Access Security Guide
Page
December
Access Security Guide
Publication Number
Contents
Terminology Operating Rules and Notes
Contents Overview Client Options General Features
Configuring the Switch To Access a Radius Server
Messages Related to TACACS+ Operation Operating Notes
Viewing the Switch’s Current Authentication Configuration
Configuring the Switch’s TACACS+ Server Access
General Authentication Process Using a TACACS+ Server
Local Authentication Process
Configuring Secure Shell SSH
Vii
Generate the Switch’s Server Host Certificate
Common Errors in SSL Setup
Viii
Configuring and Monitoring Port Security
Operating Notes for Port Security
Contents
Access Levels
Web Configuring IP Authorized Managers
Switch manual set includes the following
About Your Switch Manual Set
Xii
Feature Index
Feature
Configuration Management Guide
Xiii
Product Documentation Feature
Tftp
Xiv
Getting Started
Contents
Getting Started
Overview of Access Security Features
Access security features covered in this guide include
Introduction
Fabric than if you use only local passwords
Management Access Security Protection
Management Access Security Protection
General Switch Traffic Security Guidelines
Conventions
Feature Descriptions by Model
Command Syntax Statements
Port Identity Examples
Command Prompts
Screen Simulations
Getting Help in the Menu Interface
Sources for More Information
Main Menu of the Menu interface, select
Run Setup
Need Only a Quick Start?
IP Addressing
Interpreting LED behavior
To Set Up and Install the Switch in Your Network
This page is intentionally unused
Configuring Username and Password Security
Web browser interface
Overview
T e U t i o n
Console Passwords
Configuring Local Password Security
Menu Setting Passwords
To set a new password
Commands Used in This Section
CLI Setting Passwords and Usernames
Continue Deletion of password protection? No
Click on the Security tab
Web Setting Passwords and Usernames
Click on Device Passwords
Front-Panel Security
When Security Is Important
Clear Button
ResetClear
Front-Panel Button Functions
Press and hold the Reset button
Reset Button
Restoring the Factory Default Configuration
ResetClear Self Test
Configuring Front-Panel Security
Syntax show front-panel-security
Default Front-Panel Security Settings
Either form of the command enables password-clear
Example of Re-Enabling the Clear Button’s Default Operation
Changing the Operation of the Reset+Clear Combination
Management access to the switch
Password Recovery
Disabling or Re-Enabling the Password Recovery Process
Default configuration settings
No front-panel-security password-recovery
Steps for Disabling Password-Recovery
11. Example of the Steps for Disabling Password-Recovery
Password Recovery Process
This page is intentionally unused
Overview Client Options General Features
Overview
Radius server uses the device MAC address as the username
Lock a particular device to a specific switch and port
Client Options
General Features
Web-based Authentication
How Web and MAC Authentication Operate
Authenticator Operation
Progress Message During Authentication
MAC-based Authentication
How Web and MAC Authentication Operate
Terminology
Management
Operating Rules and Notes
Operating Rules and Notes
Do These Steps Before You Configure Web/MAC Authentication
General Setup Procedure for Web/MAC Authentication
General Setup Procedure for Web/MAC Authentication
Aabbcc-ddeeff Aa-bb-cc-dd-ee-ff Aabbccddeeff
Addresses
Radius Server Configuration Commands
