Synology DiskStation Users Guide
Table of Contents
Back Up Data
Manage Media Server and iTunes Service
Store and Share Files over the Internet
Enjoy Entertainment Content on the Server
Transfer Files via FTP
Manage Files with Web-Based File Browser
Host Websites
Enjoy Music Anytime and Anywhere
Record Videos with IP Cameras
USB Print Server
Most Models
Bay & 2-Bay Models
DS211+
DS710+
DiskStation
Bay Models
1U RackStation
DS411slim
DS1511+
2U RackStation
Log in to Synology DiskStation Manager
Install Synology DiskStation
Use Synology Assistant
Windows User
Mac OS X User
Get Started with Synology DiskStation Manager
Linux Ubuntu User
Use a Web Browser
Desktop and Shortcuts
DiskStation Manager Appearance
To create a desktop shortcut to an application
To remove a desktop shortcut to an application
Logout, Restart, and Shutdown
Manage DSM with the Main Menu
Taskbar
Open Application Windows
Reorder Main Menu’s Thumbnails
Use the Control Panel
To open an application window
Manage Personal Options
Volume Usage
Account
To modify your account
To choose a background color for your desktop
Desktop
Tick Customize Wallpaper
Tick Customize Wallpaper and then tick Customize image
Tick Dont show confirmation dialog when leaving DSM
Tick Do not expand the Main Menu after login
Tick Resume DSM to previous logout status when logging
Photo Station
Login Style
Change DSM Settings
To change the style of login
To display your own recognition image on the login
To enable Https connection
Http Service Options
About redirecting to Https connection
Ports used for Https connection
Session Security
To set the logout timer
To skip IP checking
Tick Enhance browser compatibility by skipping IP checking
To enable File Browser log
Enable File Browser log
Tick Enable File Browser log
To see the File Browser log
To set up domain name server and default gateway
Change Network Settings
General
To rename DiskStation
To decide how your DiskStation obtains IP address
To set up IPv6
Network Interface
To separate the Bond interface into multiple LAN interfaces
Bond
To combine multiple LAN interfaces with Link Aggregation
To set up a wireless network
Wireless Network
IPv6 Setup
To connect to the Internet via PPPoE
Click PPPoE Setting
PPPoE
Tunnel
To setup IPv6 Tunnel
Tick Enable tunnel
Language
Modify Regional Options
To set the time zone
Set Up Time
To set the date and time manually
To sync the date and time with NTP server
Below are a few recommended NTP servers
Use Energy Saving Features
Power Recovery
Manage General Settings
Tick Restart automatically after a power failure
HDD Hibernation
To manage beep control
Fan speed mode
Manage Beep Control
Manage UPS
Tick the Enable UPS support checkbox
Choose Startup or Shutdown
Power Schedule
Synology DiskStation Supported RAID Types
What is Volume and Disk Group?
Volume Creation Methods
Manage Volumes or Disk Groups with Storage Manager
