TL-SG3216/TL-SG3424 JetStream L2 Lite Managed Switch
Copyright & Trademarks
Contents
Gvrp
100
VII
NDP
Package Contents
Conventions
About this Guide
Intended Readers
Overview of This Guide
System Switching Vlan Spanning Tree Multicast
QoS ACL Network Security Snmp Cluster
Return to Contents
Overview of the Switch
Main Features
Introduction
Appearance Description
Front Panel
¾ LEDs Name Status Indication
Rear Panel
Login to the Switch
Login
Configuration
Return to Contents
System Summary
System
System Info
¾ Port Status
Rate
Port
Type
Status
Device Description
System Time
¾ Device Description
Synchronize With
Current System
Get GMT
PC’S Clock
¾ IP Config
System IP
User Config
User Manage
User Table
User Status
User ID, Name, Access Level and status Operation
¾ User Info
¾ User Table
¾ Config Restore
Config Restore
Config Backup
System Tools
Firmware Upgrade
¾ Config Backup
System Reset
Access Security
System Reboot
Access Control
IP Address&Mask
¾ Access Control Config
¾ Session Config
MAC Address
SSL Config
¾ Access User Number
¾ Certificate Download
SSH Config
¾ Global Config
¾ Key Download
Idle Timeout
Protocol
Max Connect
Download
¾ Configuration Procedure
Key Type
¾ Network Requirements
Application Example 2 for SSH
Page
Return to Contents
Port
Switching
Port Config
Port Select
Speed and Duplex
Port Mirror
Description
Flow Control
Mirroring
Mirror Mode
Group
Mode
Port Security
¾ Port Security
LAG
Max Learned MAC
Learned Num
¾ LAG Table
LAG Table
Aggregate Arithmetic
Group Number
Static LAG
Detail Information
Lacp Config
¾ LAG Config
LAG will delete this LAG
System Priority
¾ Lacp Config
Admin Key
Port Priority
Traffic Monitor
Traffic Summary
¾ Auto Refresh
Traffic Statistics
MAC Address
Way
Address Table
Bound MAC address
Port
¾ Search Option
¾ Address Table
Displays the corresponding Vlan ID of the MAC address
MAC Address Displays the MAC address learned by the switch
Static Address
¾ Create Static Address
Dynamic Address
¾ Static Address Table
¾ Aging Config
¾ Dynamic Address Table
Filtering Address
Bind
¾ Create Filtering Address
¾ Filtering Address Table
Vlan
802.1Q Vlan
¾ Link Types of ports
¾ Pvid
Vlan ID Select
Vlan Config
¾ Vlan Table
Description :
Is valid or not
¾ Vlan Config
Enter the ID number of Vlan
¾ Vlan Members
¾ Vlan Port Config
Port Displays the port number
¾ Vlan of Port
Required. On the VLAN→802.1Q VLAN→Port Config page, set
Required. On the VLAN→802.1Q VLAN→VLAN Config
Vlan Description
VLAN→VLAN Config
MAC Vlan
MAC Select
Protocol Vlan
¾ MAC Vlan Table
Step Operation Description
¾ The Procedure for the Switch to Identify Packet Protocol
¾ Encapsulation Format of Ethernet Data
802.3 raw 802.2 LLC Snap Protocol