Configuring the Switch To Access a Radius Server
Example of Configuring a Switch To Access a Radius Server
Overview
Configuring Web Authentication
Command Configuration Level
Configure the Switch for Web-Based Authentication
Syntax no aaa port-access web-based e port-list
Syntax aaa port-access web-based e port-list max-requests
Default 30 seconds
Configuring MAC Authentication on Switch
Configure the Switch for MAC-Based Authentication
Syntax
Default 30seconds
Command
Show Status and Configuration Web-Based Authentication
Show Status and Configuration of MAC-Based Authentication
Syntax show port-access port-list mac-based clients
Timed out-unauth vlan
Show Client Status
This page is intentionally unused
TACACS+ Authentication
Example of TACACS+ Operation
TACACS+ Authentication
Terminology Used in Tacacs Applications
TACACS+ Authentication
General System Requirements
General Authentication Setup Procedure
Determine the following
Using the Encryption Key on
TACACS+ Authentication
Before You Begin
Configuring TACACS+ on the Switch
Switch offers three command areas for TACACS+ operation
This example shows the default authentication configuration
CLI Commands Described in this Section
Viewing the Switch’s Current Authentication Configuration
Example of the Switch’s TACACS+ Configuration Listing
Configuring the Switch’s Authentication Methods
Method/privilege path. Available only if the primary method
AAA Authentication Parameters
Name Default Range Function
Authentication for the access being configured is local
Login Primary to Local authentication
Primary/Secondary Authentication Table
ProCurve config# aaa authentication num-attempts
Switch or your TACACS+ server
Configuring the Switch’s TACACS+ Server Access
Syntax tacacs-server host ip-addr key key-string
Name Default Range Tacacs-server host ip-addr None
Details on Configuring Tacacs Servers and Keys
Timeout 1
Name Default Range Key key-string None null
To configure north01 as a per-server encryption key
ProCurveconfig# no tacacs-server host
Changes without executing write mem
How Authentication Operates
General Authentication Process Using a TACACS+ Server
TACACS+ Authentication
Terminal must initiate a new session before trying again
Local Authentication Process
Authentication
General Operation
Using the Encryption Key
Encryption Options in the Switch
ProCurveconfig# tacacs-server key north40campus
CLI Message Meaning
Tacacs-server configuration
Messages Related to TACACS+ Operation
Operating Notes
TACACS+ Authentication
Radius Authentication and Accounting
Radius Authentication and Accounting
Web Series 2600, 2600-PWR, and 2800 switches Port-Access
Host See Radius Server
Switch Operating Rules for Radius
Preparation for Configuring Radius on the Switch
General Radius Setup Procedure
Radius Authentication Commands
Configuring the Switch for Radius Authentication
Radius server documentation
Outline of the Steps for Configuring Radius Authentication
Radius Authentication and Accounting
Example Configuration for Radius Authentication
Configuring Radius Accounting instead of continuing here
Configure the Switch To Access a Radius Server
Radius Authentication and Accounting
Configure the Switch’s Global Radius Parameters
T e
Radius Authentication and Accounting
Listings of Global Radius Parameters Configured In Figure
Local Authentication Process
Radius Accounting Commands
Configuring Radius Accounting
This section assumes you have already
Access methods
