User Guide SBG900 Wireless Cable Modem Gateway
Comply with all instructions that accompany this equipment
Recycling your Motorola Equipment
Caring for the Environment by Recycling
FCC Compliance Class B Digital Device
FCC Certification
Regulatory, Safety, Software License, and Warranty Information Card
Canada - Industry Canada IC
Connecting a PC to the USB Port
Contents
Installation
Basic Configuration
Setting the Firewall Policy
Configuring the Gateway
Configuring TCP/IP
Setting Up Your Wireless LAN
Front-Panel Lights and Error Conditions
Setting Up a USB Driver
Troubleshooting
Contact Us Frequently Asked Questions Specifications Glossary
Overview
Network Connection Types
Easy Setup
Powerful Features in a Single Unit
SBG900
Sample Hybrid LAN
Internet
Wireless Ethernet
Optional Accessories
Adapter WU830G
WPCI810G
Light
Front Panel
Flashing
Key Item Description
Rear Panel
SBG900 LAN Choices
Label on the Rear of the SBG900
Sample wireless network connections
Wireless LAN
Sample Ethernet connection to hubs or switches
Wired Ethernet LAN
Sample Ethernet to computer connection
Sample USB connection
USB Connection
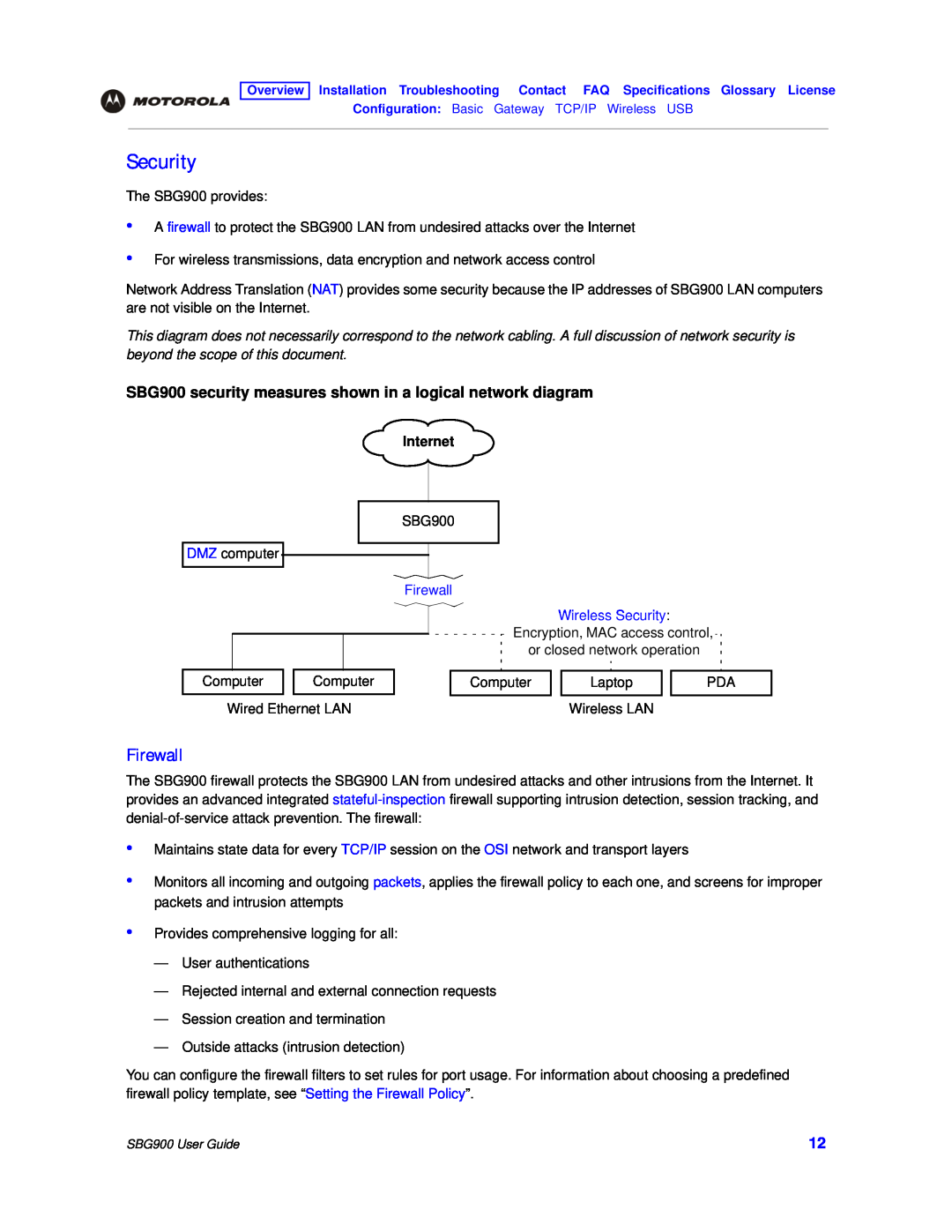
Firewall
SBG900 security measures shown in a logical network diagram
Firewall Wireless Security
Security
Port Triggering
Wireless Security
Virtual Private Networks
Port Forwarding
Related Documentation
Obtaining an IP Address for Ethernet Connecting a PC to the USB Port
Installation
Before You Begin Precautions Signing Up for Service
Connecting the SBG900 to the Cable System Cabling the LAN
To avoid damaging the SBG900 or computers with static electricity
Precautions
Signing Up for Service
Always make the wall connection first
Computer System Requirements
Connecting the SBG900 to the Cable System
Step
Cabling the LAN
Steps 5 to
Obtaining an IP Address in Windows 2000 or Windows XP
Obtaining an IP Address for Ethernet
Obtaining an IP Address on a Macintosh or UNIX System
Connecting a PC to the USB Port
Gaming Configuration Guidelines
Basic Configuration
Starting the SBG900 Setup Program Changing the Default Password
Getting Help Setting the Firewall Policy
Starting the SBG900 Setup Program
To Perform
Click
Changing the Default Password
3 Select Enable remote access
Enabling Remote Access
Getting Help
Setting the Firewall Policy
Page
Firewall POLICY - advanced Page
the Firewall Policy ”
Firewall POLICY - advanced page fields
Field
expertise
Firewall ALERT - basic page fields
Firewall ALERT - basic Page
Field or Button
Firewall ALERT - email page fields
Firewall ALERT - email Page
Firewall LOGS page fields
Firewall LOGS Page
Configuring the Firewall for Gaming
Gaming Configuration Guidelines
Configuring Port Triggers
Configuring a Gaming DMZ Host
Gateway PORT FORWARDING - config Page
Configuring the Gateway
Gateway STATUS Page Gateway WAN Page Gateway LAN - nat config Page
Gateway LAN - dhcp server config Page
This page displays the gateway status information
Gateway STATUS Page
Gateway WAN page fields
