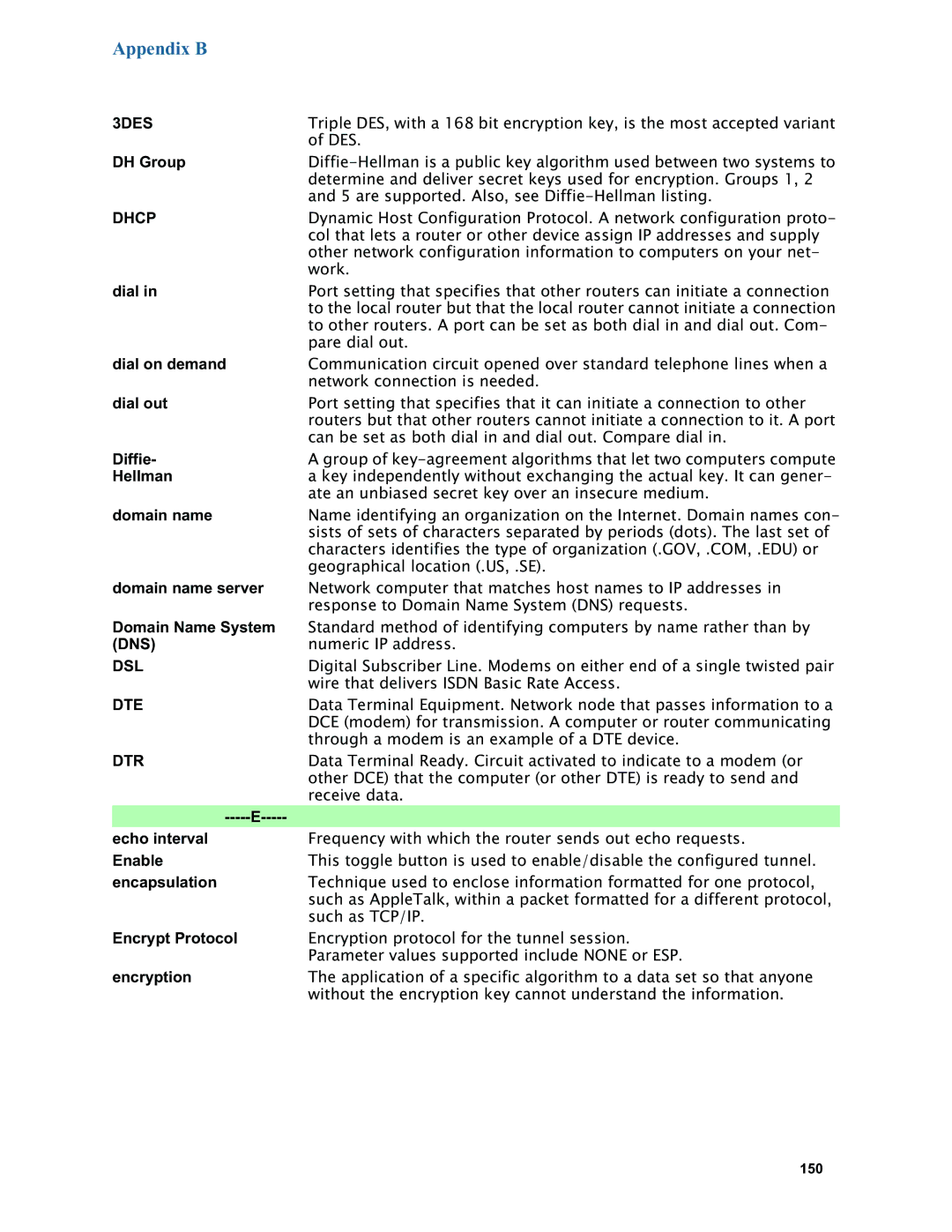
6.3 specifications
Netopia 6.3 is a powerful software solution designed to enhance digital content management, online collaboration, and project workflow for businesses of all sizes. This version introduces a plethora of new features, technologies, and improvements that streamline processes and foster greater productivity.One of the standout features of Netopia 6.3 is its enhanced user interface. The intuitive design allows users to navigate the system with ease, minimizing the learning curve for new team members. The dashboard provides a customizable view, enabling users to prioritize tasks and track project milestones at a glance.
Collaboration is at the heart of Netopia 6.3. The platform offers integrated communication tools, including real-time chat and video conferencing options, facilitating seamless teamwork regardless of geographic location. Additionally, users can share files and documents securely within the platform, reducing reliance on external tools.
Another significant upgrade in this version is the robust data analytics capabilities. Netopia 6.3 provides advanced reporting tools that enable users to generate detailed insights into project performance, resource allocation, and team productivity. This data-driven approach empowers decision-makers to make informed choices and optimize their strategies for improved outcomes.
The integration of artificial intelligence also sets Netopia 6.3 apart. AI-driven features help automate routine tasks, such as scheduling meetings and sending reminders, allowing teams to focus on more critical aspects of their work. Enhanced search functionalities enable users to find information quickly across the platform, improving overall efficiency.
Security remains a top priority in Netopia 6.3. The platform employs advanced encryption protocols to safeguard user data and ensure compliance with industry standards. Role-based access controls allow organizations to manage user permissions effectively, ensuring that sensitive information is accessible only to authorized personnel.
Netopia 6.3 also boasts compatibility with various third-party applications, making it easier for organizations to integrate existing tools into their workflows. This adaptability ensures that businesses can maintain their preferred systems while leveraging the benefits of Netopia's features.
In summary, Netopia 6.3 is a comprehensive solution that combines a user-friendly interface, enhanced collaboration tools, robust analytics, AI capabilities, and strong security measures. With these advancements, it positions itself as a valuable asset for organizations looking to improve project management and workflow efficiency. As the digital landscape continues to evolve, Netopia 6.3 equips businesses with the tools they need to thrive in a competitive environment.