Configured one or more Radius servers to support the switch
Under Port-Based Access Control
Operating Rules for Radius Accounting
Steps for Configuring Radius Accounting
Configure the Switch To Access a Radius Server
Key key-string
Radius Authentication and Accounting
Start-Stop
Syntax no aaa accounting update periodic 1
General Radius Statistics
Viewing Radius Statistics
Term Definition
Values for Show Radius Host Output Figure
Syntax show authentication
Radius Authentication Statistics
Radius Accounting Statistics
14. Listing the Accounting Configuration in the Switch
17. Search Order for Accessing a Radius Server
Changing RADIUS-Server Access Order
18. Example of New Radius Server Search Order
Message Meaning
Messages Related to Radius Operation
This page is intentionally unused
Configuring Secure Shell SSH
Configuring Secure Shell SSH
Client Public Key Authentication Model
Using these algorithms unless otherwise noted
Use a key to authenticate itself to the switch
Terminology
Public Key Formats
Prerequisite for Using SSH
Primary SSH
Authentication
SSH Options
Configuring Secure Shell SSH
General Operating Rules and Notes
SSH-Related Commands in This Section
Configuring the Switch for SSH Operation
Assign Local Login Operator and Enable Manager Password
Example of Configuring Local Passwords
Generate the Switch’s Public and Private Key Pair
Pair automatically disables SSH
To the switch using the earlier pair
CLI kill command
Operation
Provide the Switch’s Public Key to Clients
For example, to generate and display a new key
Example of a Public Key Generated by the Switch
Inserted Bit Exponent e Modulus n
Switch’s Public and Private Key Pair on
To enable SSH on the switch
49, 80, 1506,
Always 896 bits
U t i o n T e
Configure the Switch for SSH Authentication
Option B Configuring the Switch for Client Public-Key SSH
Copies a public key file into the switch
Use an SSH Client To Access the Switch
Further Information on SSH Client Public-Key Authentication
Configuring Secure Shell SSH
14. Example of a Client Public Key
Ascii
Property Supported Comments Value
Deletes the client-public-key file from the switch
U t i o n
00000K Peer unreachable
Messages Related to SSH Operation
Generating new RSA host key. If
Steps for Configuring and Using SSL for Switch
Configuring Secure Socket Layer SSL
Configuring Secure Socket Layer SSL
Server Certificate authentication with User Password
Otherwise noted
3DES 168-bit, 112 Effective
RC4 40-bit, 128-bit
Configuring Secure Socket Layer SSL
Prerequisite for Using SSL
General Operating Rules and Notes
SSL-Related CLI Commands in This Section
Configuring the Switch for SSL Operation
Security Tab Password Button
Earlier certificate
Generate the Switch’s Server Host Certificate
Particular switch/client session, and then discarded
Verified unequivocally
CLI
To Generate or Erase the Switch’s Server Certificate with
Field Name Description
Comments on Certificate Fields
Certificate Field Descriptions
For example, to generate a key and a new host certificate
For example, to display the new server host certificate
Can resume SSL operation
Configuring Secure Socket Layer SSL
Configuring Secure Socket Layer SSL
Web browser Interface showing current SSL Host Certificate
Configuring Secure Socket Layer SSL
Example of a Certificate Request and Reply
T e
Execute no web-management ssl
Using the CLI interface to enable SSL
Using the web browser interface to enable SSL
Zeroize the switch’s host certificate or certificate key.
