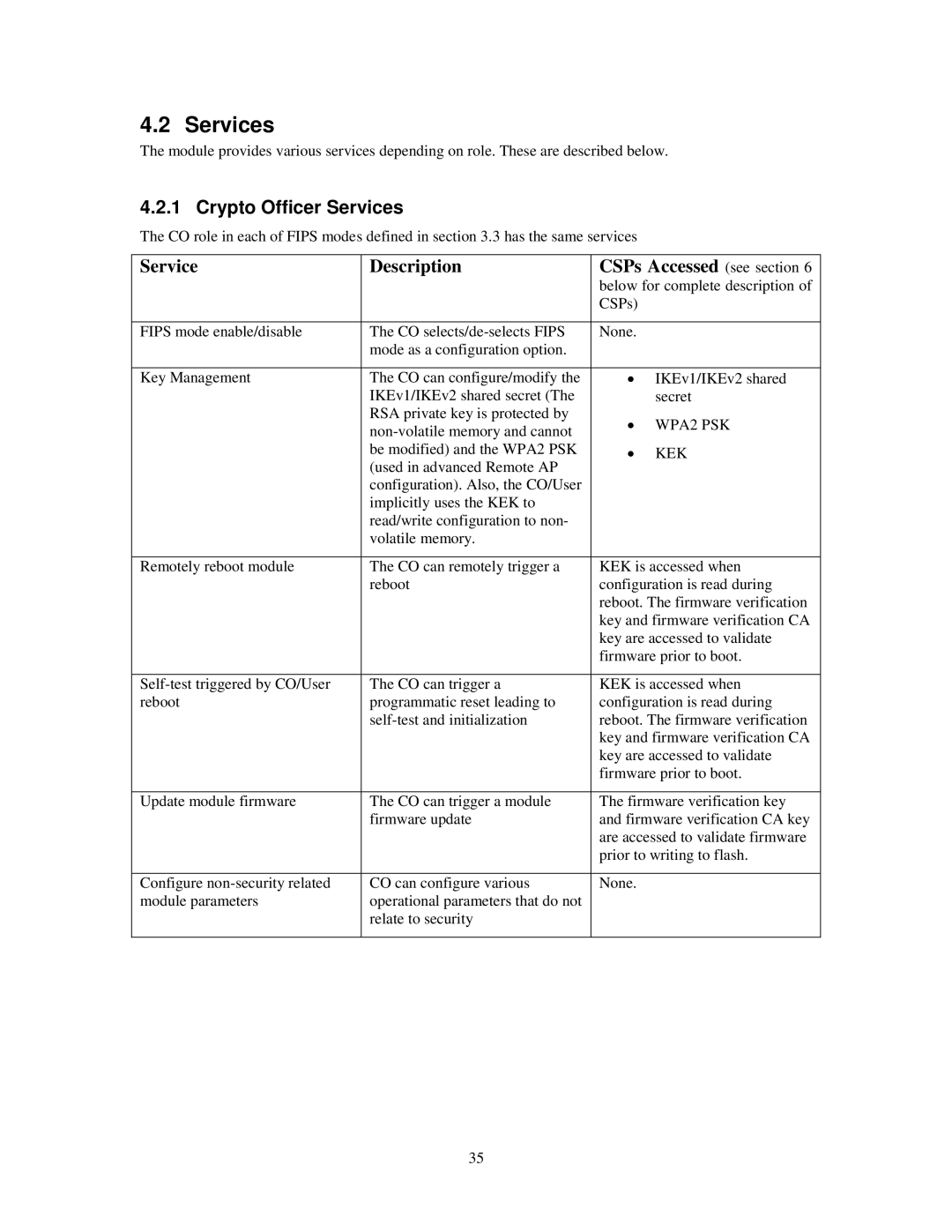
4.2 Services
The module provides various services depending on role. These are described below.
4.2.1 Crypto Officer Services
The CO role in each of FIPS modes defined in section 3.3 has the same services
Service | Description | CSPs Accessed (see section 6 | |
|
| below for complete description of | |
|
| CSPs) |
|
|
|
|
|
FIPS mode enable/disable | The CO | None. |
|
| mode as a configuration option. |
|
|
|
|
|
|
Key Management | The CO can configure/modify the | ∙ | IKEv1/IKEv2 shared |
| IKEv1/IKEv2 shared secret (The |
| secret |
| RSA private key is protected by | ∙ | WPA2 PSK |
| |||
|
|
| |
| be modified) and the WPA2 PSK | ∙ | KEK |
| (used in advanced Remote AP |
|
|
| configuration). Also, the CO/User |
|
|
| implicitly uses the KEK to |
|
|
| read/write configuration to non- |
|
|
| volatile memory. |
|
|
|
|
| |
Remotely reboot module | The CO can remotely trigger a | KEK is accessed when | |
| reboot | configuration is read during | |
|
| reboot. The firmware verification | |
|
| key and firmware verification CA | |
|
| key are accessed to validate | |
|
| firmware prior to boot. | |
|
|
| |
The CO can trigger a | KEK is accessed when | ||
reboot | programmatic reset leading to | configuration is read during | |
| reboot. The firmware verification | ||
|
| key and firmware verification CA | |
|
| key are accessed to validate | |
|
| firmware prior to boot. | |
|
|
| |
Update module firmware | The CO can trigger a module | The firmware verification key | |
| firmware update | and firmware verification CA key | |
|
| are accessed to validate firmware | |
|
| prior to writing to flash. | |
|
|
|
|
Configure | CO can configure various | None. |
|
module parameters | operational parameters that do not |
|
|
| relate to security |
|
|
|
|
|
|
35