1752 and 1754 SHDSL Router User’s Guide
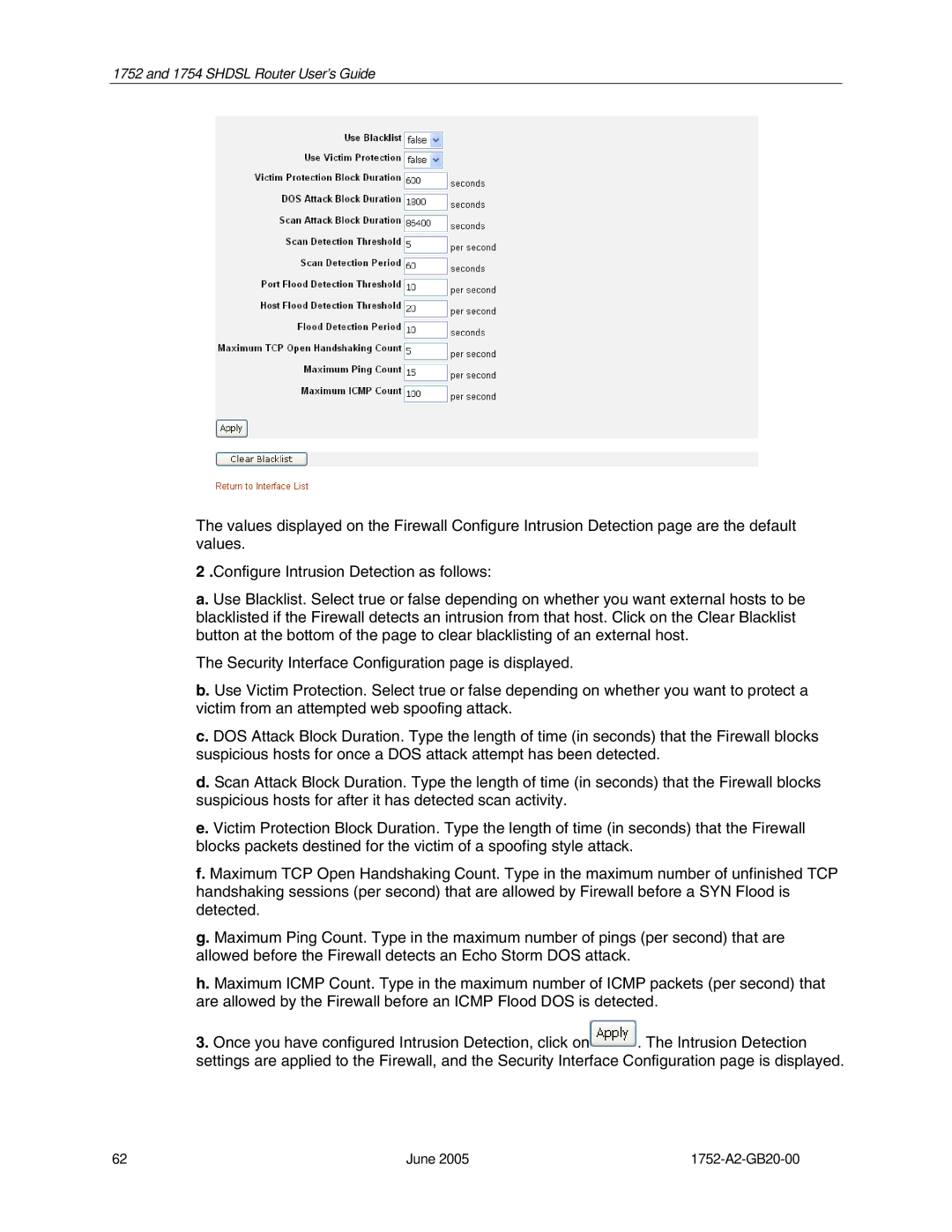
The values displayed on the Firewall Configure Intrusion Detection page are the default values.
2 .Configure Intrusion Detection as follows:
a. Use Blacklist. Select true or false depending on whether you want external hosts to be blacklisted if the Firewall detects an intrusion from that host. Click on the Clear Blacklist button at the bottom of the page to clear blacklisting of an external host.
The Security Interface Configuration page is displayed.
b. Use Victim Protection. Select true or false depending on whether you want to protect a victim from an attempted web spoofing attack.
c. DOS Attack Block Duration. Type the length of time (in seconds) that the Firewall blocks suspicious hosts for once a DOS attack attempt has been detected.
d. Scan Attack Block Duration. Type the length of time (in seconds) that the Firewall blocks suspicious hosts for after it has detected scan activity.
e. Victim Protection Block Duration. Type the length of time (in seconds) that the Firewall blocks packets destined for the victim of a spoofing style attack.
f. Maximum TCP Open Handshaking Count. Type in the maximum number of unfinished TCP handshaking sessions (per second) that are allowed by Firewall before a SYN Flood is detected.
g. Maximum Ping Count. Type in the maximum number of pings (per second) that are allowed before the Firewall detects an Echo Storm DOS attack.
h. Maximum ICMP Count. Type in the maximum number of ICMP packets (per second) that are allowed by the Firewall before an ICMP Flood DOS is detected.
3.Once you have configured Intrusion Detection, click on![]() . The Intrusion Detection settings are applied to the Firewall, and the Security Interface Configuration page is displayed.
. The Intrusion Detection settings are applied to the Firewall, and the Security Interface Configuration page is displayed.
62 | June 2005 |