Enable SLL Port number Selection
Error During Possible Cause
Common Errors in SSL Setup
This page is intentionally unused
Operating Rules for Authorized-Client
Configuring Port-Based Access Control
Configuring Port-Based Access Control
Why Use Port-Based Access Control?
Configuring Port-Based Access Control
Example of an 802.1X Application
How 802.1X Operates
Example of Supplicant Operation
Switch-Port Supplicant Operation
Authenticator at the same time
802.1X standard
General Operating Rules and Notes
Configuring Port-Based Access Control
Do These Steps Before You Configure 802.1X Operation
General Setup Procedure for Port-Based Access Control
Authenticators operate as expected
Overview Configuring 802.1X Authentication on Switch
Configuring Port-Based Access Control
802.1X Authentication Commands
Configuring Switch Ports as 802.1X Authenticators
Enable 802.1X Authentication on Selected Ports
Quiet-period 0
Max-requests 1
Clears authenticator statistics counters
Example of 802.1X Port-Access Authentication
Configure the 802.1X Authentication Method
Enter the Radius Host IP Addresses
Enable 802.1X Authentication on the Switch
Introduction
802.1X Open Vlan Mode
802.1X-Related Show Commands Radius server configuration
Membership in the Vlan
Use Models for 802.1X Open Vlan Modes
802.1X Open Vlan Mode
1X Open Vlan Mode Options
802.1X Per-Port Configuration Port Response
Condition Rule
Multiple Authenticator Ports Using
Before you configure the 802.1X Open Vlan mode on a port
Setting Up and Configuring 802.1X Open Vlan Mode
Mised by an unauthorized client
Vlan Operation
Activate authentication on the switch
Port-Security To Allow Only 802.1X Devices on
ProCurveconfig# aaa authentication port-access eap-radius
802.1X Open Vlan Operating Notes
ProCurveconfig# aaa port-access authenticator e A10
Enables 802.1X authentication on the port
802.1X Authentication Commands 802.1X Supplicant Commands
Default supplicant parameters or any previously configured
Enter secret password Repeat secret password
Syntax aaa port-access supplicant ethernet port-list
Max-start 1
Show Commands for Port-Access Authenticator
Displaying 802.1X Configuration Statistics, and Counters
Show port-access authenticator Syntax Config e port-list
Viewing 802.1X Open Vlan Mode Status
Authenticator
Open Vlan Mode Status
802.1X authentication
Access Control
No Pvid The port is not an untagged member of any Vlan
Status Indicator Meaning
Current Vlan ID
Switch reboots
Show Commands for Port-Access Supplicant
Supplicant port detects a different authenticator device
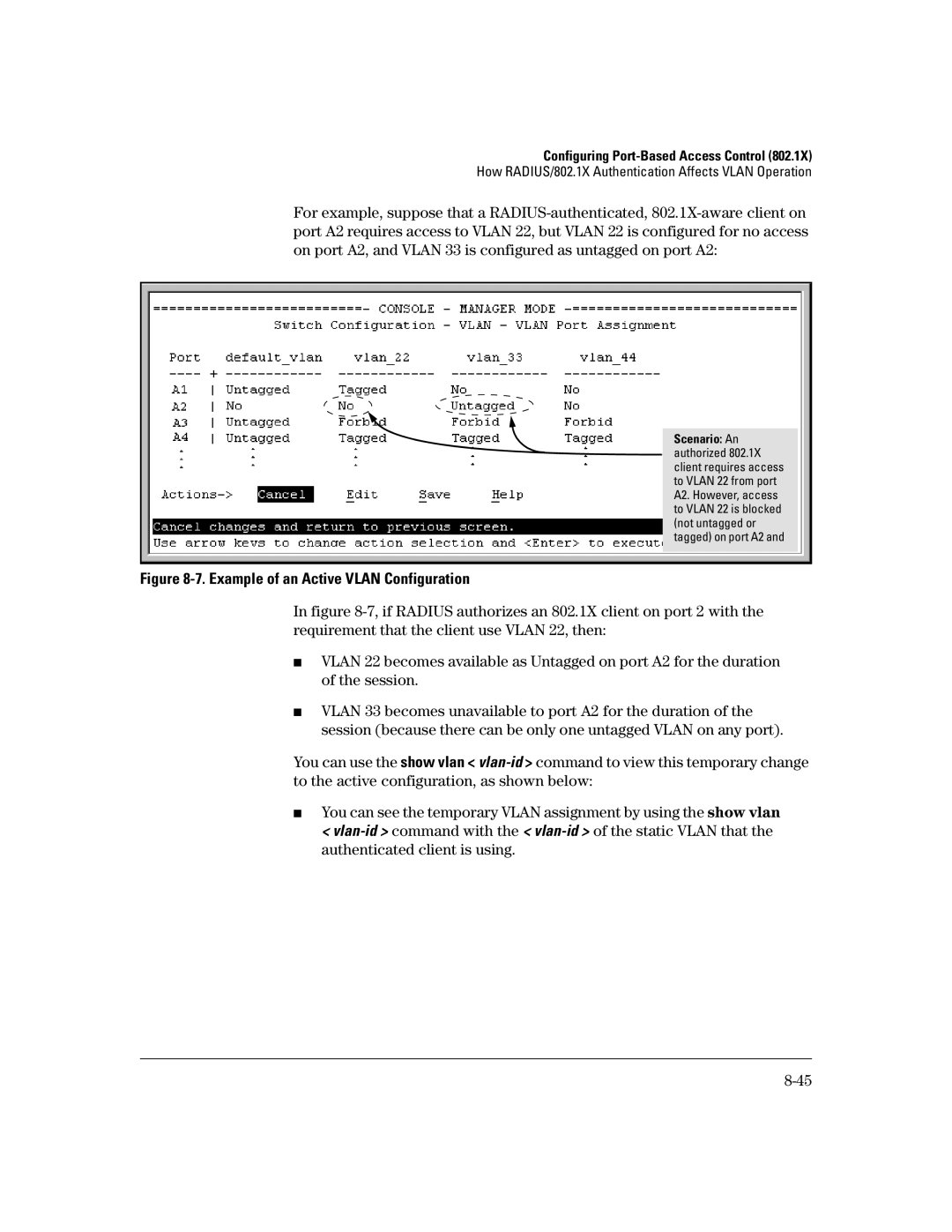
How RADIUS/802.1X Authentication Affects Vlan Operation
Example of an Active Vlan Configuration
Otherwise, port A2 is not listed
Assignment
1X Operating Messages
Messages Related to 802.1X Operation
Configuring and Monitoring Port Security
Cast traffic
Configuring and Monitoring Port Security
Basic Operation
Blocking Unauthorized Traffic
Switch C
Physical Topology Logical Topology for Access to Switch a
Switch B
Switch a
Planning Port Security
Acquires and maintains authorized addresses
Port Security Command Options Operation
Port Security Commands Used in This Section
Commands
00f031-423fc1 4 b0-880a80 the authorized address
080090-1362f2
Address-limit integer
Clear-intrusion-flag
Assigned/Authorized MAC Addresses
Displaying Current Port Security Settings
Retention of Static MAC Addresses
Learned MAC Addresses
Using the CLI To Display Port Security Settings
Specifying Authorized Devices and Intrusion Responses
