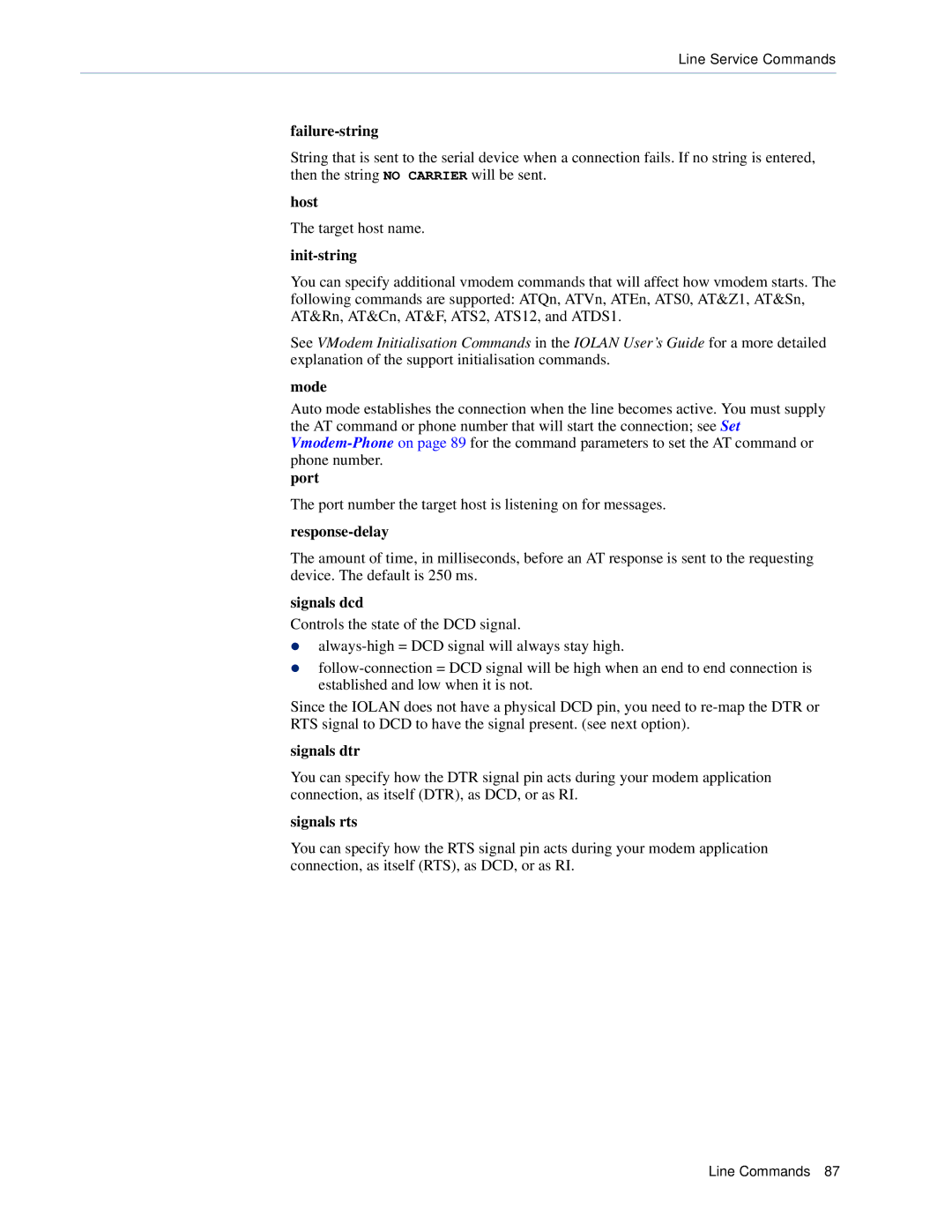
CSS specifications
Perle Systems, a well-established provider of networking and IoT solutions, offers the innovative Perle CSS (ClearSky Services) platform, designed to facilitate efficient and secure device management. This powerful solution aims to address the challenges of managing a diverse range of devices connected to the Internet, particularly in enterprise, industrial, and M2M (Machine-to-Machine) environments.One of the main features of the Perle CSS is its robust device management capabilities. Administrators can remotely monitor, configure, and control devices in real-time. This means that troubleshooting can be conducted without the need for physical access, significantly reducing operational downtime. Additionally, the platform supports bulk provisioning, allowing organizations to onboard multiple devices simultaneously, which streamlines the deployment process.
Another notable feature is its security architecture. Perle Systems has integrated advanced security protocols to ensure the integrity and confidentiality of data transmitted between devices. The use of virtual private networks (VPNs), secure socket layer (SSL) encryption, and secure shell (SSH) protocols ensures that sensitive information remains protected from unauthorized access while in transit.
The Perle CSS also stands out for its compatibility with various communication protocols, including MQTT, RESTful APIs, and others. This interoperability allows organizations to integrate the CSS platform seamlessly with their existing systems, facilitating efficient data exchange and interoperability between different devices and applications.
Moreover, Perle CSS adopts a cloud-based architecture, which provides users with the flexibility to access device information from any location. This cloud integration enhances scalability, allowing businesses to expand their network capabilities without the need for extensive infrastructure investments.
The platform's user-friendly interface simplifies navigation, allowing users to manage devices effectively without requiring extensive technical expertise. With customizable dashboards and real-time analytics, administrators can gain valuable insights into device performance, network status, and usage patterns.
In summary, Perle Systems' CSS offers a comprehensive solution for managing connected devices in a secure and efficient manner. Its key features, including robust device management, advanced security, protocol compatibility, and a cloud-based architecture make it an ideal choice for enterprises looking to enhance their IoT capabilities and streamline operations in an increasingly connected world.