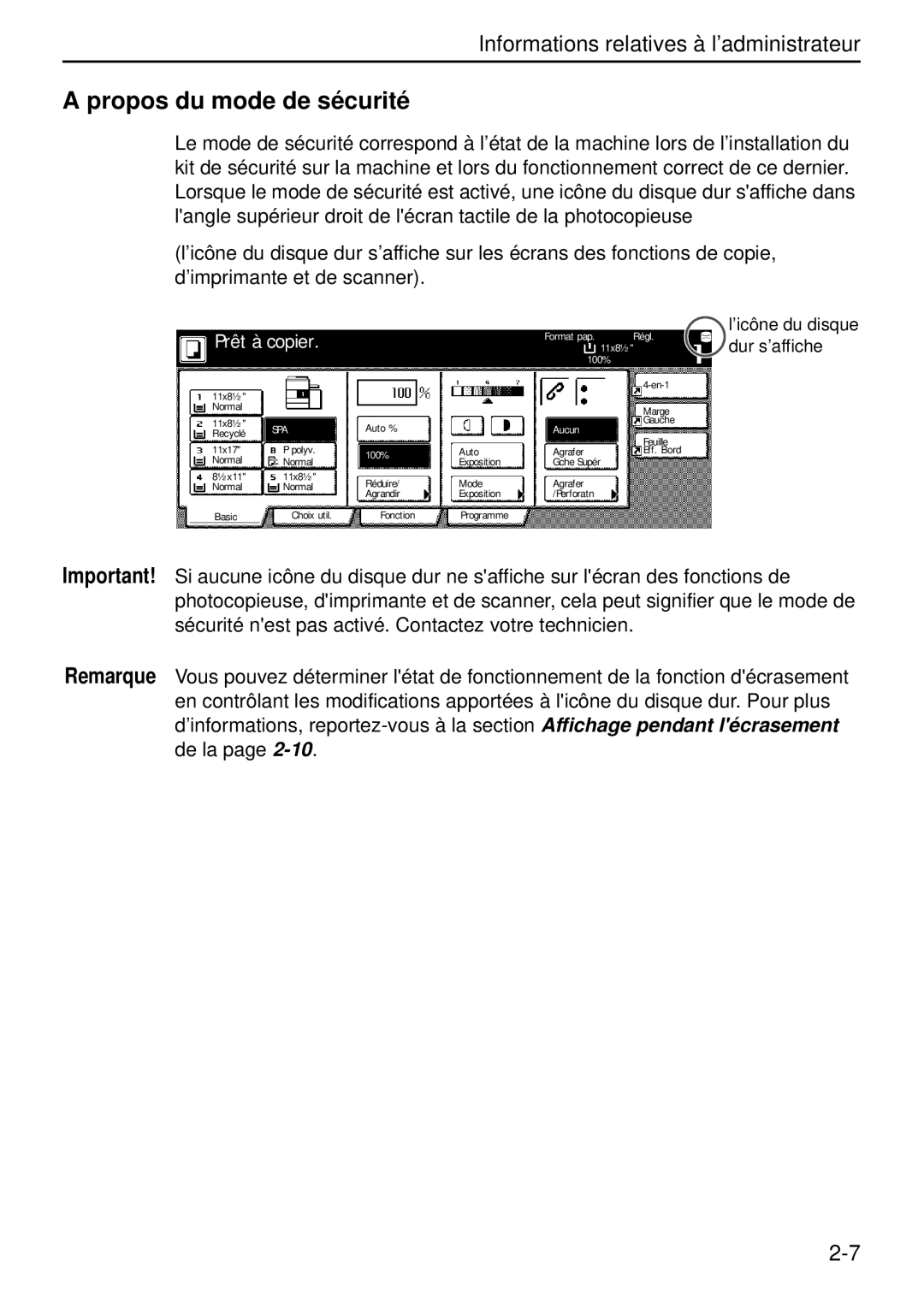
Data Security Kit (B) For Copier specifications
The Kyocera Data Security Kit (B) is an essential accessory for businesses that prioritize the security of their confidential information. Designed specifically for Kyocera multifunction printers (MFPs), this component enhances the overall operational integrity by providing advanced data protection features.One of the main features of the Data Security Kit (B) is its ability to encrypt data. This technology ensures that all sensitive documents processed by the copier are securely encoded, safeguarding them from unauthorized access. The encryption process involves transforming readable data into a coded format, making it unreadable to anyone who does not possess the appropriate decryption key. This is particularly beneficial in environments where sensitive information is frequently handled, such as legal or financial offices.
Another key characteristic of the Data Security Kit (B) is its secure overwrite functionality. This feature permanently deletes data from the copier’s hard drive after a job is completed. Unlike typical deletion methods that leave data recoverable, the secure overwrite function writes over the original data multiple times, ensuring that sensitive information is irretrievable. This proactive measure helps companies comply with stringent data protection regulations such as GDPR and HIPAA.
The Data Security Kit (B) also supports user authentication features. This functionality restricts access to the printer based on user permissions, thereby reducing the risk of unauthorized use. By implementing user authentication protocols, businesses can efficiently manage who can print, scan, or copy sensitive documents.
Additionally, the kit includes audit logging capabilities. This technology keeps a detailed record of all print, copy, scan, and fax activities, including user identification and the type of documents processed. These logs are invaluable for maintaining accountability and can be essential during audits or security assessments.
In terms of compatibility, the Kyocera Data Security Kit (B) integrates seamlessly with various Kyocera MFP models, making it a versatile choice for organizations already utilizing Kyocera's equipment. The installation process is straightforward, allowing businesses to enhance their data security with minimal disruption.
Overall, the Kyocera Data Security Kit (B) provides organizations with a robust solution to protect their confidential information. With its encryption capabilities, secure overwrite functionality, user authentication, and audit logging, it addresses the critical need for effective data security in today’s business landscape. Organizations can confidently manage sensitive information while ensuring compliance with data protection regulations, contributing to overall operational efficiency and security.