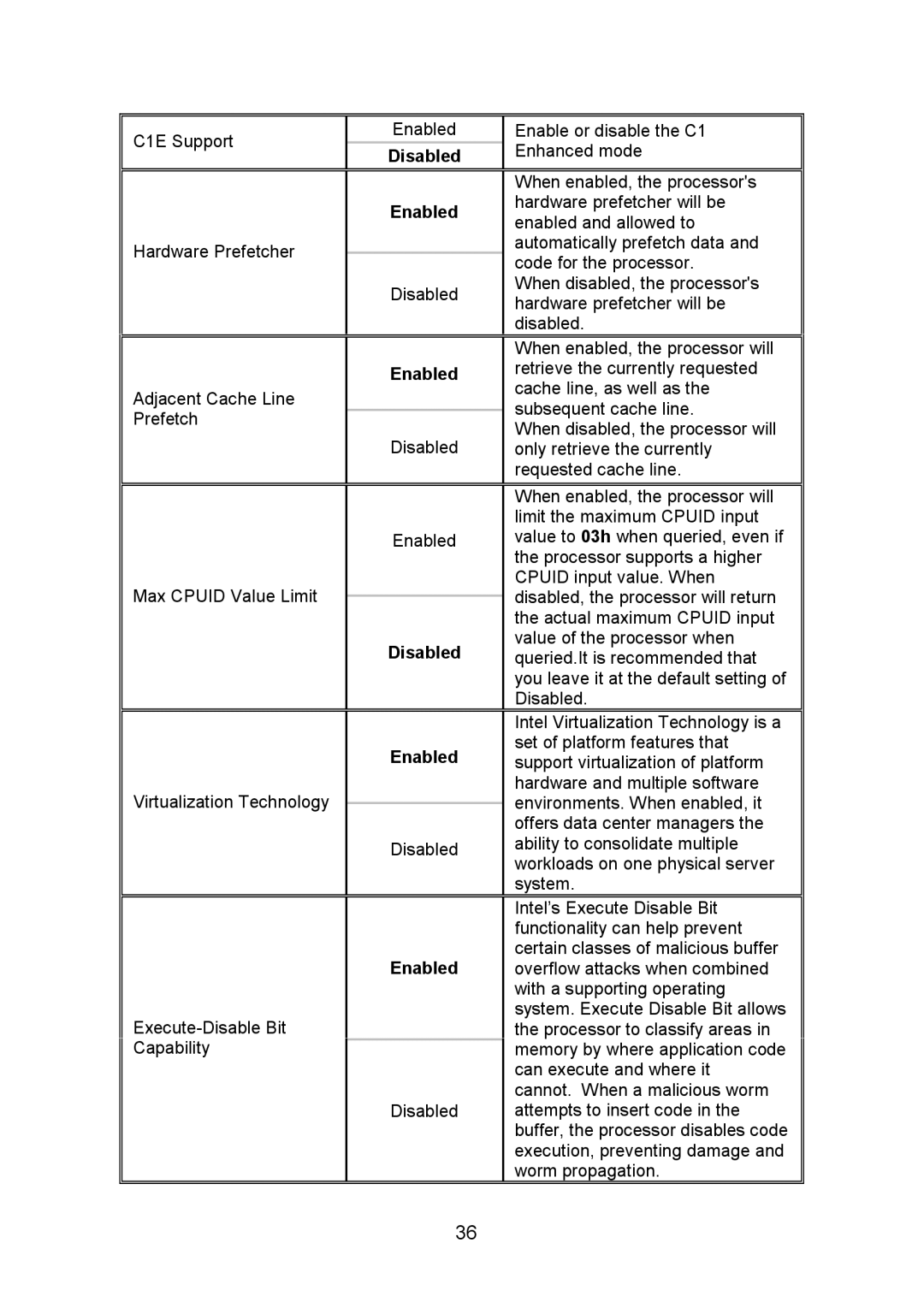
C1E Support | Enabled | Enable or disable the C1 | |
Disabled | Enhanced mode | ||
| |||
|
| When enabled, the processor's | |
| Enabled | hardware prefetcher will be | |
| enabled and allowed to | ||
|
| ||
Hardware Prefetcher |
| automatically prefetch data and | |
| code for the processor. | ||
|
| ||
| Disabled | When disabled, the processor's | |
| hardware prefetcher will be | ||
|
| ||
|
| disabled. | |
|
| When enabled, the processor will | |
| Enabled | retrieve the currently requested | |
Adjacent Cache Line |
| cache line, as well as the | |
| subsequent cache line. | ||
Prefetch |
| ||
| When disabled, the processor will | ||
| Disabled | ||
| only retrieve the currently | ||
|
| requested cache line. | |
|
| When enabled, the processor will | |
|
| limit the maximum CPUID input | |
| Enabled | value to 03h when queried, even if | |
|
| the processor supports a higher | |
Max CPUID Value Limit |
| CPUID input value. When | |
| disabled, the processor will return | ||
| |||
|
| the actual maximum CPUID input | |
| Disabled | value of the processor when | |
| queried.It is recommended that | ||
|
| you leave it at the default setting of | |
|
| Disabled. | |
|
| Intel Virtualization Technology is a | |
| Enabled | set of platform features that | |
| support virtualization of platform | ||
Virtualization Technology |
| hardware and multiple software | |
| environments. When enabled, it | ||
| |||
|
| offers data center managers the | |
| Disabled | ability to consolidate multiple | |
| workloads on one physical server | ||
|
| ||
|
| system. | |
|
| Intel’s Execute Disable Bit | |
|
| functionality can help prevent | |
| Enabled | certain classes of malicious buffer | |
| overflow attacks when combined | ||
|
| with a supporting operating | |
| system. Execute Disable Bit allows | ||
| the processor to classify areas in | ||
Capability |
| memory by where application code | |
|
| can execute and where it | |
|
| cannot. When a malicious worm | |
| Disabled | attempts to insert code in the | |
|
| buffer, the processor disables code | |
|
| execution, preventing damage and | |
|
| worm propagation. |
36