The Crypto-C Environment
The Crypto-C Environment
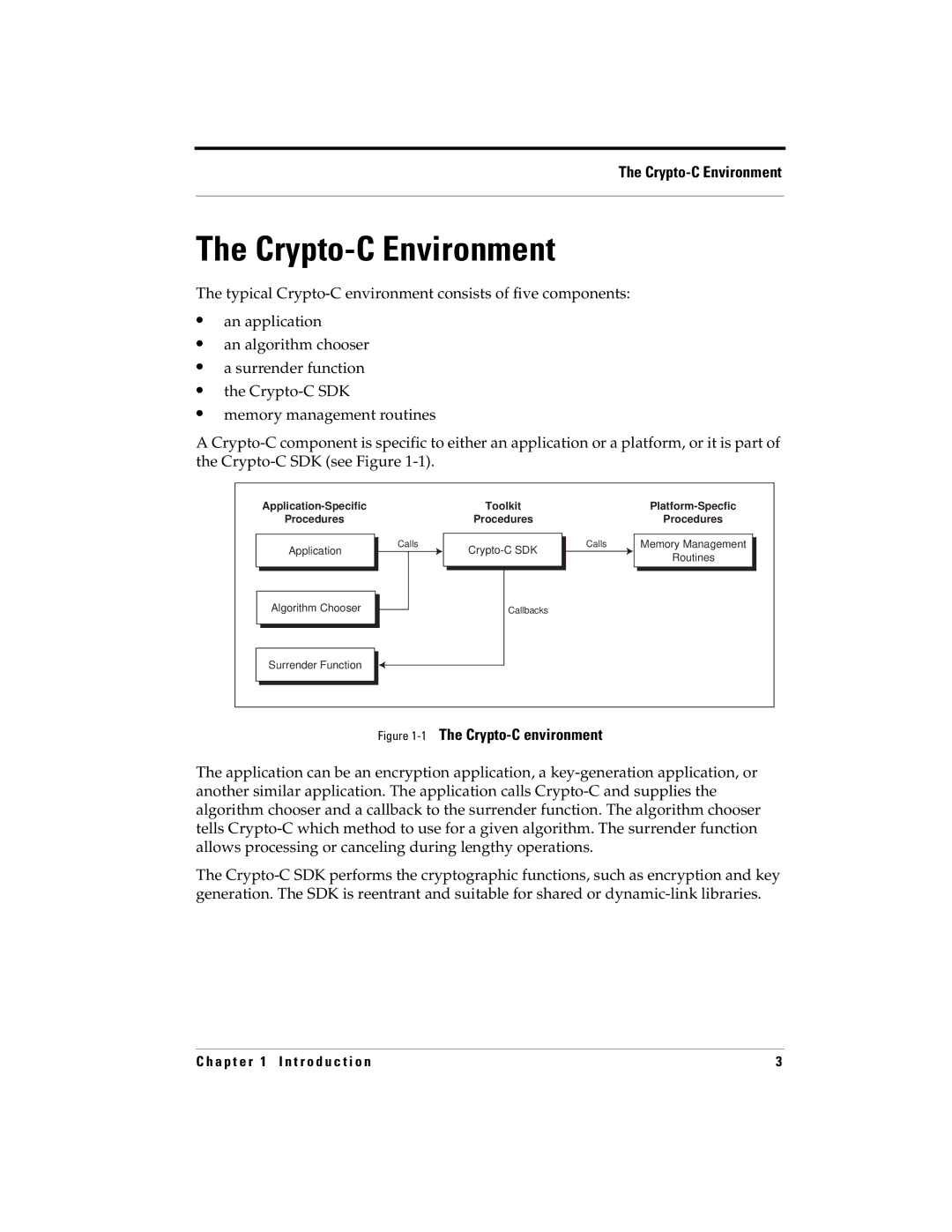
The typical Crypto-C environment consists of five components:
•an application
•an algorithm chooser
•a surrender function
•the Crypto-C SDK
•memory management routines
A Crypto-C component is specific to either an application or a platform, or it is part of the Crypto-C SDK (see Figure 1-1).
Application-Specific | Toolkit | | Platform-Specfic |
Procedures | Procedures | | Procedures |
Calls | Crypto-C SDK | Calls | Memory Management |
Application | | Routines |
| | |
Algorithm Chooser | Callbacks | | |
Surrender Function | | | |
Figure 1-1The Crypto-C environment
The application can be an encryption application, a key-generation application, or another similar application. The application calls Crypto-C and supplies the algorithm chooser and a callback to the surrender function. The algorithm chooser tells Crypto-C which method to use for a given algorithm. The surrender function allows processing or canceling during lengthy operations.
The Crypto-C SDK performs the cryptographic functions, such as encryption and key generation. The SDK is reentrant and suitable for shared or dynamic-link libraries.
C h a p t e r 1 I n t r o d u c t i o n | 3 |