To create a SHR volume using the Quick mode
Create a Volume
Create a Volume Using the Quick Mode
Create a Volume by Allocating Partial Space on a Disk Group
Create a Volume by Combining Several Hard Disks
To create a volume by combining several hard disks
Choose Single Volume on RAID, and click Next
To create a Disk Group
To create volumes on the created Disk Group
Create a Disk Group
Repair a Volume or Disk Group
Remove a Volume or Disk Group
Click the Volume or Disk Group tab
To repair a volume or Disk Group
Change RAID Type
Expand a Volume or Disk Group
Expand a Volume by Changing Volume Size
For RAID 1 and RAID 5, RAID 5+Spare, and RAID
For one-bay models
For Basic or RAID 0 on models with two or more bays
To expand a volume or Disk Group by adding disks
Expand a Volume or Disk Group by Adding Disks
ISCSI
Manage iSCSI Target with Storage Manager
ISCSI Target and LUN
To create an iSCSI Target
Tick Enable iSNS
Click Enable or Disable
To create an iSCSI LUN
Manage iSCSI LUNs with Storage Manager
There are 2 ways to create an iSCSI LUN
To edit an iSCSI LUN
To remove an iSCSI LUN
Manage Hard Disks with Storage Manager
Enable Write Cache Support for Hard Disks
To enable write cache support for your disk
Quick Test Extended Test
Run S.M.A.R.T. Analysis
Check Disk Info
To attach an external disk
Manage External Disks
To get the information of the disk
To eject or format an external disk
To use the EZ-Internet wizard
Set Up Port Forwarding Rules for Router
Use the EZ-Internet Wizard
To set up your router
Set up Router
Add Port Forwarding Rules
Give Synology DiskStation a Ddns Hostname
To add port forwarding rules
To test whether your rules are working or not
Register a Ddns hostname for Synology DiskStation
Service Requirement
Method 2 Register a Ddns account at No-IP.com
To create a firewall rule
Prevent Unauthorized Connection with Firewall
To disable rules
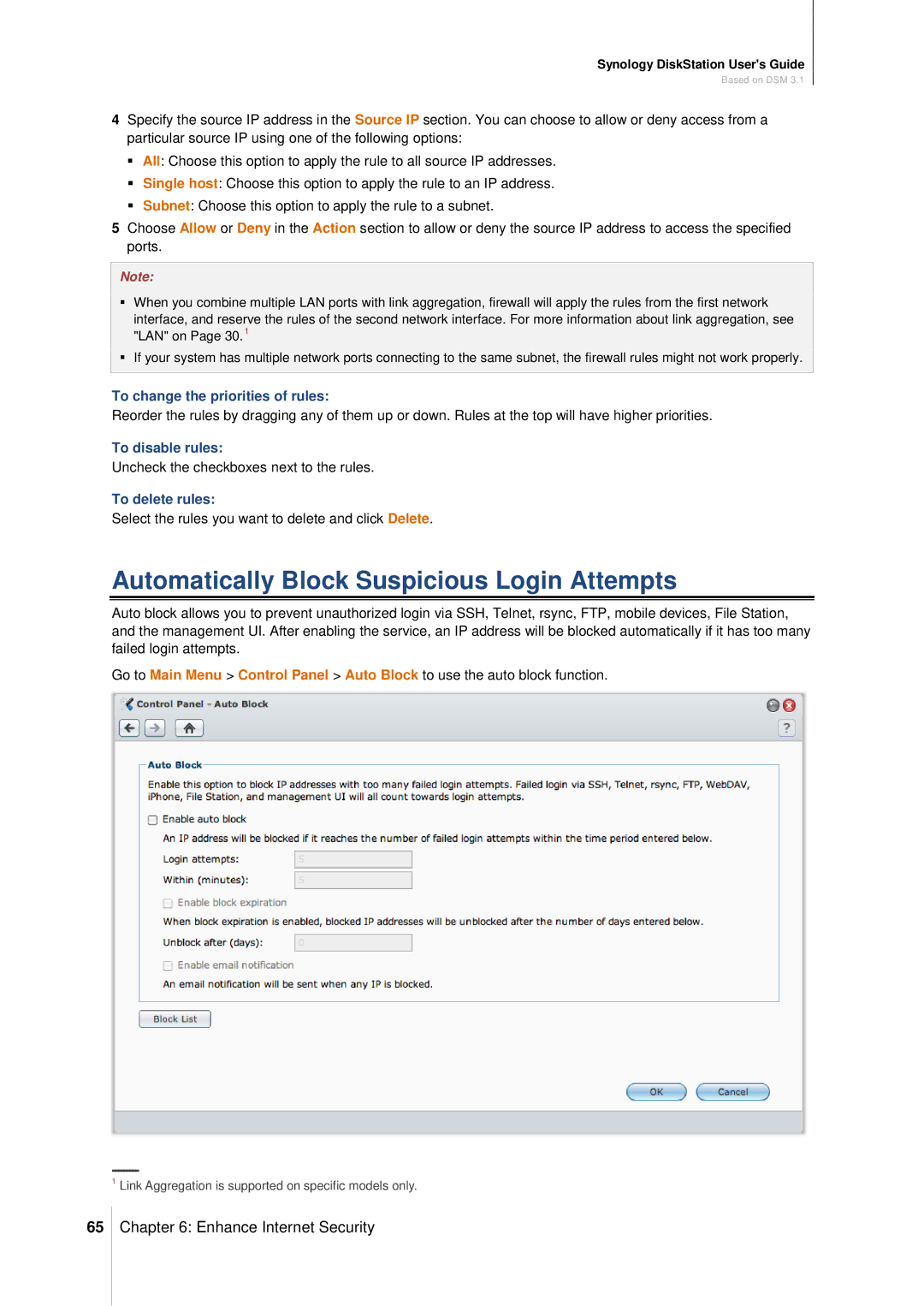
Automatically Block Suspicious Login Attempts
To change the priorities of rules
To delete rules
To manage the blocked IP addresses
To enable auto block
Tick Enable auto block
Manage Windows File Service
Enable File Sharing Protocols for All Platforms
To enable Windows file service
Tick Enable Windows file service
Manage Mac File Service
Tick Enable NFS
Enable NFS Service for Linux Clients
To join a domain
Join a Windows ADS Domain or Workgroup
To join a workgroup
About advanced domain options
Manage Users and Groups
About DNS server
Click Create to open the User Creation Wizard
Create and Edit Users
To create a user account
Go to Main Menu Control Panel User and click Import Users
To create a user account by importing users list
To edit a user
To search for a user
To apply password strength rules
Apply Password Strength Rules
Click Password Strength Tick Apply password strength rules
To cancel password strength rules
