ADMINISTRATOR’S Guide
Contents
NAT with PPPoE Configuration Restarting the SonicWALL
Status CLI Support and Remote Management
Restrict Web Features 100
100
101
103
Viewing Network Access Rules 127 Services 128
Add a Known Service 130 Add a Custom Service
Delete a Service 131 Rules
Network Access Rule Logic List 133
Intranet Settings 151
Proxy Relay 148 Web Proxy Forwarding
149
Bypass Proxy Servers Upon Proxy Failure 149 Intranet 150
Allow Dhcp Pass Through in Standard Mode 166
Allow Dhcp Pass Through in Standard Mode 173
Configure Tab 181 Add/Modify IPSec Security Associations
166
Advanced Settings for VPN Configurations 191
Configuration Changes 228
Configuration Notes 233
190
SonicWALL Authentication Service 235
234
235
236
Limited Warranty
About this Guide
Organization of this Guide
SonicWALL Technical Support Firmware Version
Icons Used in this Manual
Introduction
Your SonicWALL Internet Security Appliance
Internet Security
Content Filtering
Logging and Reporting
IPSec VPN
Dynamic Host Configuration Protocol Dhcp
Easy Installation and Configuration
Configuring the Network Mode on the SonicWALL
Standard Mode
Network Address Translation NAT Enabled
NAT with PPPoE Client
Select Standard from the Network Addressing Mode menu
NAT with Dhcp Client
NAT with L2TP Client
NAT with Pptp Client
Configuring the SonicWALL in NAT Enabled Mode
Accessing the Wizard
Setting the Password
Connecting to the Internet
Selecting Your Internet Connection
Confirming Network Address Translation NAT Mode
Selecting NAT Enabled Mode
Configuring WAN Network Settings
Configuring LAN Network Settings
Configuration Summary
Congratulations
Configuring NAT with PPPoE Client
Restarting
Setting the Password
Connecting to the Internet
Setting the User Name and Password for PPPoE
Configuring the SonicWALL Dhcp Server
Congratulations
Configuring NAT with Dhcp Client
Accessing the Installation Wizard
Setting the Time and Date
Selecting Your Internet Connection
Configuring LAN Network Settings
Configuration Summary
Configuring NAT with L2TP Client
Configuring NAT with Pptp Client
Setting the Time and Date
Connecting to the Internet
Setting the User Name and Password for Pptp
Configuring the SonicWALL Dhcp Server
Congratulations
Logging into the SonicWALL Management Interface
Configuring the Network Mode on the SonicWALL
Registering at mySonicWALL.com
Creating a New User Account
Account Information
Personal Information
Registering at mySonicWALL.com
Page
Click Here Registration
Quick Registration
Status and Options
Managing Your SonicWALL
Renaming Your SonicWALL
Transferring a SonicWALL Product
Delete Product
Managing Services for SonicWALL Internet Security Appliances
Activating Services Using mySonicWALL.com
Registering at mySonicWALL.com
Configuring the TELE3 SP Modem Connection
Configuring the TELE3 SP WAN Failover Feature
Configuring Modem Profiles
Dial-Up Configuration
ISP Settings
Location Settings
Configuring the TELE3 SP Modem Connection
TELE3 SP Modem Configuration
Modem Settings
Failover Settings
Preempt Mode
Select Enable WAN Failover Select Enable Probing
Primary Interface
Configuring a Modem Profile for Manual Dial-Up
Configure Modem Settings
Select None as the Secondary Profile
Configuring the Modem Settings
