3-1-5. Management Security
Through the management security configuration, the manager can do the strict setup to control the switch and limit the user to access this switch.
The following rules are offered for the manager to manage the switch:
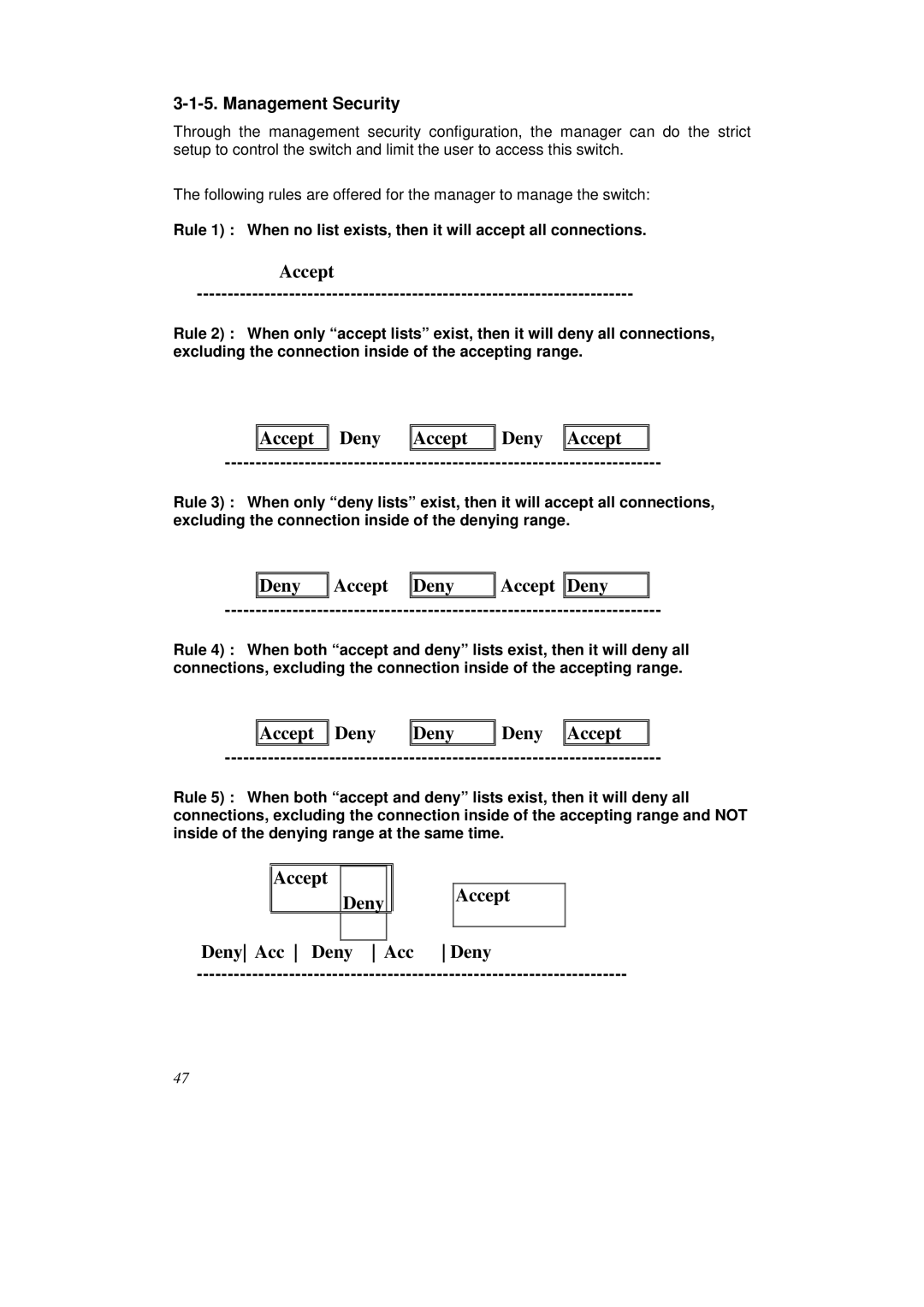
Rule 1) : When no list exists, then it will accept all connections.
Accept
Rule 2) : When only “accept lists” exist, then it will deny all connections, excluding the connection inside of the accepting range.
Accept | Deny | Accept | Deny | Accept |
Rule 3) : When only “deny lists” exist, then it will accept all connections, excluding the connection inside of the denying range.
Deny | Accept | Deny | Accept | Deny |
Rule 4) : When both “accept and deny” lists exist, then it will deny all connections, excluding the connection inside of the accepting range.
Accept | Deny | Deny | Deny | Accept |
Rule 5) : When both “accept and deny” lists exist, then it will deny all connections, excluding the connection inside of the accepting range and NOT inside of the denying range at the same time.
Accept |
|
|
|
|
| Deny |
|
| Accept |
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
Deny Acc Deny Acc Deny
47