¾ The Implementation of Protocol Vlan
Encapsulation
Vlan packets are processed in the following way
Protocol Group Table
Protocol Group
¾ Protocol Group Table
¾ Protocol Group Config
Protocol Template
¾ Protocol Group Member
Application Example for 802.1Q Vlan
¾ Network Diagram ¾ Configuration Procedure
Required. On VLAN→802.1Q VLAN→Port Config page, configure
Required. On VLAN→802.1Q VLAN→VLAN Config page, create a
Application Example for MAC Vlan
¾ Network Diagram
Application Example for Protocol Vlan
Required. On VLAN→Protocol VLAN→Protocol Template
Gvrp
On VLAN→Protocol VLAN→Protocol Group page, create protocol
¾ Gvrp
¾ Port Config
Select Port Status Registration Mode
Configuration Procedure
Spanning Tree
¾ STP Elements
¾ STP Timers
¾ Bpdu Comparing Principle in STP mode
¾ STP Generation
Step Operation
Tips :
¾ Rstp Elements
¾ Mstp Elements
¾ Port States
¾ Port Roles
STP Config
STP Config
Hello Time
Forward Delay
Version
Max Age
Port Config
STP Summary
IntPath
Priority
ExtPath
Edge Port
Region Config
Mstp Instance
Port Status
Instance Config
¾ Region Config
Instance
Instance Port Config
¾ Instance Table
Clear
Instance ID
Path Cost
Port Role
STP Security
Port Protect
¾ TC Protect
¾ Bpdu Protect
¾ Bpdu Filter
TC Protect
Loop Protect
Root Protect
Bpdu Protect
Application Example for STP Function
TC Protect
On Spanning Tree→STP Config→STP Config
On Spanning Tree→STP Config→Port Config
On Spanning Tree→MSTP Instance→Instance
Configure Switch D
¾ Suggestion for Configuration
Multicast
¾ Multicast Overview
¾ Multicast Address
¾ Multicast Address Table
Multicast IP Port
¾ Igmp Snooping Process
Igmp Snooping
¾ Igmp Snooping
¾ Igmp Messages
Snooping Config
¾ Igmp Snooping Fundamentals
¾ Igmp Snooping Status
Description Displays Igmp Snooping status Member
Igmp Snooping
Fast Leave
Leave Time
Router Port Time
Member Port Time
Static Router Port
Multicast Vlan
Snooping→Snooping Config and Port Config
Multicast→IGMP Snooping→VLAN Config
Displays the Vlan ID
¾ Multicast Vlan
On the Multicast→IGMP Snooping→Snooping Config
Vlan
Multicast→IGMP Snooping→Multicast Vlan
Snooping→Snooping Config
¾ Configuration Procedure Step Operation Description
Snooping→Port Config
Multicast IP
Multicast IP Table
Static Multicast IP
Multicast Filter
¾ Create Static Multicast
¾ Static Multicast IP Table
Start Multicast IP
IP-Range
IP Range ID
End Multicast IP
Port Filter
¾ Port Filter Config
Action Mode
Filter
Displays the LAG number which the port belongs to
Packet Statistics
Ports taking up too much bandwidth
Multicast→Multicast Filter→IP-Range
¾ Igmp Statistics
¾ Priority Mode
QoS
¾ QoS
¾ Schedule Mode
802.1Q frame
SP-Mode
¾ Port Priority Config