Click User Home Tick Enable user home service
To enable user home service
To disable user home service
Click User Home Uncheck Enable user home service
Create Domain User’s Home Folder
Create and Edit Groups
Allow Users to Access Applications
System built-in shared folders include the following
Set Up Shared Folders
Built-in Shared Folders Created by the System
To create a new shared folder
Create a Shared Folder
To allow users or groups to access a shared folder
Allow Users or Groups to Access Shared Folders
Remove a Shared Folder
To remove a shared folder
To manage domain users’ access privileges
Allow Domain Users or Groups to Access Shared Folders
To allow Linux clients to access a shared folder
To encrypt a shared folder
To manage domain group’s access privileges
Encrypt a Shared Folder
Edit an Encrypted Folder
To edit Windows ACL settings
To define Windows ACL settings for a shared folder
Define Windows ACL Privileges for Shared Folder
Click Shared Folder in Control Panel
Index Shared Folder Contents
To index files in a shared folder
Tick Enable file indexing
Method 2 Use the Run window
Access Files within the Intranet
Access Shared Folders from Windows
Method 3 Use Window Explorer
Access Shared Folders from Linux
Access Shared Folders from Mac
Tick Enable FTP service
Access Files via FTP
To enable FTP service
Report external IP in Pasv mode
Set up FTP Connection Restriction
Enable UTF-8 filename support
Enable FTP file transfer log
Manage FTP Security Settings
Access Files via WebDAV
Connect to Synology DiskStation Using a FTP Application
To configure the privilege of anonymous user
File Browser Requirement
Access Files via File Browser
File Browser Appearance
Go to Main Menu File Browser to open a File Browser window
To perform advanced search
Search for Files or Folders
To search for files or folders in the current folder
Download Files or Folders from Synology DiskStation
Set File Browser in Action
Upload Files or Folders to Synology DiskStation
Method
Copy or Move Files or Folders on Synology DiskStation
Create a Folder
Rename a File or Folder on Synology DiskStation
Delete Files or Folders
Extract an Archive
Open a File in a New Window
Edit the Properties of Files and Subfolders
To open a file in a new window
Choose Open in New Window from the Action menu
To allow users and groups to access files and subfolders
Allow Users and Groups to Access Files and Subfolders
Obtain a File or Folder’s Download Link
100
101
Edit Music Information
To obtain a file or folders download link
To view or edit music information
102
View Documents, Photos, or Videos
View Documents in Google docs
103
Preview Photos
104
Play Videos
Display Additional Attributes
Access Files via File Station
105
Go to Main Menu and click File Station
Use Data Replicator for Windows
Back Up Computer Data
What Can Data Replicator Do?
