2–Planning
Security
59265-02 B 2-23
To secure F_Ports and E_Ports in the fabric, configure security on the devices that
support security: Switch_1, Switch_2, and Adapter_1:
1. Create a security set (Security_Set_1) on Switch_1.
a. Create a port group (Group_Port_1) in Security_Set_1 with Switch_1,
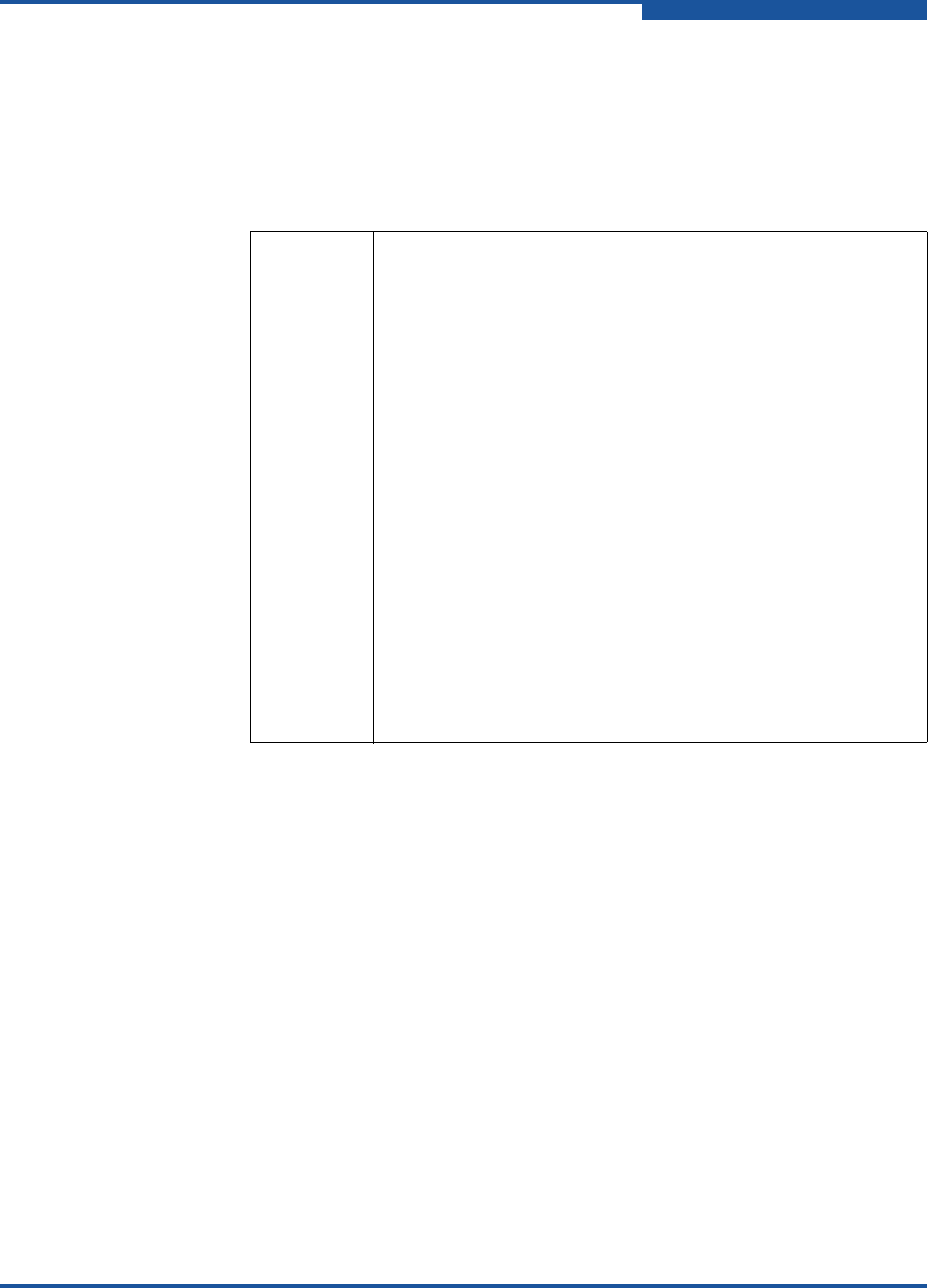
Adapter_1, and JBOD as members, as shown in the following table:
Observe the following rules:
Switch_1 and all devices and switches connected to Switch_1
must be included in the group even if the switch or devices does
not support authentication. Otherwise, the Switch_1 port will
become isolated.
You must specify adapters by node WWN. Switches can be
specified by port or node WWN. The type of switch WWN you
use in the switch security database must be the same as that in
the adapter security database. For example, if you specify a
switch with a port WWN in the switch security database, you
must also specify that switch in the adapter security database
with the same port WWN.
For CHAP authentication, create 32-character hexadecimal or
16-character ASCI secrets. The switch secret must be shared
with the adapter security database.
Switch_1 Node WWN: 10:00:00:c0:dd:07:e3:4c
Authentication: CHAP
Primary Hash: MD5
Primary Secret: 0123456789abcdef
Adapter_1 Node WWN: 10:00:00:c0:dd:07:c3:4d
Authentication: CHAP
Primary Hash: MD5
Primary Secret: fedcba9876543210
JBOD Node WWN: 10:00:00:d1:ee:18:d4:5e
Authentication: None
Node WWN: 10:00:00:d1:ee:18:d4:5f
Authentication: None
Node WWN: 10:00:00:d1:ee:18:d4:5g
Authentication: None