Configuring Port Security
Adding a MAC Address to an Existing Port List
Example of Adding a Second Authorized Device to a Port
Example of Adding an Authorized Device to a Port
See the MAC Address entry in the table on
Device’s MAC address. For example
Remove 0c0090-123456 from the Authorized Address list
Address configuration. Refer to the Note on
Example of Port A1 After Removing One MAC Address
MAC Lockdown
Configuring and Monitoring Port Security
Differences Between MAC Lockdown and Port Security
MAC Lockdown Operating Notes
Deploying MAC Lockdown
MAC Lockdown Deployed At the Network Edge Provides Security
Inside the Core Network as well, not just on the edge
Edge switches
Address and stealing data
External Network X e d U s e r s
11. Listing Locked Down Ports
MAC Lockout
Configuring and Monitoring Port Security
12. Listing Locked Out Ports
Port Security and MAC Lockout
Operating Rules for IP Lockdown
Using the IP Lockdown Command
IP lockdown command operates as follows
IP Lockdown
Click on Port Security
Web Displaying and Configuring Port Security Features
Reading Intrusion Alerts and Resetting Alert Flags
Log command displays the Event Log
How the Intrusion Log Operates
It detects
Resetting Alert Flags
Flags
As follows
15. Example of the Intrusion Log Display
Type I Intrusion log to display the Intrusion Log
Configuring and Monitoring Port Security
List intrusion log content
18. Example of Port Status Screen After Alert Flags Reset
Event Log lists port security intrusions as
Using the Event Log To Find Intrusion Alerts
Operating Notes for Port Security
Configuring and Monitoring Port Security
Traffic/Security Filters
ProCurve Series 2600/2600-PWR and 2800 Switches
10-2
10-3
Filter for the Actions Shown in Figure
Operating Rules for Source-Port Filters
Using Source-Port Filters
10-5
Configuring a Source-Port Filter
10-6
ProCurveconfig# filter source-port trk1 drop trk2,10-15
Source Port Destination Action Ports
Viewing a Source-Port Filter
10-7
10-8
Filter Indexing
10-9
Editing a Source-Port Filter
10-10
Using Named Source-Port Filters
Defining and Configuring Named Source-Port Filters
Operating Rules for Named Source-Port Filters
10-11
10-12
Sample Configuration for Named Source-Port Filters
Viewing a Named Source-Port Filter
Applying Example Named Source-Port Filters
Source Port
10-14
10-15
10-16
10-17
10-18
Operating Notes 11-1
Using Authorized IP Managers
Using Authorized IP Managers
Authorized IP Manager Features
You can configure
Access Levels
Configuration Options
11-4
Defining Authorized Management Stations
Overview of IP Mask Operation
11-5
Menu Viewing and Configuring IP Authorized Managers
Switch Configuration … IP Authorized Managers
From the console Main Menu, select
Authorized IP Managers Commands Used in This Section
CLI Viewing and Configuring Authorized IP Managers
Listing the Switch’s Current Authorized IP Managers
IP Mask
Configuring IP Authorized Managers for the Switch
11-7
11-8
Address of the authorized manager you want to delete
Analysis of IP Mask for Single-Station Entries
Web Configuring IP Authorized Managers
Configuring One Station Per Authorized Manager IP Entry
Building IP Masks
Any value from 0 to
11-10
11-11
Additional Examples for Authorizing Multiple Stations
Operating Notes
Index
Index
See RADIUS. message
See SSH. proxy Web server … Quick start …
Show accounting … 5-28 show authentication …
See RADIUS. troubleshooting
Vlan
This page is intentionally unused
December