Wireless-B Ethernet Bridge
The solution, then, is to segment your network up into multiple groups. If your network had 80 users and you used four WEP keys, a hacker would have access to only ¼ of your wireless network resources. In this way, multiple keys reduce your liability.
Finally, be sure to change your WEP key regularly, once a week or once a day. Using a “dynamic” WEP key, rather than one that is static, makes it even harder for a hacker to break into your network and steal your resources.
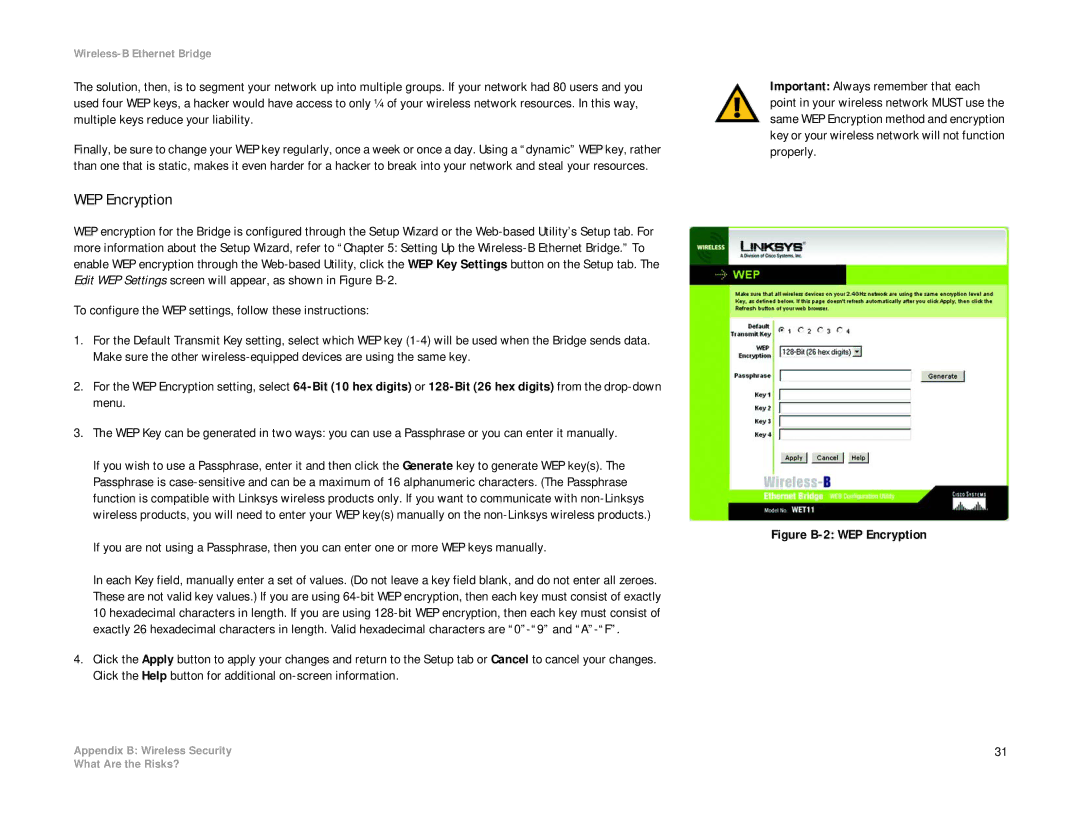
WEP Encryption
WEP encryption for the Bridge is configured through the Setup Wizard or the
To configure the WEP settings, follow these instructions:
1.For the Default Transmit Key setting, select which WEP key
2.For the WEP Encryption setting, select
3.The WEP Key can be generated in two ways: you can use a Passphrase or you can enter it manually.
If you wish to use a Passphrase, enter it and then click the Generate key to generate WEP key(s). The Passphrase is
If you are not using a Passphrase, then you can enter one or more WEP keys manually.
In each Key field, manually enter a set of values. (Do not leave a key field blank, and do not enter all zeroes. These are not valid key values.) If you are using
4.Click the Apply button to apply your changes and return to the Setup tab or Cancel to cancel your changes. Click the Help button for additional
Appendix B: Wireless Security
Important: Always remember that each point in your wireless network MUST use the same WEP Encryption method and encryption key or your wireless network will not function properly.
Figure B-2: WEP Encryption
31
What Are the Risks?