Gateway WAN Page
Gateway WAN page fields continued
Gateway LAN - nat config page fields
Gateway LAN - nat config Page
additional public IP addresses
Gateway LAN - dhcp server config page fields
Gateway LAN - dhcp server config Page
Gateway LAN - dhcp leases page fields
Gateway LAN - dhcp leases Page
FieldDescription
Gateway LAN - dhcp leases page fields continued
Gateway PORT FORWARDING - status Page
Gateway PORT FORWARDING - config page fields
Gateway PORT FORWARDING - config Page
Gateway PORT FORWARDING - config page fields continued
Gateway PORT TRIGGERS - predefined Page
Gateway PORT TRIGGERS - predefined page fields
Gateway PORT TRIGGERS - custom page fields
Gateway PORT TRIGGERS - custom Page
Gateway LOG page fields
Gateway LOG Page
Configuring TCP/IP in Windows Configuring TCP/IP in Windows XP
Configuring TCP/IP
Configuring TCP/IP in Windows 95, Windows 98, or Windows Me
Configuring TCP/IP in Windows 95, Windows 98, or Windows Me
3 Double-click the Network icon to display the Network window
13 Click Obtain an IP address automatically
Configuring TCP/IP in Windows
4 Click Local Area Connection number. The value of number varies from system to system. The Local Area Connection number Status window is displayed
8 Click Internet Protocol TCP/IP
13 Click OK to accept the TCP/IP settings
Configuring TCP/IP in Windows XP
5 If a classic view similar to below is displayed
7 Right-click on the network connection. If more than one connection is displayed, be sure to select the one for your network interface
11 Verify that the settings are correct, as shown above
Verifying the IP Address in Windows 95, Windows 98, or Windows Me
Verifying the IP Address in Windows 2000 or Windows XP
To renew the IP address
Use in Setup Program
Setting Up Your Wireless LAN
Perform
Configure on the SBG900
Encrypting Wireless LAN Transmissions
Required On Each Wireless Client
Configuring WPA on the SBG900
7 For Local WPA-PSK authentication only, set
5 Choose the WPA Authentication type
8 Click Save Changes
6 For Remote Radius authentication only, set
Configuring WEP on the SBG900
Encryption
Authentication
Restricting Wireless LAN Access
Configuring the Wireless Network Name on the SBG900
9 Click Apply to save your changes
7 Click advanced to display the Wireless SECURITY - advanced Page
3 Click advanced to display the Wireless SECURITY - advanced Page
Configuring a MAC Access Control List on the SBG900
If You Performed
Configuring the Wireless Clients
On Each Client, You Need to Perform
Configuring a Wireless Client for WEP
Configuring a Wireless Client for WPA
Configuring a Wireless Client with the Network Name ESSID
Wireless STATISTICS page
Wireless Pages in the SBG900 Setup Program
Wireless STATUS Page Wireless NETWORK Page
Wireless SECURITY - basic Page Wireless SECURITY - advanced Page
who is not authorized to use your WLAN
Wireless STATUS Page
Wireless STATUS Page Fields
the SBG900” or “Configuring WEP on the SBG900”
authorized to use your WLAN
