VPN Sample Configuration with Network Extension Mode
Configuring Authentication (AAA)
Configure an AAA user and DEFAULT AAA group for remote users. When an ANG tunnels into the XSR, it will be assigned dynamically to the IP pool AUTH. Be aware that groups must be created before users can be added to them. Remember to create the same users and passwords on the ANG. The IP address assigned to the AAA user is the remote gatewayIP address.
XSR(config)#ip local pool AUTH 192.168.2.0 255.255.255.0
XSR(config)#aaa user 112.16.244.9
VPN Sample Configuration with Network Extension Mode
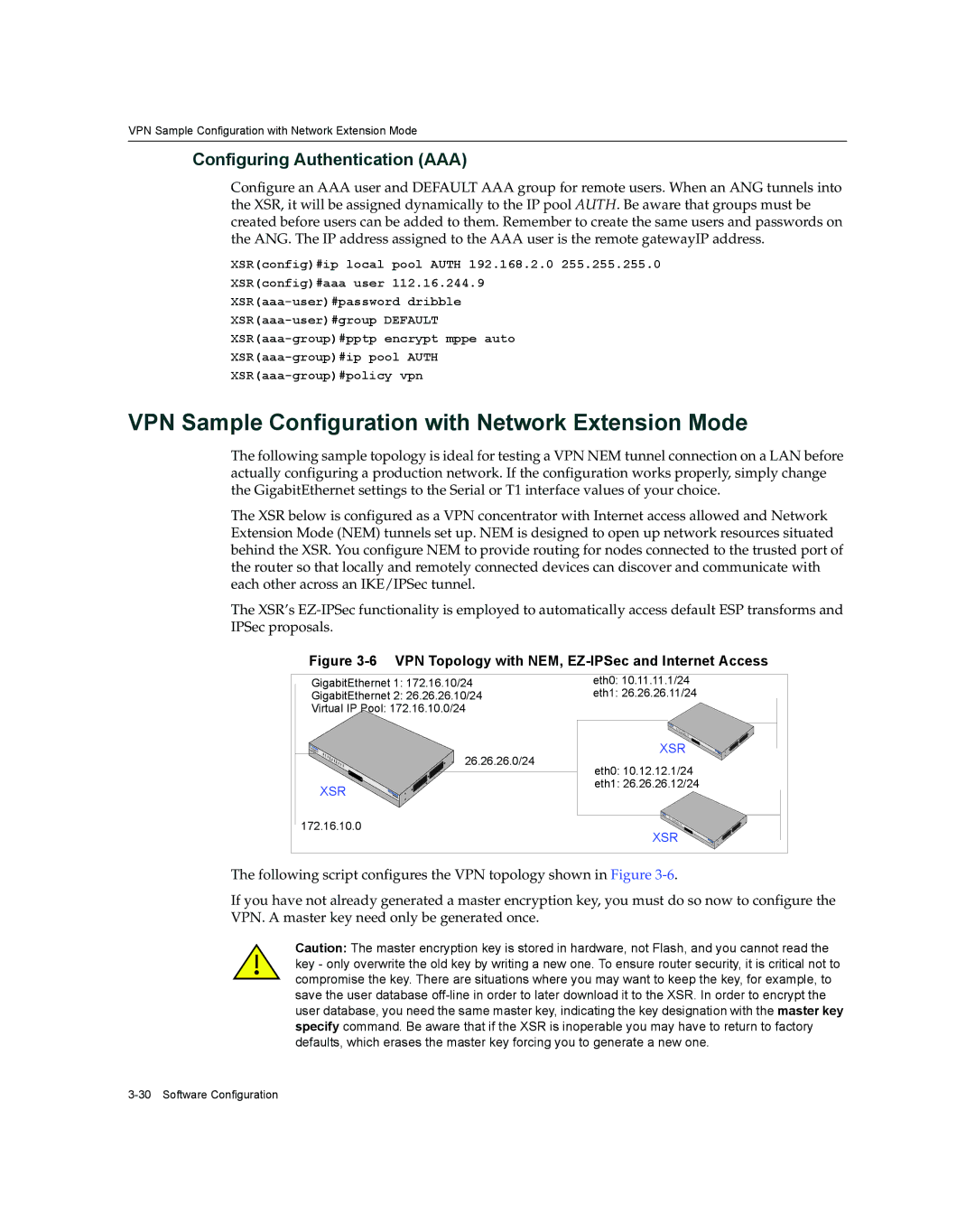
The following sample topology is ideal for testing a VPN NEM tunnel connection on a LAN before actually configuring a production network. If the configuration works properly, simply change the GigabitEthernet settings to the Serial or T1 interface values of your choice.
The XSR below is configured as a VPN concentrator with Internet access allowed and Network Extension Mode (NEM) tunnels set up. NEM is designed to open up network resources situated behind the XSR. You configure NEM to provide routing for nodes connected to the trusted port of the router so that locally and remotely connected devices can discover and communicate with each other across an IKE/IPSec tunnel.
The XSR’s
Figure 3-6 VPN Topology with NEM, EZ-IPSec and Internet Access
GigabitEthernet 1: 172.16.10/24 | eth0: 10.11.11.1/24 | |
GigabitEthernet 2: 26.26.26.10/24 | eth1: 26.26.26.11/24 | |
Virtual IP Pool: 172.16.10.0/24 |
| |
26.26.26.0/24 | XSR | |
eth0: 10.12.12.1/24 | ||
| ||
XSR | eth1: 26.26.26.12/24 | |
| ||
172.16.10.0 | XSR | |
|
The following script configures the VPN topology shown in Figure
If you have not already generated a master encryption key, you must do so now to configure the VPN. A master key need only be generated once.
Caution: The master encryption key is stored in hardware, not Flash, and you cannot read the key - only overwrite the old key by writing a new one. To ensure router security, it is critical not to compromise the key. There are situations where you may want to keep the key, for example, to save the user database