SEHI-22/24, SEHI-32/34 specifications
Cabletron Systems was a notable player in the networking hardware market during the rise of local area networks (LANs) in the late 20th century. Among its innovative products were the SEHI-22/24 and SEHI-32/34 modules, which were designed to enhance network capabilities in enterprise environments.The SEHI-22/24 and SEHI-32/34 were versatile high-performance Ethernet switch modules that offered significant advantages in network management and connectivity. These modules were designed to work with Cabletron's modular switching and routing architecture, allowing for scalable solutions tailored to specific network demands. A key feature of the SEHI series was its support for a range of Ethernet standards, ensuring compatibility with diverse networking environments.
One notable characteristic of the SEHI-22/24 was its ability to support both 10Base-T and 100Base-TX Ethernet technologies. This dual support enabled organizations to leverage existing 10 Mbps infrastructure while facilitating upgrades to 100 Mbps speeds without needing a complete overhaul of the network. Similarly, the SEHI-32/34 offered even greater connectivity options, accommodating more users and devices while maintaining high throughput and low latency.
In terms of management features, the SEHI series was equipped with extensive traffic management capabilities, including Quality of Service (QoS) features that prioritized bandwidth for critical applications. This ensured that essential services such as voice over IP (VoIP) and video conferencing could function optimally, even during heavy network loads.
Furthermore, both modules featured advanced diagnostics and monitoring tools that provided network administrators with critical insights into traffic patterns and potential bottlenecks. This functionality was essential for maintaining network health and optimizing performance, especially in dynamic business environments.
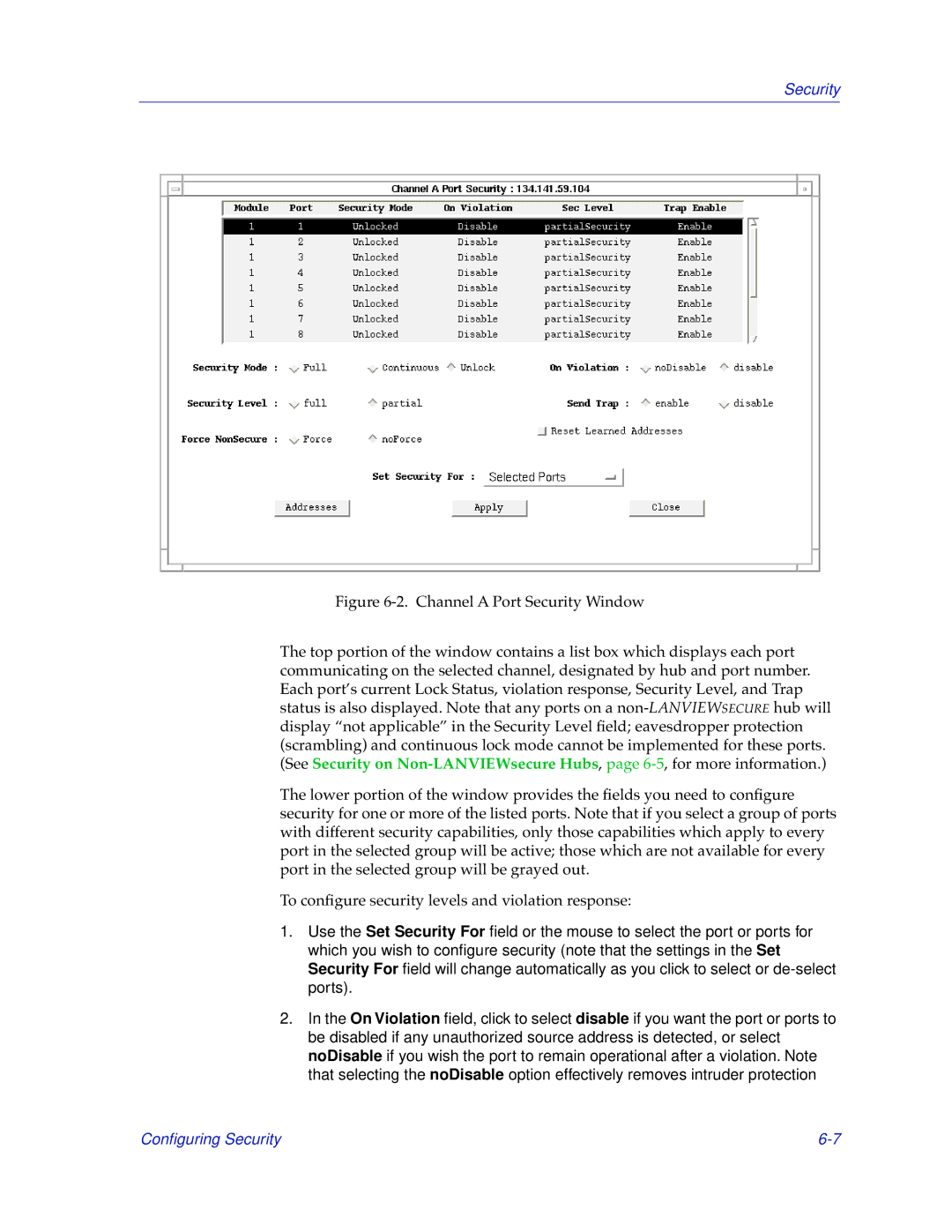
Security also played a crucial role in the design of the SEHI-22/24 and SEHI-32/34. The modules incorporated support for various authentication methods and access controls, ensuring that sensitive data remained protected within the corporate network.
In summary, Cabletron Systems’ SEHI-22/24 and SEHI-32/34 offered significant advancements in Ethernet switching technology, allowing organizations to build robust, scalable, and secure networks. With their impressive features, compatibility, and capacity for management and security, these modules were instrumental in shaping reliable networking solutions for enterprises navigating the rapidly evolving digital landscape.