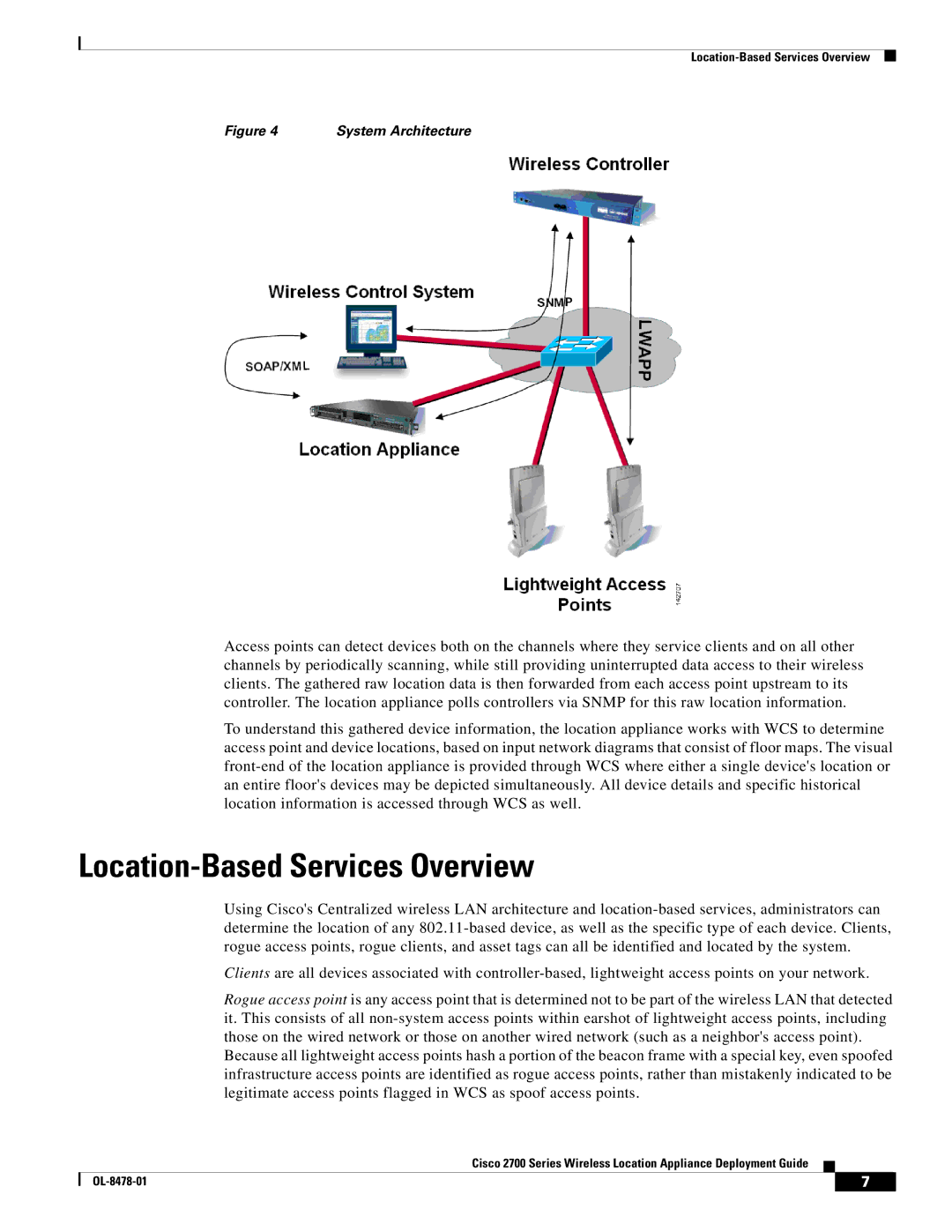
Figure 4 | System Architecture |
Access points can detect devices both on the channels where they service clients and on all other channels by periodically scanning, while still providing uninterrupted data access to their wireless clients. The gathered raw location data is then forwarded from each access point upstream to its controller. The location appliance polls controllers via SNMP for this raw location information.
To understand this gathered device information, the location appliance works with WCS to determine access point and device locations, based on input network diagrams that consist of floor maps. The visual
Location-Based Services Overview
Using Cisco's Centralized wireless LAN architecture and
Clients are all devices associated with
Rogue access point is any access point that is determined not to be part of the wireless LAN that detected it. This consists of all
Because all lightweight access points hash a portion of the beacon frame with a special key, even spoofed infrastructure access points are identified as rogue access points, rather than mistakenly indicated to be legitimate access points flagged in WCS as spoof access points.
Cisco 2700 Series Wireless Location Appliance Deployment Guide
| 7 |
| |
|
|