Wireless NETWORK Page
Wireless NETWORK page fields
Configuring the Wireless Network Name on the SBG900
Wireless NETWORK page fields continued
Wireless SECURITY - basic Page
Wireless Security - ADVANCED page fields
Wireless SECURITY - advanced Page
Wireless Security - ADVANCED page fields continued
Wireless STATISTICS page
Wireless STATISTICS page fields
Wireless STATISTICS page fields continued
Setting Up a USB Driver in Windows
Setting Up a USB Driver
Setting Up a USB Driver in Windows 98 Second Edition
Setting Up a USB Driver in Windows 98 Second Edition
3 Click Next. The following window is displayed
7 Click Next. The following window is displayed
6 Select Specify a location and type the location of the CD-ROM drive
9 After the window shown under step 8 is displayed, click Next
Setting Up a USB Driver in Windows
3 Click Next. The following window is displayed
5 Click Next. The following window is displayed 6 Click Next
Setting Up a USB Driver in Windows Me
Setting Up a USB Driver in Windows XP
SBG900 User Guide
Removing the USB Driver from Windows 98 Second Edition or Windows Me
6 Perform Running the Motorola USB Driver Removal Utility
2 Click Settings
Removing the USB Driver from Windows
4 Disconnect the USB cable from the PC or SBG900
7 Double-click Network Adapters
12 Close the Control Panel window
13 Perform Running the Motorola USB Driver Removal Utility
9 Click the Uninstall icon. The following window is displayed
10 Click OK 11 Close the Device Manager window
Removing the USB Driver from Windows XP
4 Click System to display the System Properties window. Skip to step
6 Click the Hardware tab to display the Hardware page
12 Perform Running the Motorola USB Driver Removal Utility
8 Double-click Network adapters
Running the Motorola USB Driver Removal Utility
8 Click Exit to exit the Motorola USB Driver Removal Utility. or
Setting Up a USB Driver in Windows XP
the SBG900 Setup Program again
Troubleshooting
Problem
Possible Solutions
Turns Off During Startup If
Front-Panel Lights and Error Conditions
Turns Off During Normal Operation If
Contact Us
Q What wireless security measures are provided on the SBG900?
Frequently Asked Questions
Q What is high-speed cable Internet access?
Q What is Network Address Translation?
Q What do I do if my SBG900 stops working?
Q Do I need to change my Internet service provider ISP?
Q Do I need to subscribe to cable TV to get cable Internet access?
Q What type of technical support is available?
Specifications
Downstream DOCSIS
Upstream Euro-DOCSIS
Glossary
License
SBG900 User Guide
Glossary
Overview Installation Troubleshooting Contact FAQ Specifications
The SBG900 is simultaneously a DHCP client and a DHCP server
address
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
See Ethernet
U.S. government
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
Configuration Basic Gateway TCP/IP Wireless USB
SBG900 User Guide
You may
Software License
You may not
516850-001 08/05 MGBI
Visit our website at