Chapter 5 Configuring the Router’s Security
•FTP port request to 3rd party is forbidden (Possible bounce attack) - a packet has been blocked.
•Firewall Rules were changed - the firewall rule set has been modified.
•User authentication - a message arrived during login time, including both successful and failed authentication.
Security Log Settings
To view or change the security log settings:
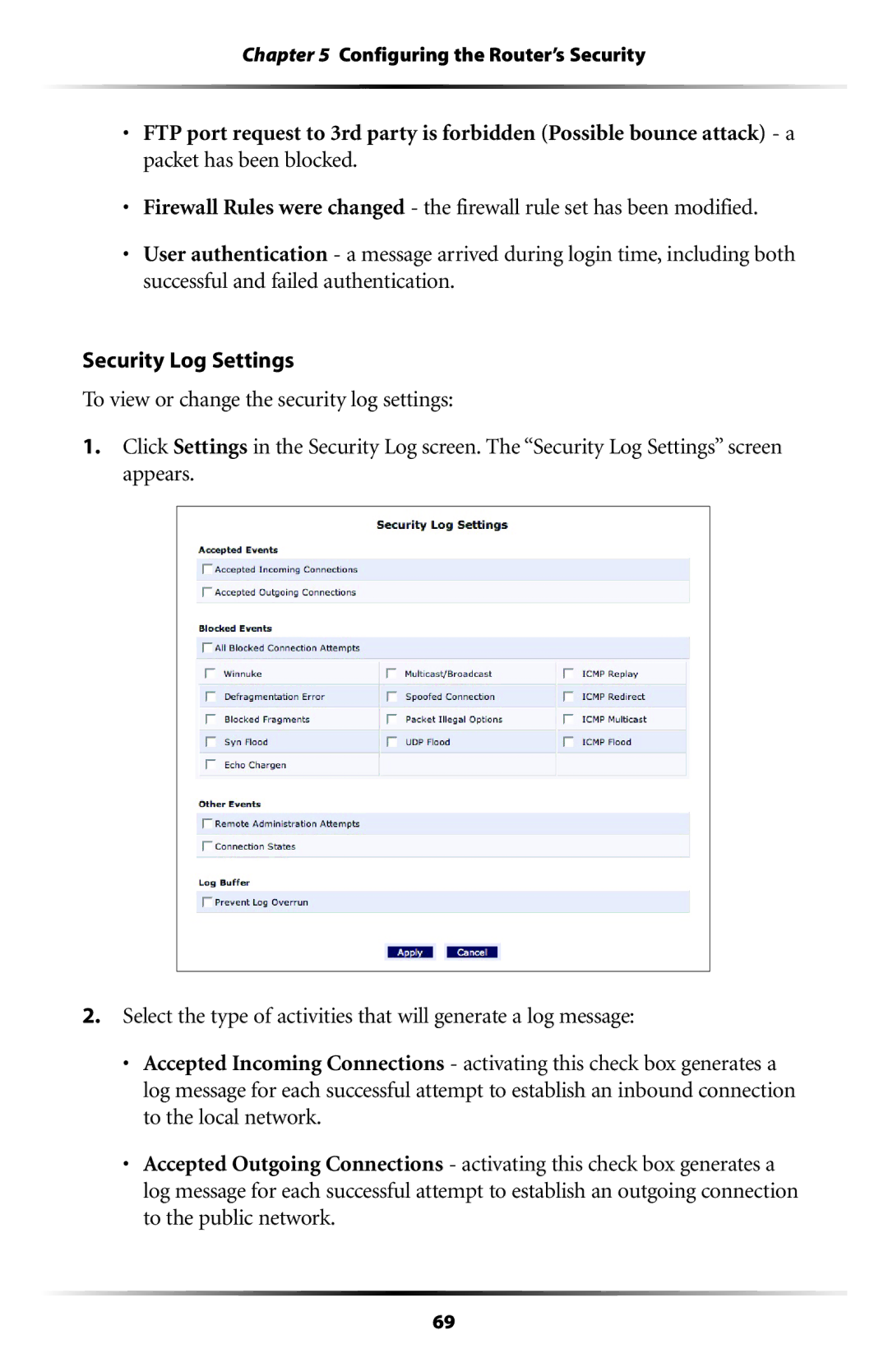
1.Click Settings in the Security Log screen. The “Security Log Settings” screen appears.
2.Select the type of activities that will generate a log message:
•Accepted Incoming Connections - activating this check box generates a log message for each successful attempt to establish an inbound connection to the local network.
•Accepted Outgoing Connections - activating this check box generates a log message for each successful attempt to establish an outgoing connection to the public network.
69