106
Use Time Machine for Mac
Install Data Replicator
Data Replicator Requirement
Use Data Replicator
Ways to Back Up Synology DiskStation Data
Back Up Data on Synology DiskStation
Use rsync for Linux
Create a Backup Task
Perform Backup Tasks on Synology DiskStation
109
Before you start, do the following first
Back Up and Restore System Configuration
Sync Shared Folder Contents between DiskStations
112
Manage Sync Tasks
113
Backup DiskStation Data with Time Backup
To perform USBCopy
Use USBCopy to Back Up Data on USB Device
114
To perform SDCopy
Use SDCopy to Back Up Data on SD card
115
Tick Enable Web Station
Enable Web Station
Use Web Station to Host Websites
116
Enable Personal Website
Enable Virtual Host to Host Websites
Tick Enable personal website and click OK
117
Enable MySQL
Manage PHP Settings
To Enable MySQL
To turn on PHP configuration option registerglobals
To enable PHP cache
Install Featured Applications
119
To customize PHP openbasedir
Tick Enable web Https connection
Modify Http Service Options
120
To add an additional Http port
Manage WebDAV
To enable WebDAV
Use WebDAV to Manage Files in Different Environments
121
Click Files Open
122
Click Places Connect to server
Host Mail Server
Set up Mail Server
Before you start
123
To install Mail Station
Install Mail Station to Enable Webmail Service
124
To connect to Mail Station
To set up print server on DiskStation
Set up Print Server on DiskStation
Set Synology DiskStation as Print Server
125
126
Access Print Server with iOS Devices
To access the print server with an iOS device
To set up print server access with Windows
Set up Computer to Access Print Server
To set up print server access with Mac OS
127
Manage Printer
Release the Connection between Printer and Client
128
Click Release Printer
129
This chapter explains how to do the following
Tick Enable Photo Station
Enable Photo Station
Support and Limitations
130
Enable DSM User’s Photo Station
Enable Personal Photo Station
Click Enable Personal Photo Station service
131
Click Enable Personal Photo Station username and click OK
To enable DSM user’s Photo Station
Manage Photo Station User Accounts
132
Create Albums
Upload Albums Using Photo Uploader Synology Assistant
133
To edit existing user accounts
Upload Using DS photo+ Mobile App
Create Album Using Photo Station
Upload via File Sharing Protocols or File Browser
134
Edit Album Details
Manage Albums
Upload Photos and Videos to an Album
135
Reorder Albums
Download Album
136
To allow users to download albums
Set as Private Album
Click Customize next to Access Permissions
137
Uncheck Set as public
To Enable Virtual Album
Enable Virtual Album
Move or Delete Album
138
139
View and Edit Photos and Videos
To see photo or video’s details, click the following links
To share photo or video’s link to social network
140
Customize Album Layout
To add comments to photo or video
To customize album layout
Add a New Post
Use the Blog
Delete a Post
Personalize the Blog
142
Find Old Posts
143
Play Music with Audio Station
144
Enable Audio Station
Click Enable Audio Station 3 and click OK
Library
Choose Audio Source
Personal and Shared Playlist
145
IPod
Smart Playlist
Internet Radio
Media Server
Browse Music
Organize Your Music
Change Views
See Your Current Location
To search music
Search Music
148
149
Work with Playlist
To create a playlist, do any of the following
To create a smart playlist
150
Play Music
To rename or remove a playlist
To remove songs from a playlist
Add Music to Queue
About the Output Modes and the Queue Panel
Add a Playlist to Queue
151
Play Music with Music Player
Manage Songs in the Queue Panel
152
Click Play/Pause, Next, or Previous
153
Enable Transcoder
Play Music with Mini Player
Tick Enable music download
Go to Settings Transcoder
Download Music
154
155
Enable Download Station
To enable Download Station
To connect to Download Station, do any of the following
Set up BT/HTTP/FTP/NZB
156
Download Schedule
Default Destination Folder
157
To set advanced schedule
BitTorrent
Premium Account
Torrent Search
158
159
Create BT/HTTP/FTP/NZB Download Tasks
Create by Entering URLs
Create by Uploading Files
160
To create download tasks by uploading files
To create download tasks via torrent search
Create via Torrent Search
161
To view and update the list of RSS feeds
What is RSS?
