Chapter 4 Configuring the VSA
Configuration Tasks
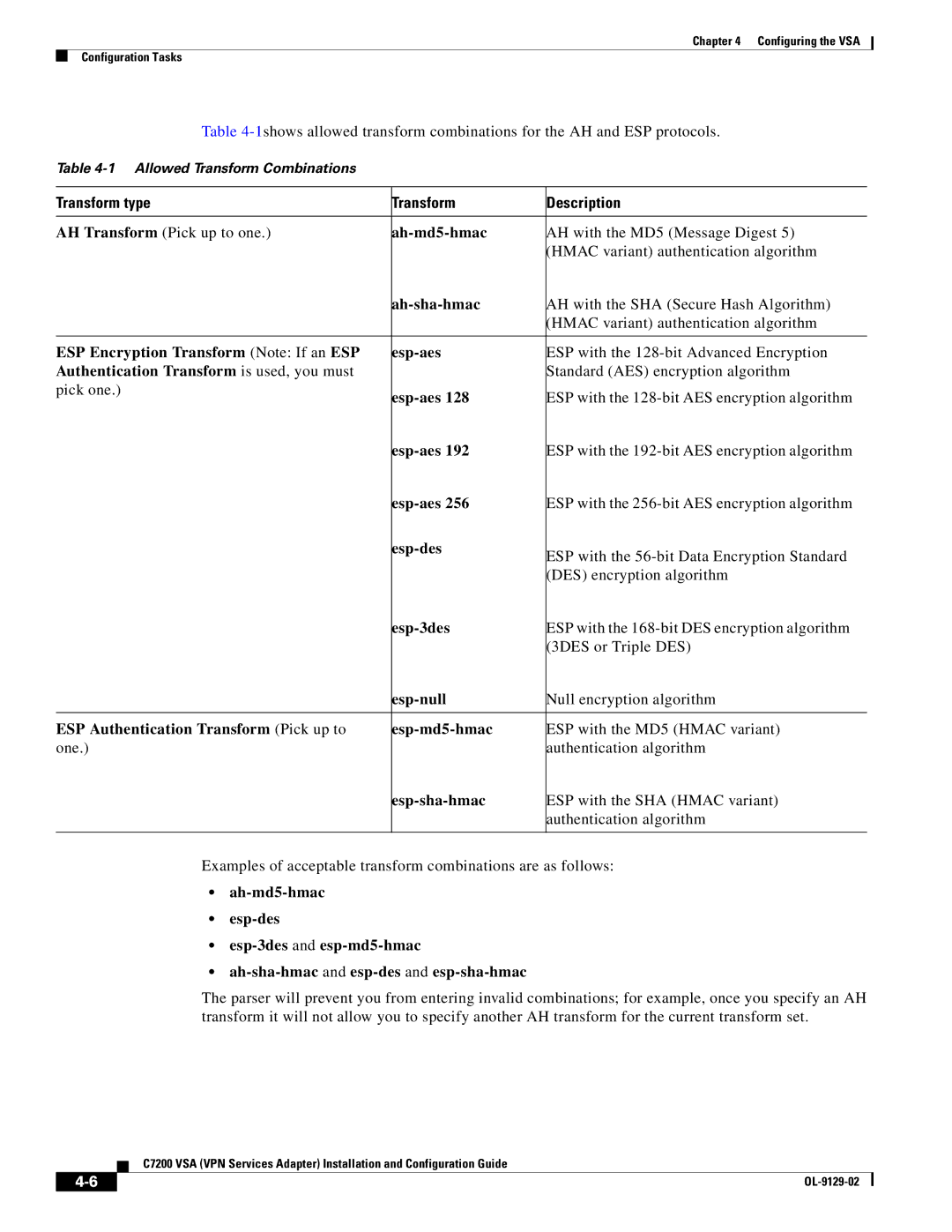
Table
Table
Transform type | Transform | Description |
|
|
|
AH Transform (Pick up to one.) | AH with the MD5 (Message Digest 5) | |
|
| (HMAC variant) authentication algorithm |
| AH with the SHA (Secure Hash Algorithm) | |
|
| (HMAC variant) authentication algorithm |
|
|
|
ESP Encryption Transform (Note: If an ESP | ESP with the | |
Authentication Transform is used, you must |
| Standard (AES) encryption algorithm |
pick one.) | ESP with the | |
| ||
| ESP with the | |
| ESP with the | |
| ESP with the | |
|
| |
|
| (DES) encryption algorithm |
| ESP with the | |
|
| (3DES or Triple DES) |
| Null encryption algorithm | |
|
|
|
ESP Authentication Transform (Pick up to | ESP with the MD5 (HMAC variant) | |
one.) |
| authentication algorithm |
|
| ESP with the SHA (HMAC variant) |
|
| authentication algorithm |
|
|
|
Examples of acceptable transform combinations are as follows:
•
•
•
•
The parser will prevent you from entering invalid combinations; for example, once you specify an AH transform it will not allow you to specify another AH transform for the current transform set.
C7200 VSA (VPN Services Adapter) Installation and Configuration Guide
|
| |
|