DiffServ
Port Priority
¾ Schedule Mode Config
Schedule Mode
Required. On QoS→DiffServ→Schedule Mode
Required. On QoS→DiffServ→Port Priority
3 802.1P Priority
Dscp Priority
¾ Priority Level
¾ Dscp Priority Config
Required. On QoS→DiffServ→DSCP Priority
¾ Rate Limit Config
Bandwidth Control
Rate Limit
¾ Storm Control Config
Storm Control
Bps
Voice Vlan
Broadcast Rate
Mulitcast Rate
¾ Security Mode of Voice Vlan
TAG
Global Config
Security Packet Type Processing Mode
Enter the Vlan ID of the voice Vlan
Select the desired port for voice Vlan configuration. It is
OUI Config
Configuration Procedure of Voice Vlan
Displays the OUI address of the voice device
Time-Range Summary
ACL
Time-Range
Index
Time-Range Create
¾ Create Holiday
ACL Config
Holiday Config
¾ Holiday Table
¾ Rule Table
ACL Summary
ACL Create
¾ Create ACL
Rule ID
MAC ACL
¾ Create MAC ACL
EtherType
¾ Create Standard-IP ACL
Standard-IP ACL
Extend-IP ACL
Time-Range
¾ Create Extend-IP ACL
IP Protocol
TCP Flag :
Policy Config
Policy Summary
¾ Create Policy
Policy Create
Action Create
¾ Create Action
Policy Binding
Binding Table
Port Binding
Vlan Binding
Direction Displays the binding direction
Enter the ID of the Vlan you want to bind
¾ VLAN-Bind Config
Application Example for ACL
¾ VLAN-Bind Table
On ACL→ACL Config→ACL Create page, create ACL
On ACL→ACL Config→Standard-IP ACL page, select ACL
Network Security
IP-MAC Binding
Manual Binding
Protect Type Select the Protect Type for the entry
¾ Manual Binding Option
Enter the Vlan ID
¾ Manual Binding Table
ARP Scanning
End IP Address
Dhcp Snooping
Start IP Address
Scan
Network diagram for DHCP-snooping implementation
¾ Dhcp Working Principle
¾ Option
Dhcp Cheating Attack Implementation Procedure
¾ Dhcp Cheating Attack
¾ Dhcp Snooping Config
¾ Option 82 Config
¾ Port Config Port Select
Customization Circuit ID Remote ID
ARP Inspection
¾ Imitating Gateway
¾ Cheating Gateway
10 ARP Attack Cheating Gateway
¾ Cheating Terminal Hosts
¾ Man-In-The-Middle Attack
¾ ARP Flooding Attack
ARP Detect
¾ ARP Detect
¾ Trusted Port
ARP Defend
Required. On the Network Security→IP-MAC
Network Security→ARP
Defend
ARP Statistics
¾ ARP Defend
Speed
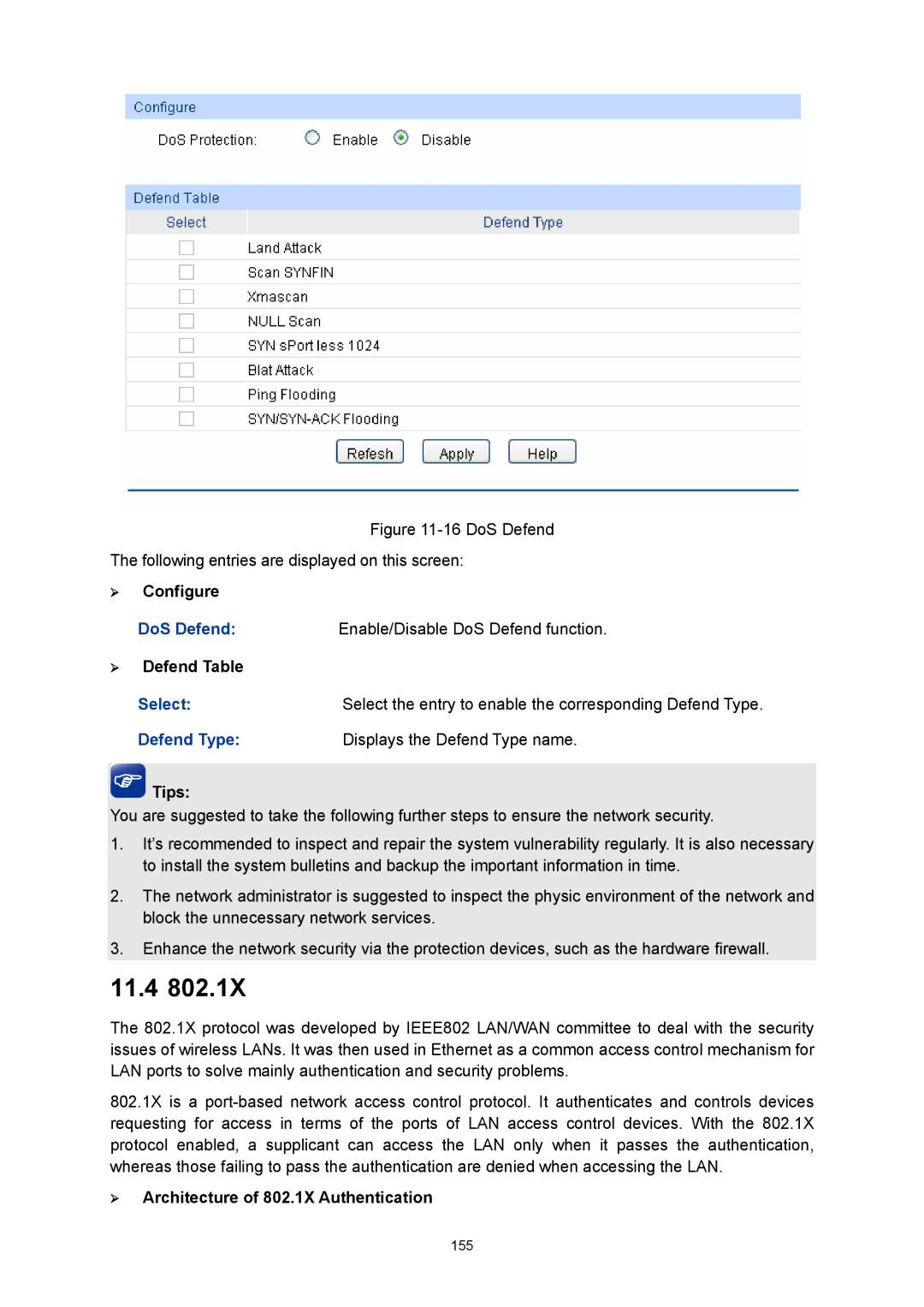
DoS Defend
¾ Illegal ARP Packet
DoS Attack Type Description
11.4
¾ Configure
¾ Architecture of 802.1X Authentication
¾ Defend Table
¾ The Mechanism of an 802.1X Authentication System
¾ 802.1X Authentication Procedure
¾ 802.1X Timer
¾ Guest Vlan
Guest Vlan
Authentication Method
802.1X
Guest Vlan ID
Supplicant Timeout
Server Timeout
Retry Times
Control Type
Control Mode
Radius Server
Authorized
On the Network Security→802.1X→Global Config
