Getting started | Planning the FortiGate configuration |
|
|
Otherwise, security policy configuration is similar to a NAT/Route mode configuration with a single Internet connection. You would create NAT mode firewall policies to control traffic flowing between the internal, private network and the external, public network (usually the Internet). If you have multiple internal networks, such as one or more DMZ networks, in addition to the internal, private network, you can create route mode firewall policies for traffic flowing between them.
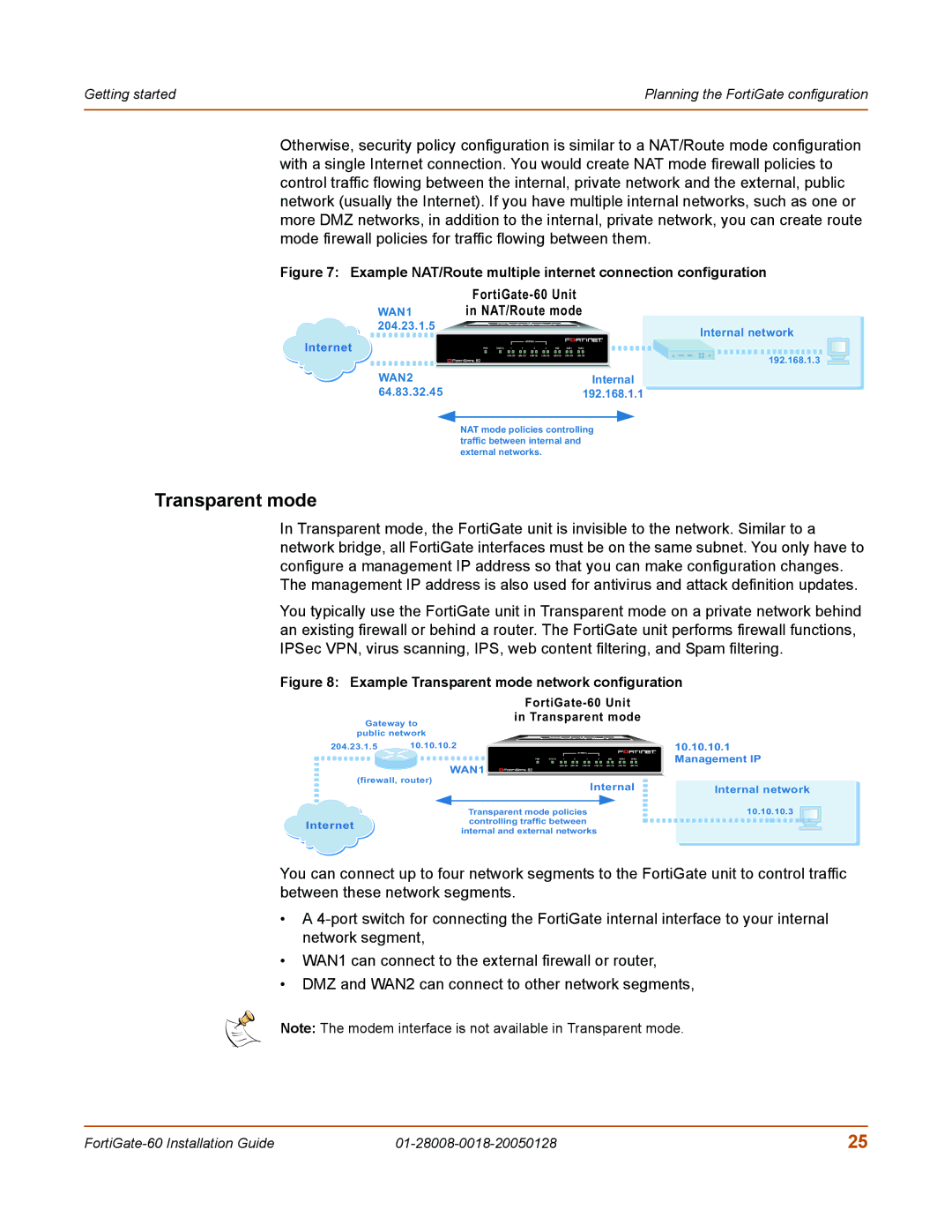
Figure 7: Example NAT/Route multiple internet connection configuration
|
| ||||||
WAN1 | in NAT/Route mode | ||||||
204.23.1.5 |
|
|
|
|
|
| Internal network |
Internet |
| INTERNAL |
|
|
| ||
|
|
|
|
| |||
LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 | |
| PWR STATUS 1 | 2 | 3 | 4 | DMZ | WAN1 | WAN2 |
|
|
|
|
|
|
| 192.168.1.3 |
WAN2 | Internal |
64.83.32.45 | 192.168.1.1 |
NAT mode policies controlling traffic between internal and external networks.
Transparent mode
In Transparent mode, the FortiGate unit is invisible to the network. Similar to a network bridge, all FortiGate interfaces must be on the same subnet. You only have to configure a management IP address so that you can make configuration changes. The management IP address is also used for antivirus and attack definition updates.
You typically use the FortiGate unit in Transparent mode on a private network behind an existing firewall or behind a router. The FortiGate unit performs firewall functions, IPSec VPN, virus scanning, IPS, web content filtering, and Spam filtering.
Figure 8: Example Transparent mode network configuration
Gateway to
public network
FortiGate-60 Unit
in Transparent mode
204.23.1.510.10.10.2 ![]() WAN1
WAN1
|
|
| INTERNAL |
|
|
|
| |
PWR | STATUS | 1 | 2 | 3 | 4 | DMZ | WAN1 | WAN2 |
|
| LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 | LINK 100 |
10.10.10.1 Management IP
(firewall, router)
| Internal | Internal network |
|
| |
| Transparent mode policies | 10.10.10.3 |
Internet | controlling traffic between |
|
internal and external networks |
| |
|
|
You can connect up to four network segments to the FortiGate unit to control traffic between these network segments.
•A
•WAN1 can connect to the external firewall or router,
•DMZ and WAN2 can connect to other network segments,
Note: The modem interface is not available in Transparent mode.
25 |