Tested Internet Service Providers
Status
Modem Status
Chat Scripts
Custom Chat Scripts
Managing Your SonicWALL Internet Security Appliance
Https Management
Managing Your SonicWALL Internet Security Appliance
74 SonicWALL Internet Security Appliance User’s Guide
CLI Support and Remote Management
9600 bps Bits No parity No hand-shaking
General and Network Settings
Network Settings
Network Addressing Mode
Network Time Administrator
LAN Settings
Multiple LAN Subnet Mask Support
SonicWALL LAN IP Address
LAN Subnet Mask
WAN Settings
DNS Settings
WAN Gateway Router Address
WAN/LAN Subnet Mask
Standard Configuration
NAT Enabled Configuration
SonicWALL WAN Gateway Router Address is
NAT with Dhcp Client Configuration
NAT with PPPoE Configuration
Select NAT with PPPoE from the Network Addressing Mode menu
Restarting the SonicWALL
NAT with L2TP Client Configuration
Restarting the SonicWALL
NAT with Pptp Client Configuration
Restarting the SonicWALL
Setting the Time and Date
NTP Settings
Change the Administrator Password
Configuring the Administrator Settings
Administrator Name
Setting the Administrator Inactivity Timeout
Login Failure Handling
View Log
View Log Log Settings Reports
Logging and Alerts
SonicWALL Log Messages
TCP, UDP, or Icmp packets dropped
Web, FTP, Gopher, or Newsgroup blocked
ActiveX, Java, Cookie or Code Archive blocked
Log Settings
Configure the following settings
Page
Log Categories
VPN Tunnel Status
Alerts/SNMP Traps
Reports
Bandwidth Usage by IP Address
Bandwidth Usage by Service
Web Site Hits
SonicWALL ViewPoint
Content Filtering and Blocking
Configure URL List Customize Consent
Block
Configuring SonicWALL Content Filtering
Restrict Web Features
Message to display when a site is blocked
List Updates
URL List
Trusted Domains
Select Categories to Block
Settings
Download Automatically every
Customizing the Content Filtering List
Custom Filter
Time of Day
Filter Block Action
User Idle Timeout is 5 minutes configure here
Consent
Maximum Web usage
Consent page URL Optional Filtering
Mandatory Filtered IP Addresses
Consent Accepted URL Filtering Off
Consent Accepted URL Filtering On
Consent page URL Mandatory Filtering
Configuring N2H2 Internet Filtering
Trusted Domains
Settings Server Host Name or IP Address
N2H2 Server Status
Listen Port
Reply Port
Configuring the Websense Enterprise Content Filter
Trusted Domains
Configuring the Websense Content Filter List
Settings
Websense Server Status
Server Port
URL Cache
Restart Preferences Firmware Diagnostic
Web Management Tools
Exporting the Settings File
Preferences
Click Import in the Preferences tab
Importing the Settings File
Restoring Factory Default Settings
Updating Firmware
Updating Firmware Manually
Upgrade Features
Diagnostic Tools
DNS Name Lookup
Find Network Path
Select Ping from the Choose a diagnostic tool menu
Ping
Packet Trace
Select Packet Trace from the Choose a diagnostic tool menu
Tech Support Report
Generating a Tech Support Report
Trace Route
Network Access Rules
Viewing Network Access Rules
Services
LAN Out
Windows Networking NetBIOS Broadcast Pass Through
Network Connection Inactivity Timeout
Public LAN Server
Windows Messenger Support
Add a Custom Service
Add Service
Add a Known Service
Rules
Enable Logging
Delete a Service
Maximum Number of Rules by Product
Product Maximum Rules
Network Access Rule Logic List
Bandwidth Management
Add a New Rule
Select always from the Apply this rule menu
Blocking LAN Access for Specific Services
Add New Rule Examples
Enabling Ping
Select WAN from the Destination Ethernet menu
Current Network Access Rules Table
Enable/Disable a Rule
Restore the Default Network Access Rules
Edit a Rule
Understanding the Access Rule Hierarchy
Global User Settings
Users
Adding and Removing a User
Highlight -Add New User- in the Current User list box
Users Currently Locked Out After Login Failures
Current Users
User Login
Radius
Radius Servers
Radius Users
Radius Client Test
Management SonicWALL Snmp Support
Configuration of the Log/Log Settings for Snmp
Configuration of the Service and Rules Pages
SonicWALL Management Protocol
Additional Management
Network Access Rules
Advanced Features
Proxy Relay Web Proxy Forwarding
Configuring Web Proxy Relay
Bypass Proxy Servers Upon Proxy Failure
Installation
Intranet
Intranet Configuration
Intranet Settings
VPN Single-Armed Mode stand-alone VPN gateway
Remote SonicWALL Corporate SonicWALL
Configuring a SonicWALL for VPN Single Armed Mode
VPN Single Armed Mode SonicWALL
Routes
LAN Route Advertisement
Tip There is no route advertisement on the WAN
DMZ Addresses
RIPv2 Authentication
DMZ Route Advertisement
DMZ in Standard Mode
DMZ in NAT Mode
Delete a DMZ Address Range
HomePort Configuration
HomePort in Standard Mode
HomePort in NAT Mode
Delete a HomePort Address Range
Select the Enable One-to-One NAT check box
One-to-One NAT
One-to-One NAT Configuration Example
Select Enable One-to-One NAT and click Update
Ethernet
WAN Link Settings
Enable Bandwidth Management
DMZ/WorkPort Link Settings
LAN/HomePort Link Settings
MTU Settings
Proxy Management workstation ethernet address on WAN
SonicWALL Bandwidth Management
How SonicWALL Bandwidth Management Works
Rule Service Priority Guaranteed Maximum
Examples of Bandwidth Management Rules
Setup
Allow Dhcp Pass Through in Standard Mode
Setup Dhcp over VPN Status
Dhcp Server
Configuring the SonicWALL Dhcp Server
Select the Enable Dhcp Server
Dhcp over VPN
Dhcp Relay Mode
Deleting Dynamic Ranges and Static Entries
Select Central Gateway from the Dhcp Relay Mode menu
Configuring the Central Gateway for VPN over Dhcp
Configuring the Remote Gateway for VPN over Dhcp
Select Remote Gateway from the Dhcp Relay Mode menu
LAN IP Addresses
LAN Device Configuration
Dhcp Status
Dhcp Server on the SonicWALL TELE3 TZ and TZX
Configuring the SonicWALL Dhcp Server
Deleting Dynamic Ranges and Static Entries
Dhcp Status
SonicWALL VPN
Global VPN Settings
VPN Management Interface Summary Tab
Currently Active VPN Tunnels
VPN Bandwidth Management
VPN Policies
SonicWALL NAT Traversal Support
AES Advanced Encryption Standard Support
Configure Tab Add/Modify IPSec Security Associations
Disabling Security Associations
Security Policy Settings
Security Policy Settings for Group VPN
Security Policy Settings for IKE using Pre-shared Secret
AES support is available only on the PRO 230 and PRO
Security Policy Settings using Manual Key
Accessing Remote Resources across a Virtual Private Network
Destination Networks
Adding Destination Networks
Modifying and Deleting Existing Security Associations
Try to bring up all possible SAs
Advanced Settings
Enable Keep Alive
Require authentication of local users
Require authentication of remote users
Enable Windows Networking NetBIOS broadcast
Apply NAT and firewall rules
Enable Perfect Forward Secrecy
Phase 2 DH Group
Default LAN Gateway
Route all internet traffic through this SA
VPN Terminated at the LAN, DMZ, or LAN/DMZ
Advanced Settings for VPN Configurations
IKE using
Configuring SonicWALL VPN
SonicWALL VPN
Page
Group VPN Client Configuration
Group VPN Client Setup
Installing the VPN Client Software
Page
SonicWALL VPN
Verifying the VPN Tunnel as Active
SonicWALL VPN
Configuring the VPN Client
Launching the SonicWALL VPN Client
Configuring VPN Security and Remote Identity
Select the Connect using Secure Gateway Tunnel check box
Select None from the Select Certificate menu
Configuring VPN Client Identity
Configuring VPN Client Security Policy
Configuring VPN Client Key Exchange Proposal
Select the Encapsulation Protocol ESP check box
Configuring Inbound VPN Client Keys
Configuring Outbound VPN Client Keys
Saving SonicWALL VPN Client Settings
Click Inbound Keys. The Inbound Keying Material box appears
Verifying the VPN Client Icon in the System Tray
IKE and Manual Key Configuration for Two SonicWALLs
Manual Key for Two SonicWALLs
SonicWALL VPN
Select Strong Encrypt ESP 3DES as the Encryption Method
Configuring the Second SonicWALL Appliance
Example of Manual Key Configuration for Two SonicWALLs
Configuring the Remote SonicWALL
Enter the Encryption Key from the Main Office configuration
Page
IKE Configuration for Two SonicWALLs
Select Group 1 from the Phase 1 DH Group menu
Page
Select 3DES & SHA1 from the Phase 1 DH Group menu
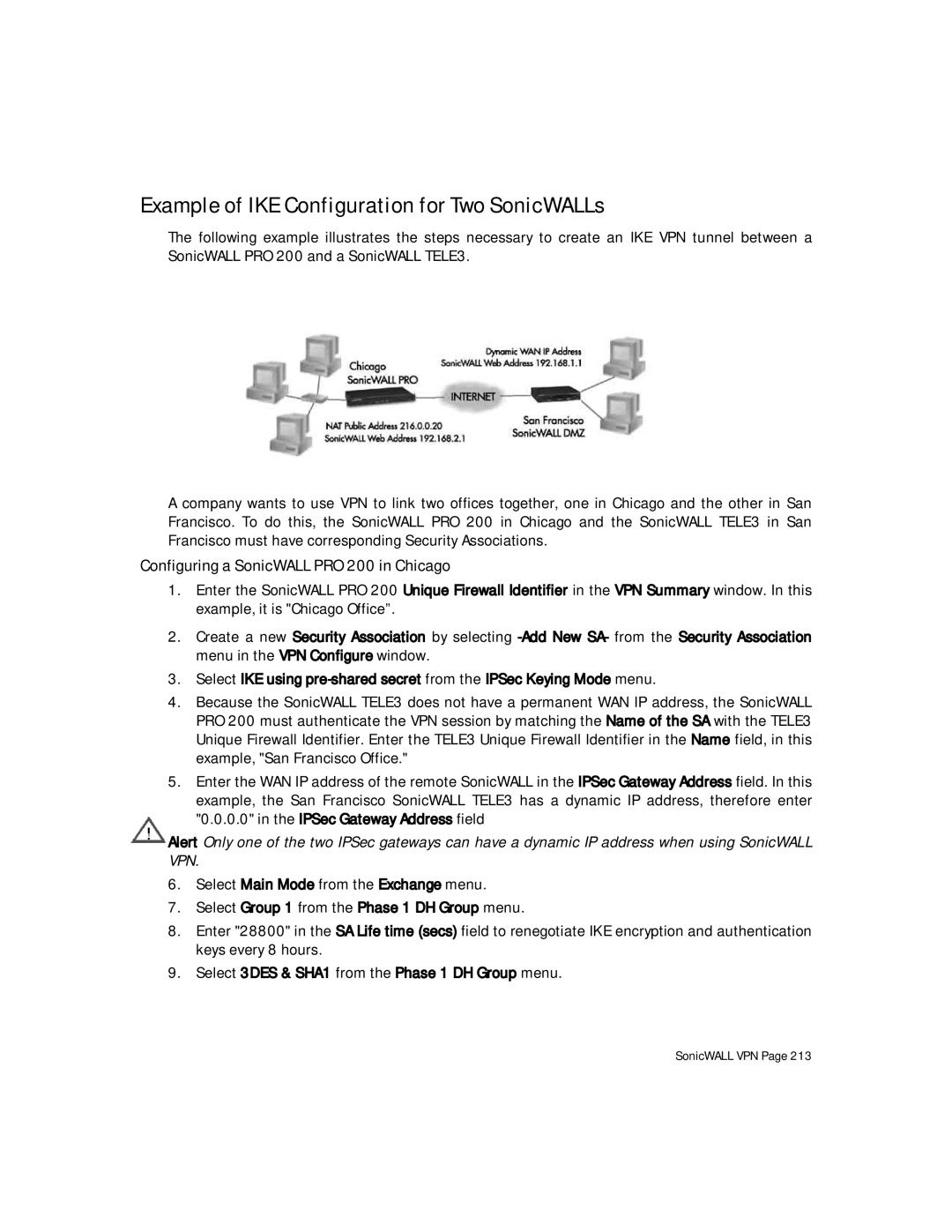
Example of IKE Configuration for Two SonicWALLs
Configuring a SonicWALL PRO 200 in Chicago
Configuring a SonicWALL TELE3 in San Francisco
Select Group 2 from the Phase 1 DH Group menu
SonicWALL Third Party Digital Certificate Support
VeriSign Entrust
Overview of Third Party Digital Certificate Support
Version 3 Certificate Standard
Importing CA Certificates into the SonicWALL
Certificate Details
Importing Certificate with private key
Certificate Revocation List CRL
Creating a Certificate Signing Request
Importing a Signed Local Certificate
Click VPN, then Local Certificates
Click Import Certificate
SonicWALL Enhanced VPN Logging
Testing a VPN Tunnel Connection Using Ping
Configuring Windows Networking
SonicWALL VPN
Page
High Availability
Before Configuring High Availability
Network Configuration for High Availability Pair
Configuring High Availability on the Primary SonicWALL
High Availability
Configuration Changes
High Availability Status
High Availability Status Window
Mail Alerts Indicating Status Change
Forcing Transitions
Configuration Notes
SonicWALL Network Anti-Virus
SonicWALL Options and Upgrades
SonicWALL VPN Client
SonicWALL Authentication Service
Content Filter List Subscription
Vulnerability Scanning Service
Contact Your Reseller or SonicWALL
SonicWALL ViewPoint Reporting
SonicWALL Global Management System
SonicWALL PRO 230 and PRO 330 Front Panel Description
Hardware Descriptions
SonicWALL PRO 230 and PRO 330 Front Panel
Reset Switch
Power Switches
