Page
Copyright Notice
Barracuda NG Network Access Client
VPN Configuration
Update or Migration
Uninstall
VPN Component Configuration
Warranty and Software License Agreement
Pre-Connector and Remote VPN
Example Configuration
802.1X Technical Guideline
Endpoint Security and Network Access Control
Introduction to Barracuda NG Network Access Client
Introduction
Client software consists of the following subsystems
Barracuda NG Personal Firewall
What can Barracuda NG Network Access Client be used for?
1Barracuda NG Network Access Client environment
Barracuda NG Network Access Client Administrator’s Guide
Healthy Limited Access VPN Offline
What is a Policy Rule Set?
Policy Matching Procedure
Licensing Aspects
Barracuda NG Network Access Client Administrator’s Guide
Healthy
Probation actions
Local Machine context
Current User context
VPN context
Health Matching
Matching Criteria Local Machine Current User
Health State Healthy
Health State Untrusted
Health State Probation
Health State Unhealthy
Health State Requirements
Border Patrol
Analyse Enforce Monitor
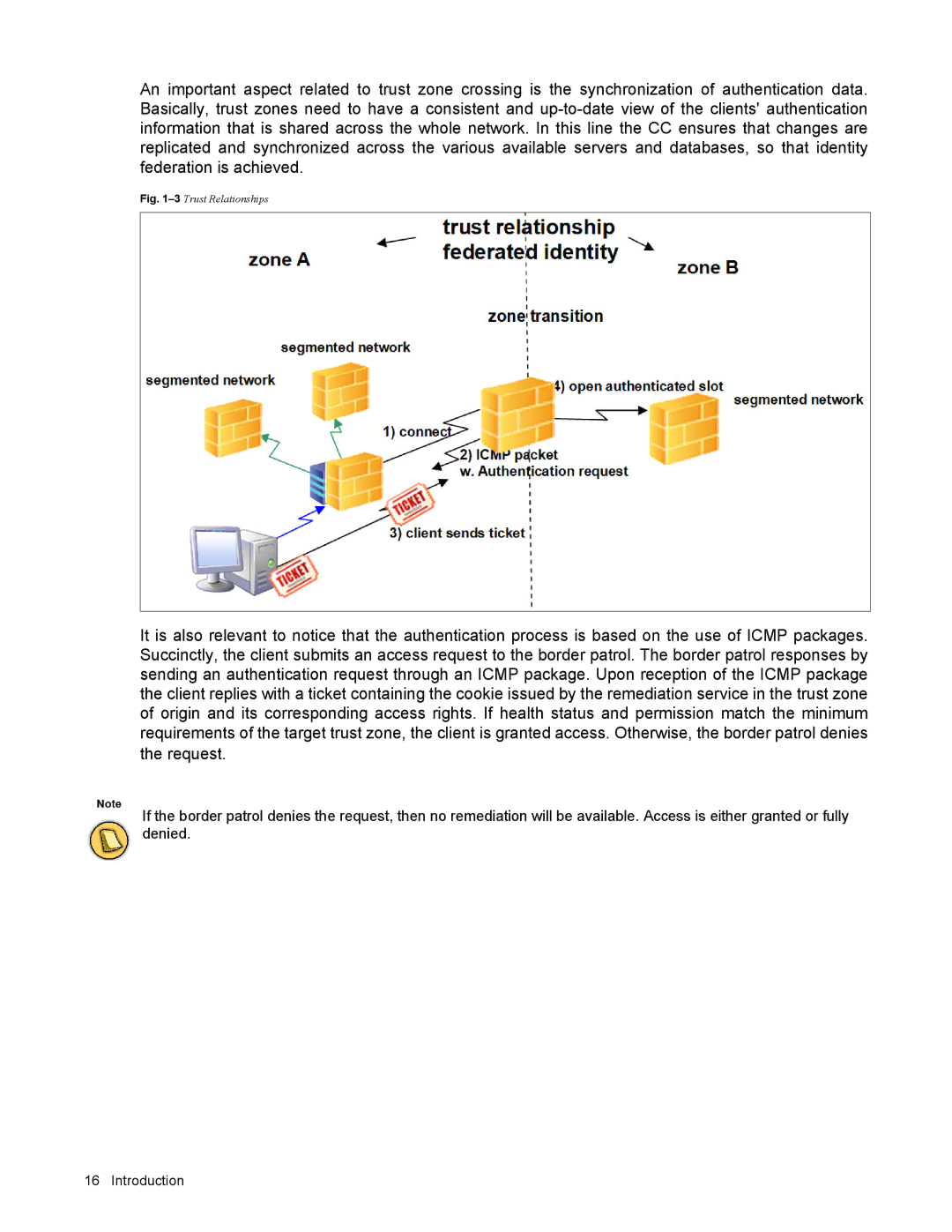
3Trust Relationships
General
Server Config Access Control Service
Access Control Service Settings
System Health Validator
ParameterDescription
Remediation Service
Trustzone-Border
Advanced
Log Level
Number of used Threads
Access Control Objects
General
Welcome Messages
Pictures
3Access Control Objects Access Control Service Bitmaps
Personal Firewall Rules
Click clipboard, import the adequate registry file
Registry Check Objects
Import of a registry file
Access Control Service Trustzone
7Access Control Service Trustzone Configuration tree
Servername Assigned Services servicename ACS
9Access Control Service Trustzone Rules
Rules
Client Connection External Ignore Internal
Policy Name
Deactivate Policy
Time Restriction
Policy Matching All-of-following One-of-following
Net Bios
User Login
Group Patterns
X509 Subject
X509 Issuer
Microsoft
X509
Required Health State Basic
Antispyware Required Scanner On
Tries to execute a full system scan automatically
AS Engine Required Ignore Latest default Previous Last-2
Last AV Scan Action Manual Auto Remediation
Last AS Scan Action Manual Auto Remediation
Update automatically
AV Engine/Pattern Manual Action Auto Remediation
Parameter Description
Server
Personal Ruleset Name Firewall Settings
Software Yes Update No default Required Yes-Even-Major
Message
Use Dhcp renew
Settings
802.1X Use
Healthy Vlan Id
Limited Access
Ruleset Name Limited Access Message
Bitmap
Passport Verification Key
Health Passport
Verification Key
802.1X
Support Chart
Server Config Personal Firewall Rules
Rule Set Name Tab
Double-click the appropriate VPN Firewall Rule Set
1Rules Incoming
Rules Incoming / Outgoing
Copy
New…
Delete
Paste
Comment
Select New… from the context menu to create a new rule
Item / Parameter Description
Inactive
Section Description
Tester view allows testing rule sets for consistency
Tester
Following entities are available for rule testing
Test Report
Options
Connect to the Internet
Port Protocol Service Name Description
Icmp Parameters
With Adsl Pptp
Listing is divided into the following columns
Preconfigured
Adapters
Following objects assigned with status multi are available
Following further adapter objects are available
Name Specify a name for the adapter object
IPs
Trust Type
Status
Adapter/Ref
User Objects
10User Object dialog
Net Objects
