Connection Methods
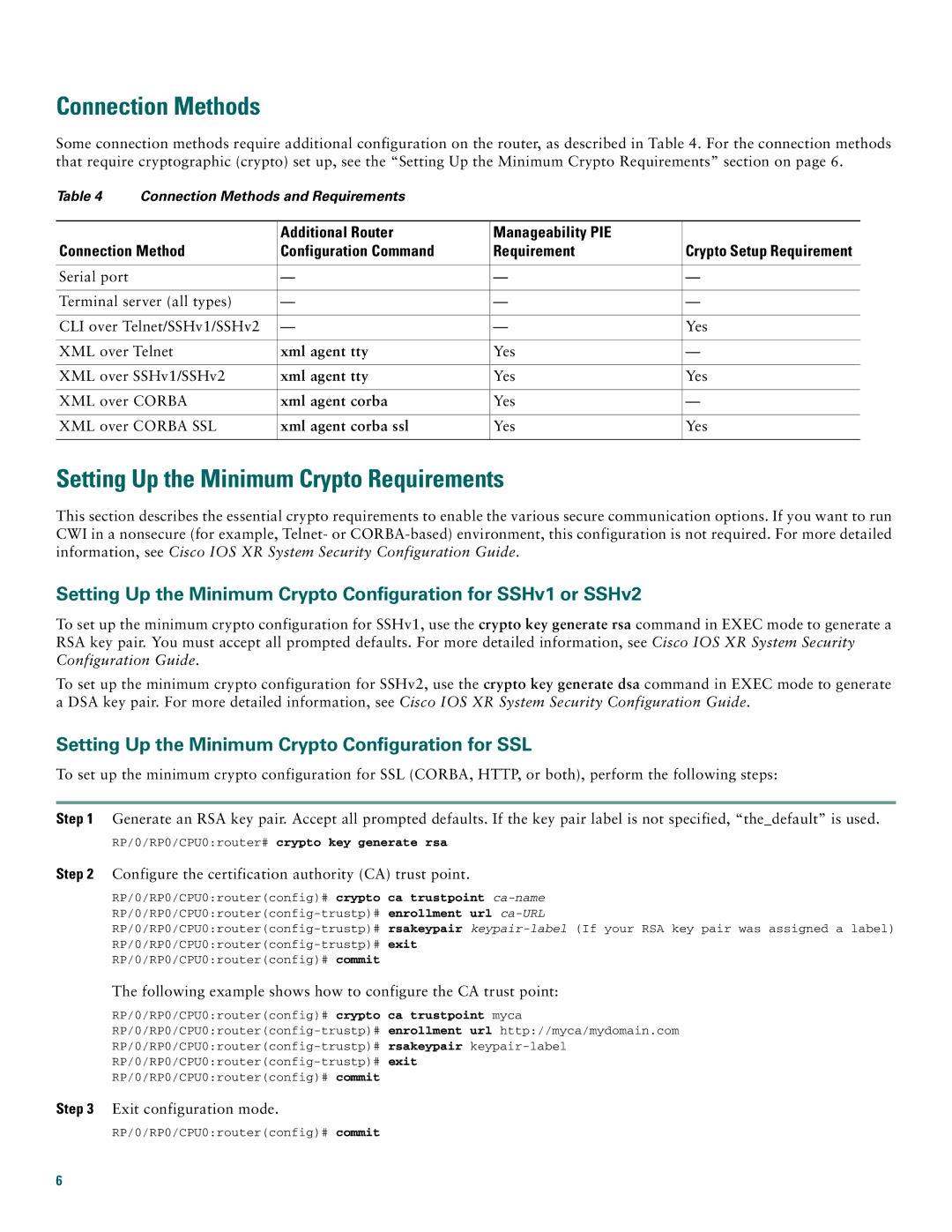
Some connection methods require additional configuration on the router, as described in Table 4. For the connection methods that require cryptographic (crypto) set up, see the “Setting Up the Minimum Crypto Requirements” section on page 6.
Table 4 | Connection Methods and Requirements |
|
| |
|
|
|
|
|
|
| Additional Router | Manageability PIE |
|
Connection Method | Configuration Command | Requirement | Crypto Setup Requirement | |
|
|
|
|
|
Serial port |
| — | — | — |
|
|
|
| |
Terminal server (all types) | — | — | — | |
|
|
|
| |
CLI over Telnet/SSHv1/SSHv2 | — | — | Yes | |
|
|
|
| |
XML over Telnet | xml agent tty | Yes | — | |
|
|
|
| |
XML over SSHv1/SSHv2 | xml agent tty | Yes | Yes | |
|
|
|
| |
XML over CORBA | xml agent corba | Yes | — | |
|
|
|
| |
XML over CORBA SSL | xml agent corba ssl | Yes | Yes | |
|
|
|
|
|
Setting Up the Minimum Crypto Requirements
This section describes the essential crypto requirements to enable the various secure communication options. If you want to run CWI in a nonsecure (for example, Telnet- or
Setting Up the Minimum Crypto Configuration for SSHv1 or SSHv2
To set up the minimum crypto configuration for SSHv1, use the crypto key generate rsa command in EXEC mode to generate a RSA key pair. You must accept all prompted defaults. For more detailed information, see Cisco IOS XR System Security Configuration Guide.
To set up the minimum crypto configuration for SSHv2, use the crypto key generate dsa command in EXEC mode to generate a DSA key pair. For more detailed information, see Cisco IOS XR System Security Configuration Guide.
Setting Up the Minimum Crypto Configuration for SSL
To set up the minimum crypto configuration for SSL (CORBA, HTTP, or both), perform the following steps:
Step 1 Generate an RSA key pair. Accept all prompted defaults. If the key pair label is not specified, “the_default” is used.
RP/0/RP0/CPU0:router# crypto key generate rsa
Step 2 Configure the certification authority (CA) trust point.
RP/0/RP0/CPU0:router(config)# crypto ca trustpoint
RP/0/RP0/CPU0:router(config)# commit
The following example shows how to configure the CA trust point:
RP/0/RP0/CPU0:router(config)# crypto ca trustpoint myca
RP/0/RP0/CPU0:router(config)# commit
Step 3 Exit configuration mode.
RP/0/RP0/CPU0:router(config)# commit
6