Chapter 5 Configuring the Router’s Security
General
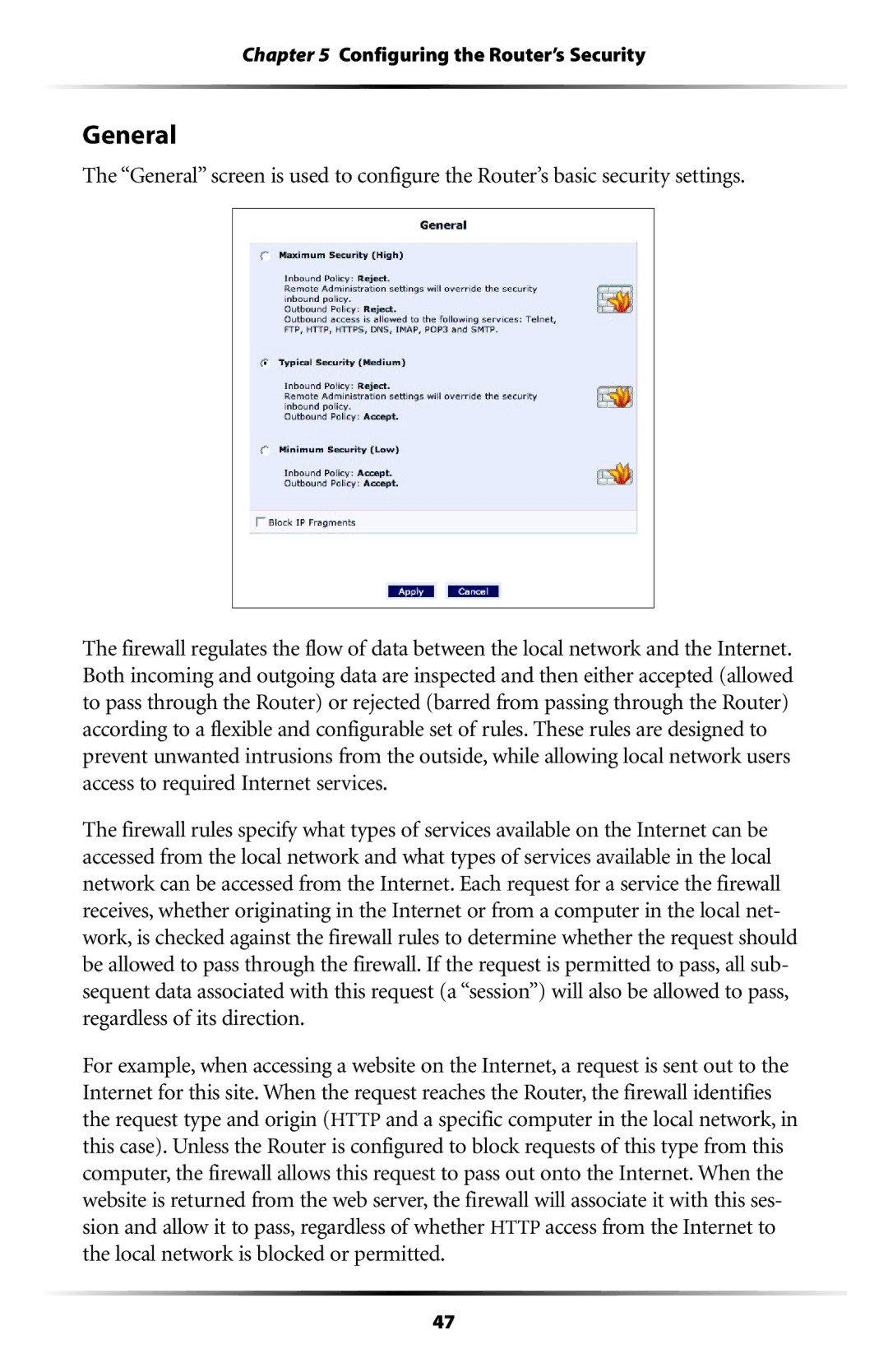
The “General” screen is used to configure the Router’s basic security settings.
The firewall regulates the flow of data between the local network and the Internet. Both incoming and outgoing data are inspected and then either accepted (allowed to pass through the Router) or rejected (barred from passing through the Router) according to a flexible and configurable set of rules. These rules are designed to prevent unwanted intrusions from the outside, while allowing local network users access to required Internet services.
The firewall rules specify what types of services available on the Internet can be accessed from the local network and what types of services available in the local network can be accessed from the Internet. Each request for a service the firewall receives, whether originating in the Internet or from a computer in the local net- work, is checked against the firewall rules to determine whether the request should be allowed to pass through the firewall. If the request is permitted to pass, all sub- sequent data associated with this request (a “session”) will also be allowed to pass, regardless of its direction.
For example, when accessing a website on the Internet, a request is sent out to the Internet for this site. When the request reaches the Router, the firewall identifies the request type and origin (HTTP and a specific computer in the local network, in this case). Unless the Router is configured to block requests of this type from this computer, the firewall allows this request to pass out onto the Internet. When the website is returned from the web server, the firewall will associate it with this ses- sion and allow it to pass, regardless of whether HTTP access from the Internet to the local network is blocked or permitted.
47