11Network Objects window
This object includes the Multicast network 239.255.0.0/16
Click New… to open the Net Object dialog
12Net Object dialog
Service Objects
13Service Object dialog
Service Name Port Protocol Connection Description
Application Objects
Kerberos
14Application Object dialog
HKEYLOCALMACHINE\Services registry key
Application Connection Description
Operating & Monitoring Barracuda NG NAC
Box Monitoring and Real-time Information
Available Columns
Name of the matching policy rule
Possible values are Access, Not Restricted, or Probation
Filtering
Clients MAC address as reported by the NG client
Context Menus
Visualize this Computer…
Status Tab
3Box Monitoring and Real-time Information Show time in UTC
Access Tab
Status VPN Tab
Quarantine Tab
Client Installation
Double-click setup.exe to start the installation routine
Installation routine offers three basic ways of setup
Complete Installation
See 5.3 Unattended Setup,
See 5.4 Customer Setup,
Parameter Default
Custom Installation
Unattended Setup
802.1x Enable Dhcp Renew
See description for parameter Trusted Network,
See description for parameter Windows File Sharing,
This parameter defines the Access Control Server to be used
This option prevents deactivating the NG Personal Firewall
Customer.inf
Customer Setup
Proceed as follows to prepare a completely customized setup
See 5.4.1 customer.inf,
Optionally, the following file-directives may be detailed
Directive Comment
0x00000010
0x00000800
0x00000008
0x00001000
Value-entry-name
Reg-root
Subkey
Flags
Edit profile name
Diskid
Silent.cmd
Filename
Subdir
For an overview of specific properties see -1,
System Restore
Refer to the OS help for details
Update or Migration
Uninstall
Procedure
VPN Configuration
Overview
Facts and Figures
Function Supported
Function Comment
Usage Scenario
Architecture
All Programs Barracuda NG Network Access Client NG Firewall
Barracuda NG Personal Firewall
Integration within Windows
1Windows 7 Windows Firewall and Action Center screens
Rule Set Selection
2Rule set selection
User Interface
3Graphical Interface of the Barracuda NG Personal Firewall
General Firewall Settings and Tasks Menu Bar
Firewall Menu
Automatic Adapter Assignment
This tab allows you to configure blocking of Icmp packets
Disable Windows Firewall
Block all IP Fragments
View Menu
Connect Close Block
Security Mode Menu
Load Display
NG Control Center Monitoring Firewall Activities
Summary
Events
History
11NG Control Center History window
Send to Rule Tester
Show Details
Resolve Source/Destination IP
Add Pass Rule
Filters the application which has attempted to connect
Filters the connection’s Traffic Policy
Filters the source IP address of the connection
Filters incoming or outgoing connections
Live Activity
Live Activity view details all currently active connections
Disconnect
Filter Conditions
Current State Setting the Security Mode
Configuration
Show Adapters
Show Source Addresses…
Show Destination Addresses…
Show Users
ItemDescription
Paste Pastes the selected rules from the clipboard
Source / Destination
Action Name Comment
Inactive checkbox Select
Application optional
Monitor Connections Yes
18Time restriction dialog
Adapters
19Adapter objects window
Network Connection name for example, Local Area Connection
Control Network Connections
Networks
Following options are available
Untrusted
Secured Routes are assigned to the Net-NGVPNObject
Services
