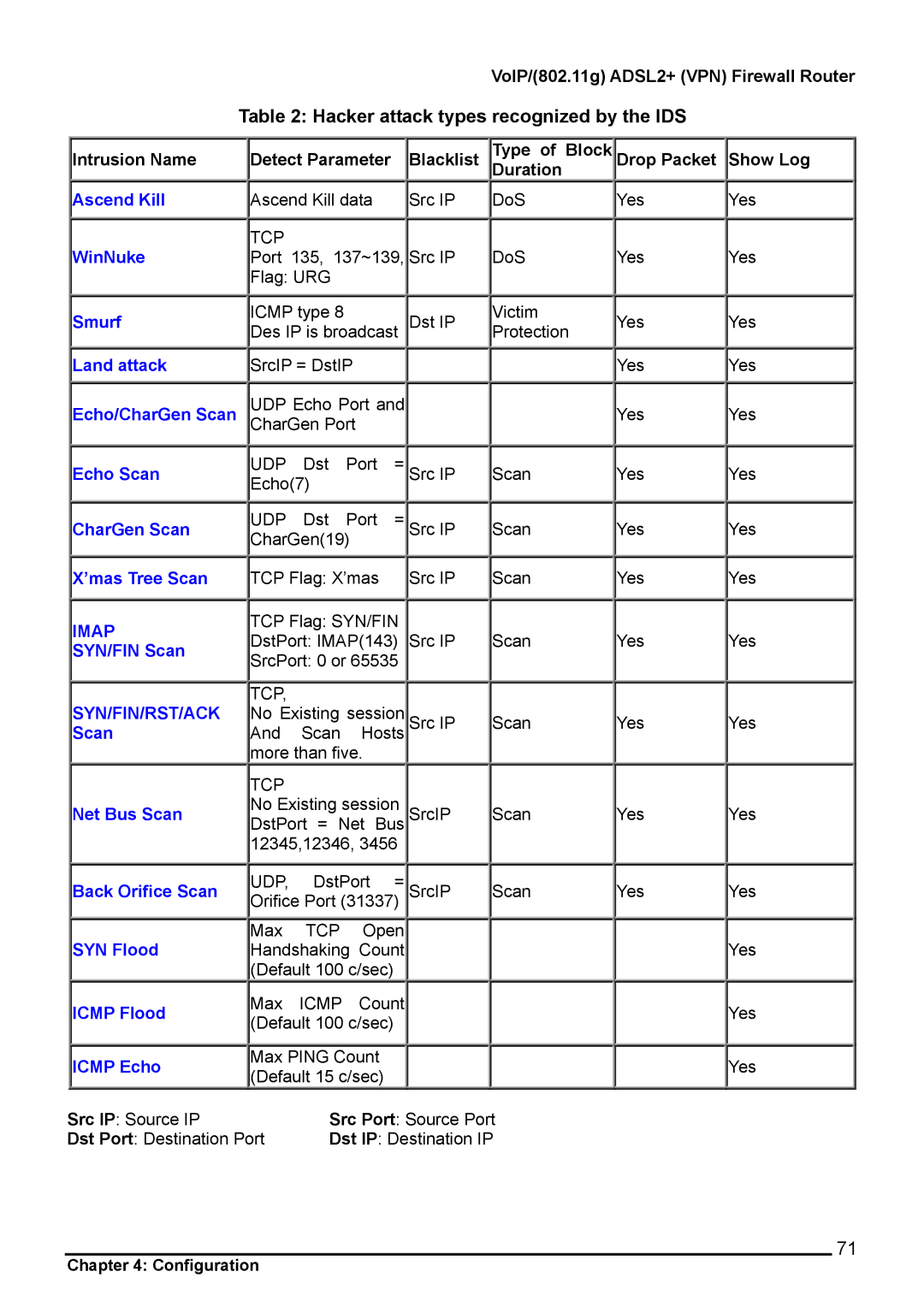
Table 2: Hacker attack types recognized by the IDS
Intrusion Name
Ascend Kill
WinNuke
Smurf
Land attack
Echo/CharGen Scan
Echo Scan
CharGen Scan
X’mas Tree Scan
IMAP
SYN/FIN Scan
SYN/FIN/RST/ACK Scan
Net Bus Scan
Back Orifice Scan
SYN Flood
Detect Parameter |
| Blacklist | Type of Block | Drop Packet | ||
|
|
|
|
| Duration |
|
Ascend Kill data |
| Src IP | DoS | Yes | ||
|
|
|
|
|
|
|
TCP |
|
|
| Src IP | DoS | Yes |
Port 135, 137~139, | ||||||
Flag: URG |
|
|
|
|
| |
ICMP type 8 |
|
| Dst IP | Victim | Yes | |
Des IP is broadcast | Protection | |||||
SrcIP = DstIP |
|
|
| Yes | ||
UDP Echo Port and |
|
| Yes | |||
CharGen Port |
|
|
| |||
|
|
|
| |||
|
|
|
|
|
|
|
UDP | Dst | Port | = | Src IP | Scan | Yes |
Echo(7) |
|
|
|
|
| |
UDP | Dst | Port | = | Src IP | Scan | Yes |
CharGen(19) |
|
|
|
| ||
TCP Flag: X’mas |
| Src IP | Scan | Yes | ||
|
|
|
| |||
TCP Flag: SYN/FIN | Src IP | Scan | Yes | |||
DstPort: IMAP(143) | ||||||
SrcPort: 0 or 65535 |
|
|
| |||
|
|
|
|
|
|
|
TCP, |
|
|
|
|
|
|
No Existing session | Src IP | Scan | Yes | |||
And | Scan | Hosts |
|
|
| |
more than five. |
|
|
|
| ||
TCP |
|
|
|
|
|
|
No Existing session | SrcIP | Scan | Yes | |||
DstPort = Net Bus |
|
|
| |||
12345,12346, 3456 |
|
|
| |||
|
|
|
|
|
| |
UDP, | DstPort | = | SrcIP | Scan | Yes | |
Orifice Port (31337) |
|
|
| |||
Max | TCP | Open |
|
|
| |
Handshaking Count |
|
|
| |||
(Default 100 c/sec) |
|
|
|
| ||

 Show Log
Show Log
![]()
![]() Yes
Yes
Yes
![]()
![]() Yes
Yes
![]()
![]() Yes
Yes
Yes
Yes
Yes
![]()
![]() Yes
Yes
Yes
Yes
Yes
Yes
Yes
ICMP Flood
 ICMP Echo
ICMP Echo
Max ICMP Count (Default 100 c/sec)
Max PING Count (Default 15 c/sec)
Yes
![]()
![]() Yes
Yes
Src IP: Source IP | Src Port: Source Port |
Dst Port: Destination Port | Dst IP: Destination IP |
71
Chapter 4: Configuration