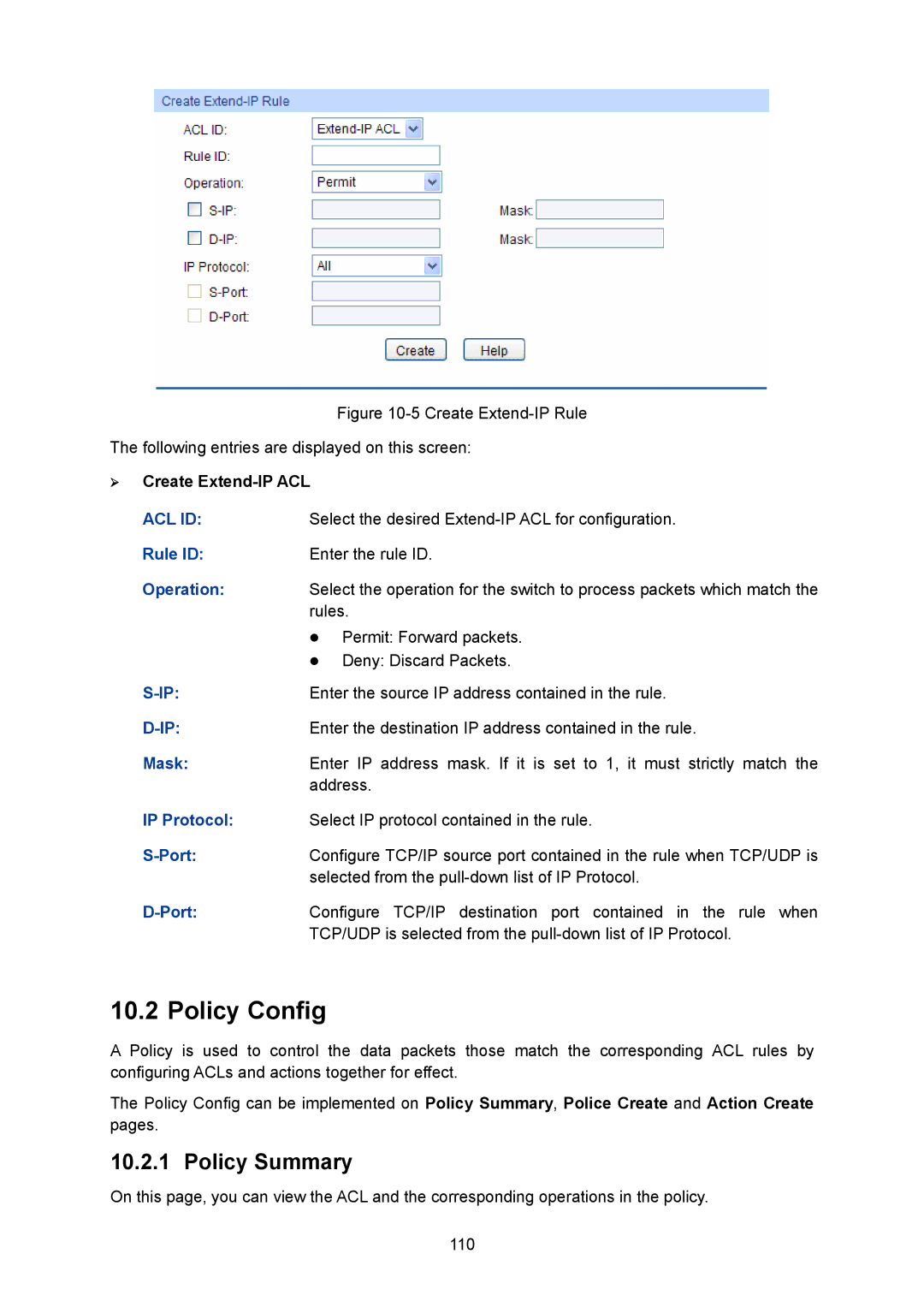
Figure 10-5 Create Extend-IP Rule
The following entries are displayed on this screen:
¾Create Extend-IP ACL
ACL ID: | Select the desired | |
Rule ID: | Enter the rule ID. | |
Operation: | Select the operation for the switch to process packets which match the | |
| rules. | |
| z | Permit: Forward packets. |
| z | Deny: Discard Packets. |
Enter the source IP address contained in the rule. | ||
Enter the destination IP address contained in the rule. | ||
Mask: | Enter IP address mask. If it is set to 1, it must strictly match the | |
| address. | |
IP Protocol: | Select IP protocol contained in the rule. | |
| Configure TCP/IP source port contained in the rule when TCP/UDP is | |
| selected from the | |
| Configure TCP/IP destination port contained in the rule when | |
| TCP/UDP is selected from the | |
10.2 Policy Config
A Policy is used to control the data packets those match the corresponding ACL rules by configuring ACLs and actions together for effect.
The Policy Config can be implemented on Policy Summary, Police Create and Action Create pages.
10.2.1 Policy Summary
On this page, you can view the ACL and the corresponding operations in the policy.
110