22Net Object dialog
Example
Applications
24Application Object dialog
10Applications required in Microsoft Windows domains
Users
25User Object dialog
Rule Tester view allows testing rule sets for consistency
Rule Tester
Test Reports
27Test Report window
Administration Firewall Settings Wizard
Following options are available for customisation
Automatic Adapter Configuration
However, it will not pop up if
Automatic Rule Configuration
28Security Alert windows
29Security Alert Advanced Policy
Restrictive rule set only
VPN Component Configuration
Create a New Profile Using the Profile Wizard
2VPN Profile Wizard Profile Wizard
4VPN Profile Wizard Enter personal License
Configure a New Profile Manually
6VPN Profile Wizard Modify Existing Profile Using the Wizard
8NG VPN client Connect dialog
Field where characters need to be inserted
Shows the version information
11Editing options of the VPN client dialog
Barracuda NG VPN Client’s Menu Bar
13Close NG VPN Client informational window
Connection Dialog
Closes the NG VPN Client window
NG VPN Client can be started in the following ways
Click Connect to establish a connection to the VPN server
Assigned DNS IP address for the VPN connection
Status Dialog
Assigned domain
Assigned Wins address
VPN server to which the client currently is connected
Enable or disable compression
Uptime for the current connection
Local time on the VPN server
Message Dialog
16Message dialog window
Barracuda Networks Control / Preferences Dialog
VPN Profiles Configuration Window
Configured VPN server to connect to
Name of the profile
Modify, copy or delete an existing profile
Certification Authorities Configuration Window
Store into which the certificate was saved
Use this menu item to terminate a connection
Configure specific Barracuda NG VPN adapter settings here
Opens a window with detailed certificate information
Deletes the selected certificate from the certificate store
General VPN Settings section Direct Access
Connection Entries Tab
19Connection Entries tab
Barracuda Authentication
Following parameters are available for X509 authentication
Advanced Settings Tab
DescriptionDescription
External File Path to the external X.509 certificate
Use Access Control Service
Virtual Adapter Configuration
Default Direct assignment
Default Yes
Fallback Profile
Disconnecting. Recommended value No
Enable MS Logon
Be established
User name possibly needed for proxy authentication
IP address of the VPN server
URL or IP address of the proxy server
Log Window
Log entry’s time stamp
Module the respective log entry refers to
Barracuda NG Access Monitor
Access Monitor
Port Security
Monitoring
Health Agent
Property Description
Advanced Status information
State Description
5Connection error using Icmp connectivity checking see
Barracuda NG Network Access Client Administrator’s Guide
11.2.6 802.1X Authentication Port Security
Task Description
Column Description
EAP Tracer
Use Basic Authentication
Access Control Server IPs from Registry
Access Control Server IPs from Dhcp
Use Ntml Authentication
Health Agent Connectivity
Item Description
Key
Value
Health Agent Authentication
11.3.9 802.1X Settings
Ieee 802.1X Authentication
Capture 802.1X Traffic EAP
Log Settings
Log Files
16 Log Files Description
Download.xml
Client.xml
Connect.xml
DownloadLocal.xml
Pre-Connector and Remote VPN
VPN Connector
Create a connector to achieve following
Creating a Connector
