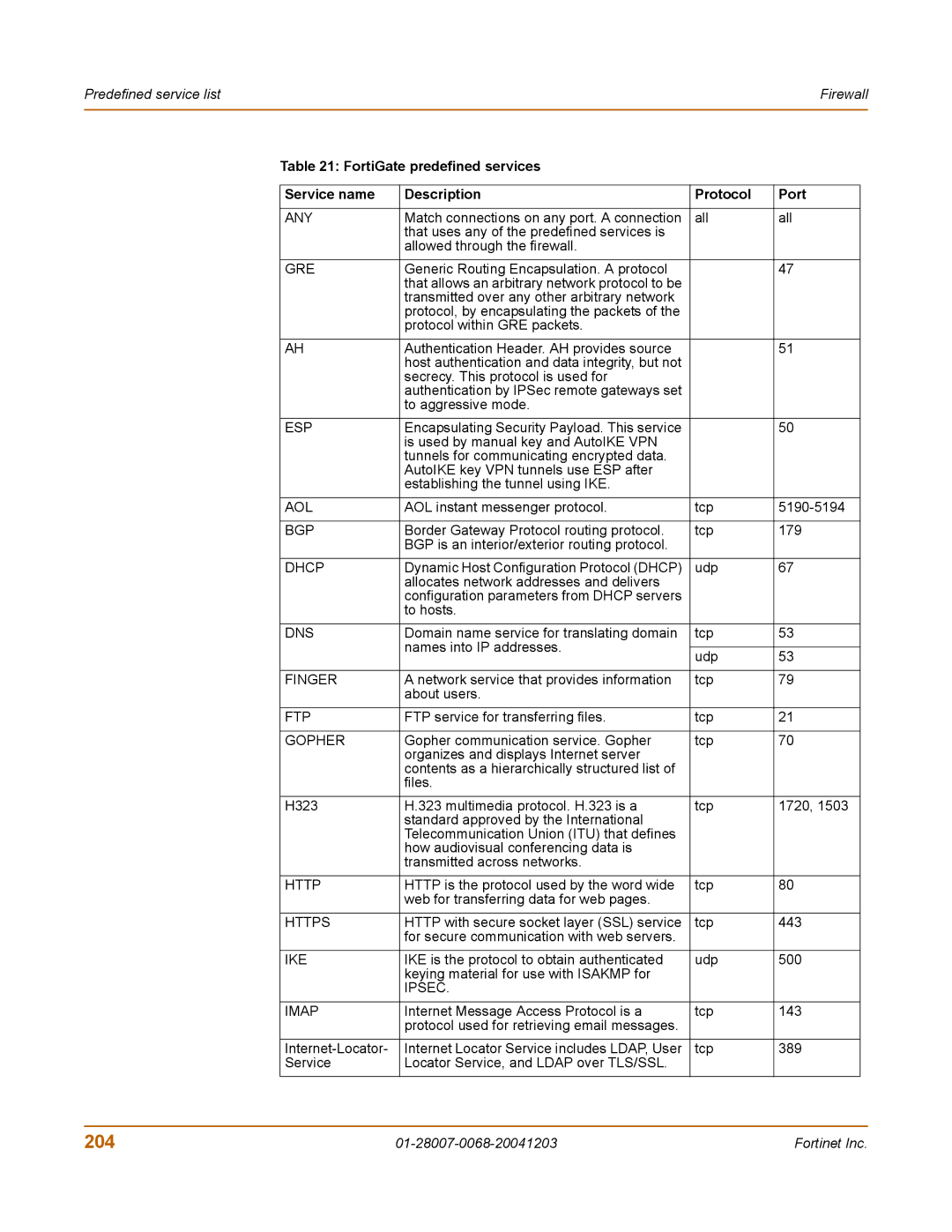
100A specifications
Fortinet 100A is a versatile network security device designed to provide comprehensive protection against various cyber threats while ensuring optimal network performance. As part of the FortiGate series, the 100A combines advanced security features with powerful hardware capabilities, making it suitable for small to medium-sized businesses.One of the key features of the Fortinet 100A is its deep packet inspection technology. This capability allows the firewall to analyze both the header and payload of packets traversing the network, enabling it to detect and block malicious content effectively. The 100A can identify and mitigate a wide range of threats, including malware, intrusions, and application-layer attacks.
The FortiOS operating system powers the Fortinet 100A, offering a robust and user-friendly interface for configuration and management. With its unified security management console, administrators can efficiently monitor network traffic and enforce security policies across the organization. The system provides centralized logging and reporting features, enabling users to gain valuable insights into their security posture and respond swiftly to incidents.
The 100A supports multiple deployment modes, including transparent, NAT, and route modes. This flexibility allows organizations to integrate the device into their existing network architecture with ease. The firewall's high throughput capabilities ensure that network performance remains unaffected, even under heavy load from multiple users and devices.
Another notable aspect of the Fortinet 100A is its support for various VPN technologies, including IPsec and SSL VPN. This feature facilitates secure remote access for employees, enabling them to connect to the corporate network safely, regardless of their location. As remote work continues to be a norm in many sectors, this capability is critical for maintaining productivity and security.
In addition to these features, the Fortinet 100A provides comprehensive web filtering capabilities, protecting users from harmful websites and inappropriate content. This protection is essential for organizations looking to maintain a secure and productive environment.
With its combination of powerful security features, flexible deployment options, and robust performance, the Fortinet 100A stands out as an ideal solution for organizations seeking to bolster their cybersecurity measures while ensuring seamless connectivity for users. As cyber threats continue to evolve, investing in a capable device like the FortiGate 100A is crucial for maintaining a secure network infrastructure.