•Querying Exchange Server using Microsoft PowerShell commands and standard APIs for vital information related to the ActiveSync enabled devices on the Exchange Server. The use of PowerShell and related APIs allows for abstraction from the specifics of the Exchange Server implementation and allows the Cloud Extender to support multiple Mailbox Servers and clustered/resilient Exchange server configurations.
•Processes device and policy information and transmits it to the Fiberlink MaaS360 Portal for reporting and management functions.
•Receives ActiveSync Policies, Device Actions, and Policy Assignments actions and carries out the relevant actions on the Exchange server.
Corporate Wipe
Both ISE and Fiberlink MaaS360 can remove corporate data from personal devices. Fiberlink MaaS360 calls this Selective Wipe. ISE refers to it as a Corporate Wipe. Other common terms used are selective wipe or partial wipe. When ISE issues this command, it is forwarded to Fiberlink MaaS360 via an API call. The MDM will then remove corporate applications using privileges granted to the MDM Profile. When these complete, the MDM profile is removed, which will remove all the associated
Selective wipes by themselves do not blacklist the device from either the MDM or ISE. An ISE administrator, the MDM administrator, or the user from either the ISE My Devices Portal or the Fiberlink MaaS360 may issue a selective wipe. If a selective wipe is being issued as a result of an employee’s termination, then additional steps must be undertaken, such as blacklisting the device with ISE and removing the user AD group memberships. This will prevent the user from
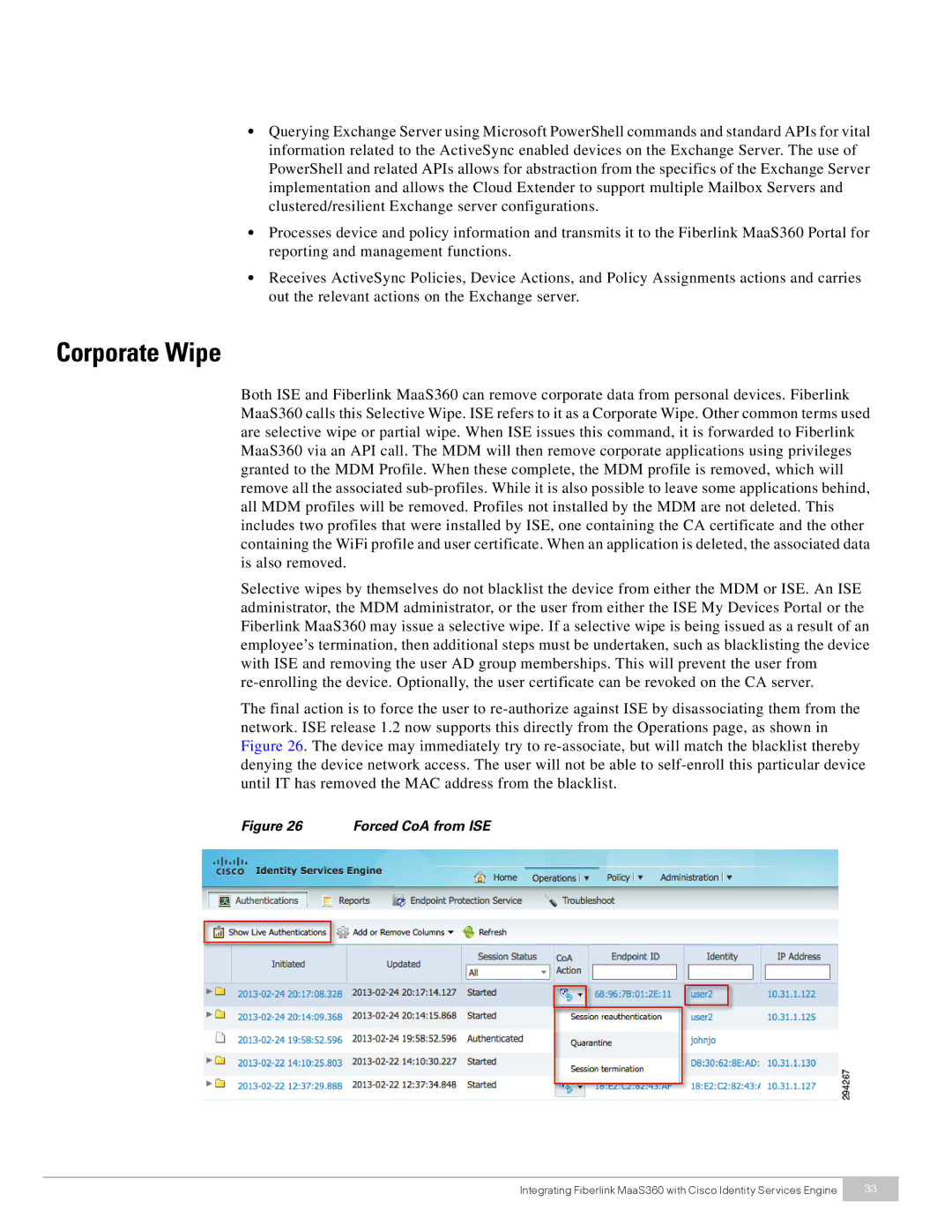
The final action is to force the user to
Figure 26 Forced CoA from ISE
Integrating Fiberlink MaaS360 with Cisco Identity Services Engine | 33 |
|
|