Required. On the Network Security→802.1X→Radius
Required. On the Network Security→802.1X→Port
¾ Snmp Management Frame
Snmp
¾ Snmp Overview
¾ Snmp Versions
¾ Snmp Configuration Outline
¾ MIB Introduction
Snmp Config
¾ Local Engine
¾ Remote Engine
View Type
Snmp View
MIB Object ID
View Name
¾ Group Config
Snmp Group
Snmp User
¾ Group Table
Privacy Mode
Auth Mode
Auth Password
Privacy Password
¾ Community Config
Access
Snmp Community
MIB View
Required. On the SNMP→SNMP Config→Global
Required. On the SNMP→SNMP Config→SNMP
¾ Community Table
On the SNMP→SNMP Config→SNMP
Notification
User
Timeout
UDP Port
Retry
Rmon
¾ Rmon Group
Rmon Group Function
Event Config
History Control
¾ History Control Table
Alarm Config
¾ Event Table
Rising Threshold
Variable
Sample Type
Rising Event
179
Cluster
¾ Cluster Role
13.1 NDP
Neighbor Info
¾ Introduction to Cluster
NDP Summary
¾ Neighbor
¾ Neighbor Info
¾ Port Status Displays the port number of the switch
NDP
Disable
NDP Config
Enable
¾ Global Cofig
Device MAC
Ntdp
Device Table
Cluster Name
Neighbor Info
Ntdp Summary
Hops
Collect Topology
Ntdp Config
Port Displays the port number of the switch
Ntdp Interval Time
Ntdp Hop Delay
Ntdp Port Delay
Ntdp Hops
¾ Global
Cluster
Cluster Summary
Cluster
Cluster Config
¾ Global Config Cluster
¾ Current Role
¾ Role Change
Application Example for Cluster Function
On Cluster→NDP→NDP Config page, enable NDP
On Cluster→NTDP→NTDP Config page, enable
194
Maintenance
System Monitor
CPU Monitor
Memory Monitor
14.2 Log
Log Table
Local Log
Log Buffer
¾ Local Log Config
Remote Log
Log File
Backup Log
¾ Log Host
Host IP
Cable Test
Error
Device Diagnose
Pair
Loopback
Switch is available
Network Diagnose
Ping
¾ Ping Config
Tracert
¾ Tracert Config
10 Tracert Following entries are displayed on this screen
Appendix a Specifications
Appendix B Configuring the PCs
207
Now
Appendix C Load Software using FTP
Hardware Installation
Configure the Hyper Terminal
210
Download Firmware via bootUtil menu
Figure C-5 Port Settings
TP-LINK upgrade You can only use the port 1 to upgrade
Are you want to upgrade the firmwareY/N y
TP-LINK start Start
User
Installation Guide
Appendix D 802.1X Client Software
215
216
Uninstall Software
Figure D-7 InstallShield Wizard Complete
Configuration
Figure D-11 Uninstall Complete
219
FAQ
Figure D-16 Connection Status
221
Appendix E Glossary
Ieee 802.1D
Multicast Switching
Group Attribute Registration Protocol Garp
Ieee 802.1Q
Link Aggregation
Port Authentication
Remote Authentication Dial-in User Service Radius
Link Aggregation Control Protocol Lacp
Spanning Tree Algorithm STA
Simple Network Management Protocol Snmp
Simple Network Time Protocol Sntp
Telnet

 Tips:
Tips: