4.It may take more time for https connection than that for http connection, because https connection involves authentication, encryption and decryption etc.
4.4.3 SSH Config
As stipulated by IFTF (Internet Engineering Task Force), SSH (Secure Shell) is a security protocol established on application and transport layers.
Comprising server and client, SSH has two versions, V1 and V2 which are not compatible with each other. In the communication, SSH server and client can
SSH key can be downloaded into the switch. If the key is successfully downloaded, the certificate authentication will be preferred for SSH access to the switch.
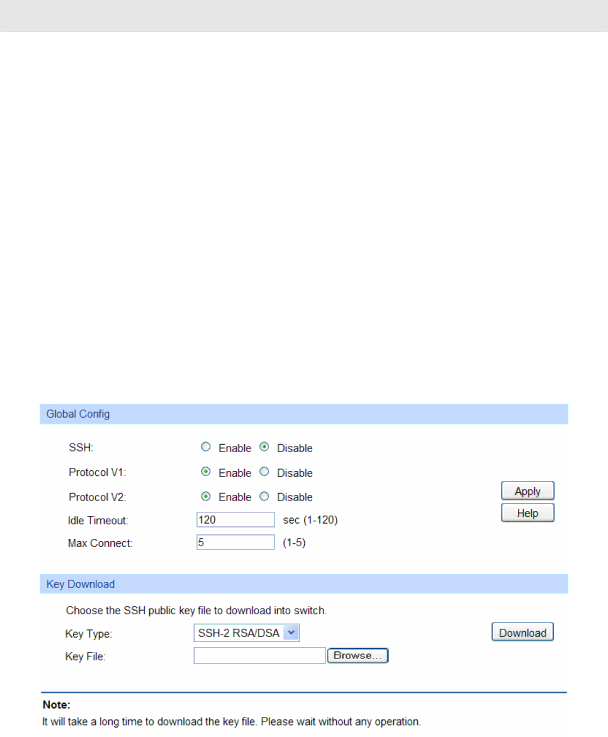
Choose the menu System→Access Security→SSH Config to load the following page.
Figure 4-17 SSH Config
The following entries are displayed on this screen:
¾Global Config
SSH: | Select Enable/Disable SSH function. |
Protocol V1:Select Enable/Disable SSH V1 to be the supported protocol.
Protocol V2:Select Enable/Disable SSH V2 to be the supported protocol.
22