Power Inputs
SonicWALL PRO 230 and PRO 330 Rear Panel Description
SonicWALL PRO 200 and PRO 300 Front Panel
SonicWALL PRO 200 and PRO 300 Front Panel Description
Power Input
Power Switch
SonicWALL PRO 200 and PRO 300 Back Panel
SonicWALL PRO 200 and PRO 300 Back Panel Description
100
SonicWALL PRO 100 Front Panel
SonicWALL PRO 100 Front Panel Description
SonicWALL PRO 100 Back Panel
SonicWALL PRO 100 Back Panel Description
Modem
SonicWALL TELE3 SP Front Panel
SonicWALL TELE3 SP Front Panel Description
CLI Command Line Interface Port
SonicWALL TELE3 SP Back Panel
SonicWALL TELE3 SP Back Panel Description
TELE3 SP Modem Port
SonicWALL TELE3 TZ Front Panel
SonicWALL TELE3 TZ Front Panel Description
SonicWALL TELE3 TZ Back Panel
SonicWALL TELE3 TZ Back Panel Description
SonicWALL TELE3 TZX Front Panel
SonicWALL TELE3 TZX Front Panel Description
SonicWALL TELE3 TZX Back Panel l
SonicWALL TELE3 TZX Back Panel Description
SonicWALL SOHO3 and TELE3 Front Panel
SonicWALL SOHO3 and TELE3 Front Panel Description
SonicWALL SOHO3 and TELE3 Back Panel
SonicWALL SOHO3 and TELE3 Back Panel Description
SonicWALL GX 250 and GX 650 Front Panel
SonicWALL GX250 and GX 650 Front Panel Description
SonicWALL GX250 Front Panel
SonicWALL GX 650 Front Panel
Alarm Reset Button
SonicWALL GX 250 and GX 650 Back Panel Description
Troubleshooting Guide
Computer on the LAN cannot access the Internet
SonicWALL does not establish authenticated sessions
Link LED is off
Duplicate IP address errors
VPN tunnel problems
SonicWALL does not save changes that you have made
Machines on the WAN are not reachable
Appendix a Technical Specifications
Appendices
Appendix B SonicWALL Support Solutions
Knowledge Base
Internet Security Expertise
SonicWALL Support
SonicWALL Support Services Features and Benefits
SonicWALL Super SonicWALL Warranty Support
Warranty Support North America
Warranty Support International
SonicWALL Support
SonicWALL Support
Appendix C Introduction to Networking
Network Hardware Components
Network Types
Firewalls
Network Protocols
IP Address
IP address Subnet mask Default gateway
IP Addressing
Default Gateway
Network Address Translation NAT
Nodes
Subnet Mask
Appendices
Registered Port Numbers
Appendix D IP Port Numbers
Well Known Port Numbers
Windows
Appendix E Configuring TCP/IP Settings
Click DNS Configuration
Windows NT
Windows
Windows XP
Open the Local Area Connection Properties window
Macintosh OS
Appendix F Basic VPN Terms and Concepts
Authentication Header AH
Internet Key Exchange IKE
Manual Key
Shared Secret
Page
Data Encryption Standard DES
ARCFour
Strong Encryption Triple DES
Security Parameter Index SPI
Erasing the Firmware for all Models
Locating the Reset button on your SonicWALL
Appendix G- Erasing the Firmware
Appendix H- Mounting the SonicWALL PRO 200 and PRO
Appendix I Configuring Radius and ACE Servers
Steel Belted Radius Funk Software
ACE Server RSA
Configuring User Privileges
Open the ACE Server Database Administrator program
ACS Server Cisco
Internet Authentication Service Windows NT/2000 Server
Open IAS, and select Remote Access Policies
Radius Attributes Dictionary
Page
Appendices
Page
Appendices
Page
Appendices
Index
Dynamic Host Configuration Protocol Dhcp Dynamic Ranges 167
Page
Index
232- 000291 Rev a 11