Create Download Tasks for RSS Feeds
162
To create download tasks by selecting RSS feeds
163
164
To create download tasks by setting download filter
View BitTorrent/HTTP/FTP/NZB Tasks
Manage BT/HTTP/FTP/NZB Download Tasks
Manage BitTorrent/HTTP/FTP/NZB Tasks
165
To edit download tasks
166
To clear finished download tasks
To change the list order of download tasks
167
Set up eMule
To manage server settings
Location
Connection
168
To set the download destination folder for eMule
169
Connect to ED2K Server/Kad
Bandwidth
170
Create eMule Download Tasks
To delete ED2K servers
To connect to a random ED2K server
To resume an eMule download task
171
To create download tasks by uploading a file
172
Create via eMule Search
To create download tasks via general search
173
To create download tasks via advanced search
To clear search results
174
Manage eMule Download Tasks
Manage Download Queue
175
Check Upload Queue
To enable Surveillance Station
Enable Surveillance Station
Tick Enable Surveillance Station
176
Manage IP Cameras
Choose Quick Setup or Complete Setup and click Next
Add a Camera
177
178
To edit camera settings
Edit Camera and Recording Settings
To edit motion detection settings
179
To disable cameras
To edit the guard settings
180
To remove cameras
To enable cameras
Export or Import Camera Configuration
To export camera configuration
To import camera configuration
182
Watch Live View
183
Configure Layout
184
Use PTZ Control
Use Other Functions
About Events
Play and Manage Events
185
The green icon represents Motion Detection Recording
186
Play Events with Timeline
To select an event source
To find events on the timeline
To use smart search
Search for Specific Situations with Smart Search
187
To view events with Image Enhancements
View Events with Image Enhancements
188
189
Edit Events
To play an event with the Event Player
To lock events
190
Export Events
Choose Delete Delete all
Choose Delete Delete this
191
Select Enable or Disable
Mount Events
192
Click Close to close the E-Map Configurations window
Use E-Map
193
Receive Email or SMS Notification
Initial Page Setting1
Manage Advanced Settings
Centralized Management1
194
MPEG4 Streaming Port Range2
VisualStation1
Video Output Module
195
196
View Log
To delete the log
To save the log
197
Assign Privilege
To change users privilege
To authorize cameras
About Camera License
To install a camera license
Use VisualStation
198
199
Manage Dlna Media Server
Following shared folders will be accessed by DMA Devices
200
photo video music
Tick Enable DLNA/UPnP media server and click OK
Record Diagnostic Log
Determine the DMA Menu Language and Style
Re-index Media Files
Tick Show videos title using embedded information
Manage Browsing Settings
Tick Enable Internet Radio
202
Play Multimedia Contents with DMA Devices
Enable iTunes Service
Manage iTunes Service
Tick Enable iTunes service and enter your Shared name
Use Smart Playlist
205
Re-index Audio Files
To edit a smart playlist
To delete a smart playlist
Systems general information includes the following
Check System Information
206
Network
To check volume usage
Storage
207
208
Log
209
Monitor System Resources
System resources include the following
To see the details of any of the resources
To check if the latest DSM is available for download
Update DSM
210
To perform manual DSM update
To check for updates regularly
To install a new package
Manage Packages
Receive Event Notification
Click Uninstall
Receive Email Notification
212
213
Tick Enable SMS notifications
Receive SMS Notification
Restore Synology DiskStation to Factory Defaults
Reset admins Password
To reset admins password
There are three restore options
Enable Snmp Service
Reinstall Synology DiskStation
Tick Enable Snmp service and enter a Community name
215
216
Enable Terminal Services
DS audio
Use iOS and Android Apps
DS cam
DS photo+
218
Use Other Mobile Devices
219
Appendix a Synology DiskStation Specifications
DS710+ DS211j DS211+
220
DS410 DS411slim DS411j DS411+II RS411 RS810+ RS810RP+
221
DS411j DS411+II RS411 RS810+ RS810RP+
222
‧日本語 ‧ 한국어 ‧繁體中文 ‧简体中文
223
‧日本語‧한국어‧繁體中文‧简体中文
224
225
Limitations
226
Appendix B LED Indication Tables
227
HDD1 & HDD2
228
229
DiskStations
230
RackStations
Alert
231
232
Troubleshooting
SYNOLOGY, INC END User License Agreement
Page
SYNOLOGY, INC Limited Product Warranty
Limitations of Liability