B.5 | Competitor’s Claims for NFS |
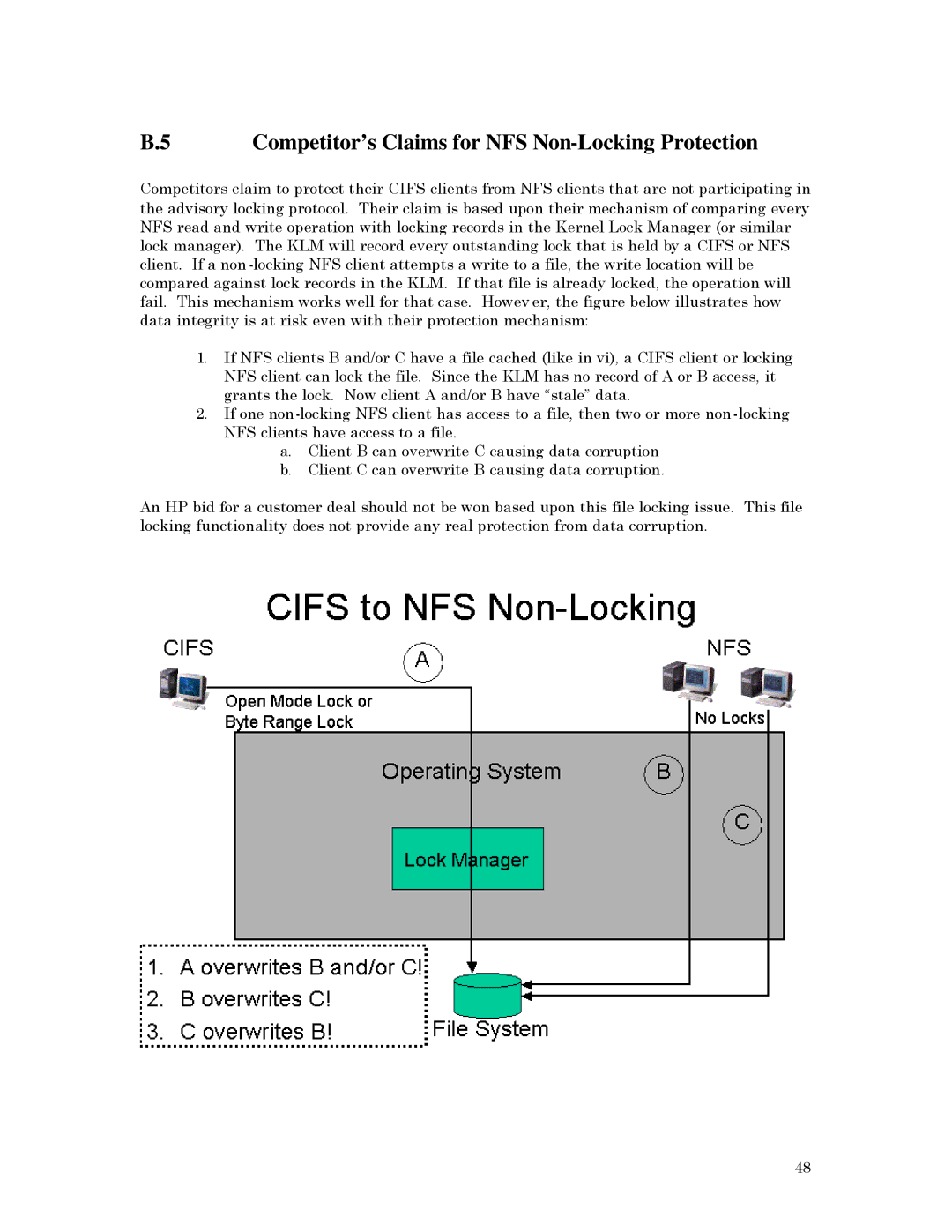
Competitors claim to protect their CIFS clients from NFS clients that are not participating in the advisory locking protocol. Their claim is based upon their mechanism of comparing every NFS read and write operation with locking records in the Kernel Lock Manager (or similar lock manager). The KLM will record every outstanding lock that is held by a CIFS or NFS client. If a non
1.If NFS clients B and/or C have a file cached (like in vi), a CIFS client or locking NFS client can lock the file. Since the KLM has no record of A or B access, it grants the lock. Now client A and/or B have “stale” data.
2.If one
a.Client B can overwrite C causing data corruption
b.Client C can overwrite B causing data corruption.
An HP bid for a customer deal should not be won based upon this file locking issue. This file locking functionality does not provide any real protection from data corruption.
48