Atlantis Land I-STORM ADSL ROUTER
Active: Choose “Yes” to enable the rule, or choose “No” to disable the rule.
Packet Type: Specify the packet type (TCP, UDP, ICMP or any) that the rule will be applied to.
Select TCP if you want to scope for the
Log: Choose “Yes” if you want to generate logs when the filer rule is applied to a packet.
Action When Matched: If any packet matches this filter rule, forward or drop this packet.
Source IP Address: Enter the incoming or outgoing packet’s source IP address.
Source IP Mask: Enter the incoming or outgoing packet’s source IP Subnet Mask.
Source Port: Check the TCP or UDP packet’s source port number(s).
Destination IP Address: Enter the incoming or outgoing packet’s destination IP address.
Destination IP Mask: Enter the incoming or outgoing packet’s destination IP Subnet Mask.
Destination Port: Check the TCP or UDP packet’s destination port number(s).
If the DHCP server option is enabled, you have to be very careful in assigning the IP addresses of filtered private IP range in order to avoid conflicts. Because you do not know which PC in LAN is assigned to which IP address. The easy way is that the filtered IP address is assigned to the specific PC that you do not want this PC to access outside resource such as Internet. You configure the filtered IP address manually to this PC, but it is still in the same subnet with the router.
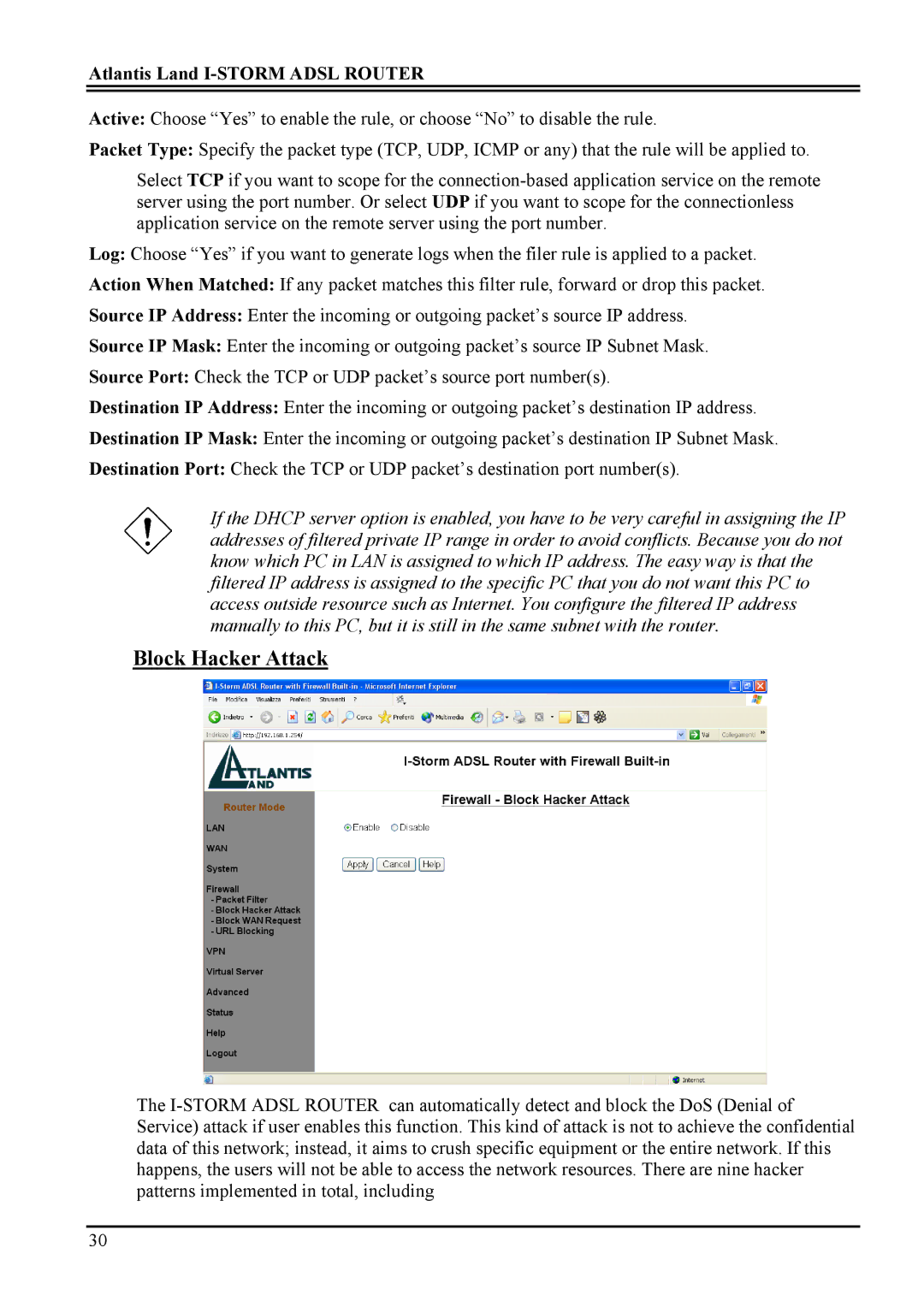
Block Hacker Attack
The
30