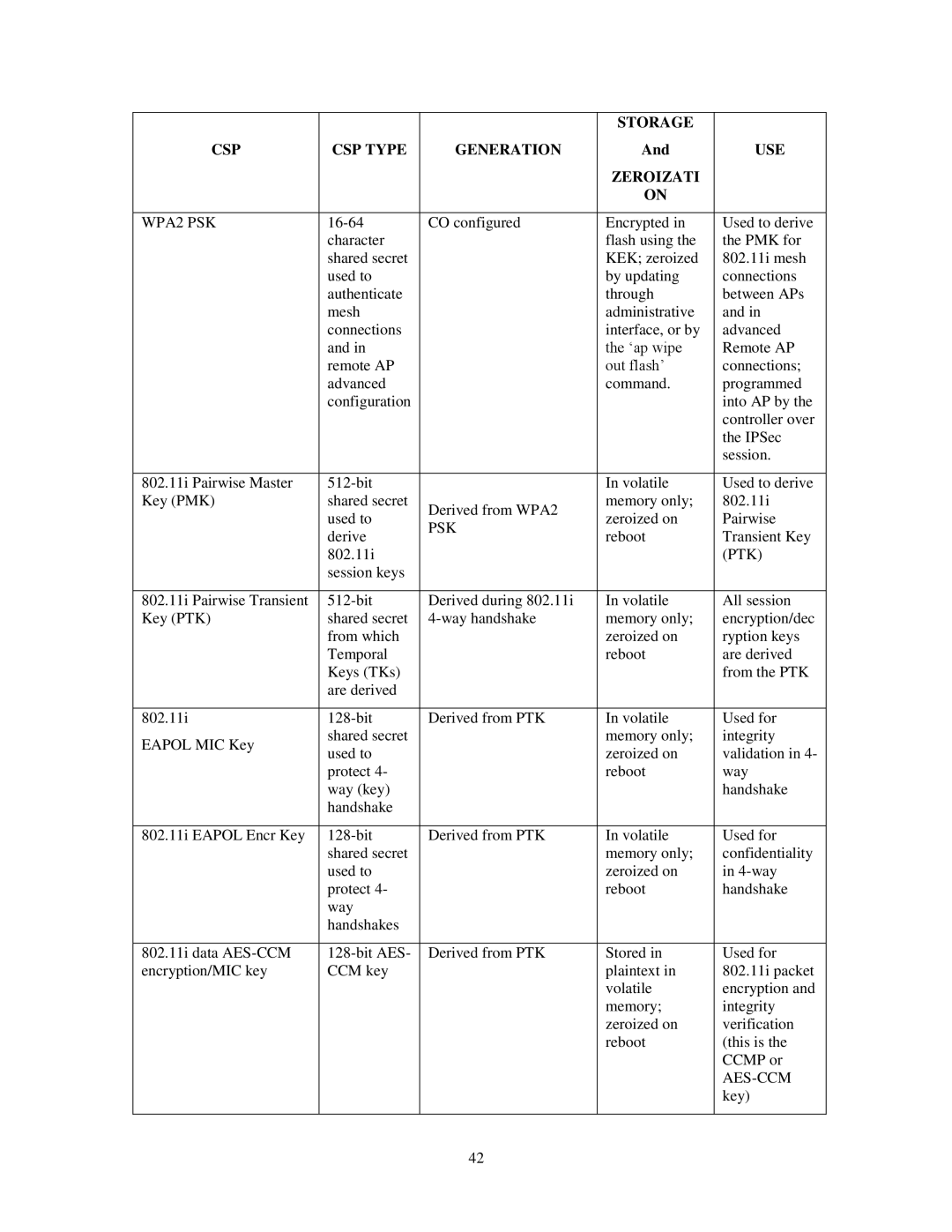
|
|
| STORAGE |
|
CSP | CSP TYPE | GENERATION | And | USE |
|
|
| ZEROIZATI |
|
|
|
| ON |
|
|
|
|
|
|
WPA2 PSK | CO configured | Encrypted in | Used to derive | |
| character |
| flash using the | the PMK for |
| shared secret |
| KEK; zeroized | 802.11i mesh |
| used to |
| by updating | connections |
| authenticate |
| through | between APs |
| mesh |
| administrative | and in |
| connections |
| interface, or by | advanced |
| and in |
| the ‘ap wipe | Remote AP |
| remote AP |
| out flash’ | connections; |
| advanced |
| command. | programmed |
| configuration |
|
| into AP by the |
|
|
|
| controller over |
|
|
|
| the IPSec |
|
|
|
| session. |
|
|
|
|
|
802.11i Pairwise Master |
| In volatile | Used to derive | |
Key (PMK) | shared secret | Derived from WPA2 | memory only; | 802.11i |
| used to | zeroized on | Pairwise | |
| PSK | |||
| derive | reboot | Transient Key | |
|
| |||
| 802.11i |
|
| (PTK) |
| session keys |
|
|
|
|
|
|
|
|
802.11i Pairwise Transient | Derived during 802.11i | In volatile | All session | |
Key (PTK) | shared secret | memory only; | encryption/dec | |
| from which |
| zeroized on | ryption keys |
| Temporal |
| reboot | are derived |
| Keys (TKs) |
|
| from the PTK |
| are derived |
|
|
|
|
|
|
|
|
802.11i | Derived from PTK | In volatile | Used for | |
EAPOL MIC Key | shared secret |
| memory only; | integrity |
used to |
| zeroized on | validation in 4- | |
|
| |||
| protect 4- |
| reboot | way |
| way (key) |
|
| handshake |
| handshake |
|
|
|
|
|
|
|
|
802.11i EAPOL Encr Key | Derived from PTK | In volatile | Used for | |
| shared secret |
| memory only; | confidentiality |
| used to |
| zeroized on | in |
| protect 4- |
| reboot | handshake |
| way |
|
|
|
| handshakes |
|
|
|
|
|
|
|
|
802.11i data | Derived from PTK | Stored in | Used for | |
encryption/MIC key | CCM key |
| plaintext in | 802.11i packet |
|
|
| volatile | encryption and |
|
|
| memory; | integrity |
|
|
| zeroized on | verification |
|
|
| reboot | (this is the |
|
|
|
| CCMP or |
|
|
|
|
|
|
|
|
| key) |
|
|
|
|
|
42