Getting Fiberlink MaaS360 Ready for ISE
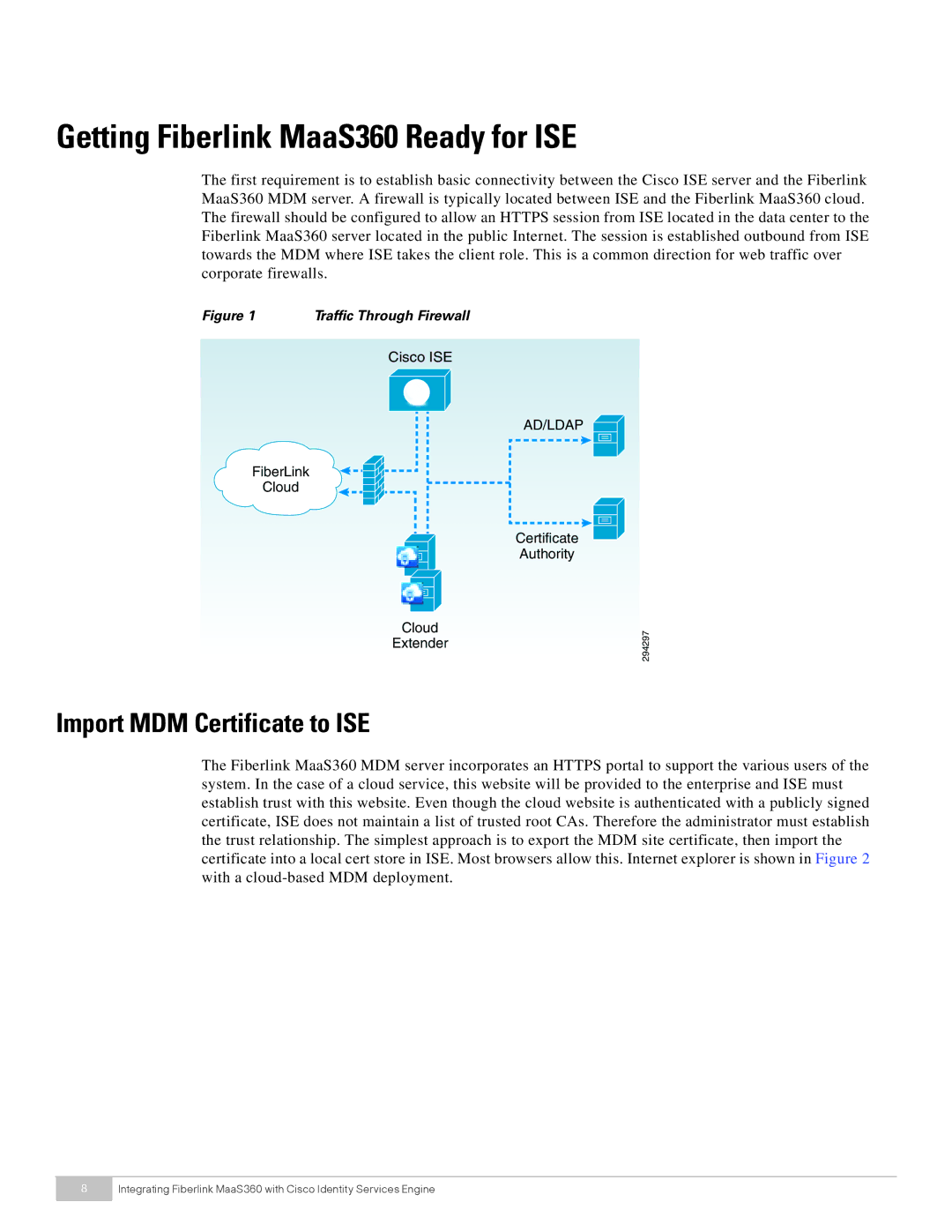
The first requirement is to establish basic connectivity between the Cisco ISE server and the Fiberlink MaaS360 MDM server. A firewall is typically located between ISE and the Fiberlink MaaS360 cloud. The firewall should be configured to allow an HTTPS session from ISE located in the data center to the Fiberlink MaaS360 server located in the public Internet. The session is established outbound from ISE towards the MDM where ISE takes the client role. This is a common direction for web traffic over corporate firewalls.
Figure 1 | Traffic Through Firewall |
Cisco ISE
AD/LDAP
FiberLink
Cloud
Certificate
Authority
Cloud
Extender
294297
Import MDM Certificate to ISE
The Fiberlink MaaS360 MDM server incorporates an HTTPS portal to support the various users of the system. In the case of a cloud service, this website will be provided to the enterprise and ISE must establish trust with this website. Even though the cloud website is authenticated with a publicly signed certificate, ISE does not maintain a list of trusted root CAs. Therefore the administrator must establish the trust relationship. The simplest approach is to export the MDM site certificate, then import the certificate into a local cert store in ISE. Most browsers allow this. Internet explorer is shown in Figure 2 with a
8Integrating Fiberlink MaaS360 with Cisco Identity Services Engine