Thereafter rename the default profile
Remote VPN rvpn
Remote Domain Logon Pre-Logon
Connection Procedure
Same example with 10 retries for connecting -c
Dhcp
Example Configuration
1Example configuration environment
Introduce Access Control Objects
Personal Firewall Rule Set
Introduce an Access Control Service Trustzone
Next create and edit the unrestricted rule set
Page
Configure an Access Control Service Trustzone
Policy Rule dialog is split up into these views
Barracuda NG Network Access Client Administrator’s Guide
Parameter Value
Page
Example Configuration
Configure Forwarding Firewall Rule Set
Example Configuration
802.1X Technical Guideline
Switch
Authentication Server
Client computer
Status Monitoring
Access Control Server
Disabled Enabled
EAP Packet Tracer
Log Files on the Client Computer
Using the Barracuda NG Access Monitor for Analysis
Command Description
Supplicant console interface
Key Logging
Switch Web Interface
These values are described in more details on
Path
See 14.3.9 Periodic client re-authentication by the switch,
See 14.3.11 Authentication Message Exchange,
Example enabling debug output
Authentication
Switch Console Interface
Ethernet
Token Ring
Operational Sequence
Start up
Point-to-Point
Service Friendly Name Service Name
WZO prior to Windows Vista
Dot3svc Windows Vista
Wpa-supplicant configuration
You will require elevated privileges to perform this step
To resolve this problem proceed following steps
Runtime
Successful start of the wpa-supplicant can be verified by
Enter global configuration mode
Return to privileged Exec mode
Verify your entries
Re-authentication started by the switch is illustrated
Example
See for the Eapol packet frames
Command
Enter the global configuration mode
Condition Description
Return to the privileged Exec mode
Dhcp Renew
Resetting the 802.1X Authentication process
Shutdown
14 phions.log Output
15 phions.log Output
WPA Supplicant Log File Identifiers
Addendum
Packets
Table shows an Eapol packet frame
200 802.1X Technical Guideline
Sending / receiving commands over pipe
202 802.1X Technical Guideline
Engineering Environment
Known Issues using Cisco Catalyst 3750-E Switch
Wireshark
Additionally following tools have been used for analysis
No aaa accounting dot1x default group radius
Customer Install Files
Appendix
Appendix
Barracuda NG Network Access Client Administrator’s Guide
Appendix
VPN Profile Registry Keys
VPN Profile Registry Keys
3DES AES
FAQs
Profile Registry Keys
Appendix
Configuration Parameters
214
Reconnect immidiately 10
X509 Altnames 2 X509 Issuer 2 X509 Subject 2
Introduction Server Config Access Control Service
15.6 Parameter Lists
Barracuda NG Access Monitor
Figures
220
802.1X Technical Guideline
Barracuda Networks Limited Hardware Warranty
Barracuda Networks Software License Agreement
Barracuda Networks Warranty and Software License Agreement
Page
Barracuda Networks Software License Agreement Appendix
Page
Page
No Warranty
Terms and Conditions
Page
Page
Page
Page
Limitation of Liability
Page
Page
Page
238
Page
Page
Page
Page
Disclaimer of Warranty
Miscellaneous
Page
Limits
Terms and Conditions for USE, REPRODUCTION, and Distribution
Page
Page
Page
Page
252
Page
Page
Barracuda Networks Warranty and Software License Agreement
Page
Barracuda Networks Warranty and Software License Agreement
Page
Barracuda Networks Warranty and Software License Agreement
Page
Page
Issue Date Aug 6 262
Page
264