Wireless-G Ethernet Bridge with 5-Port Switch
WPA RADIUS
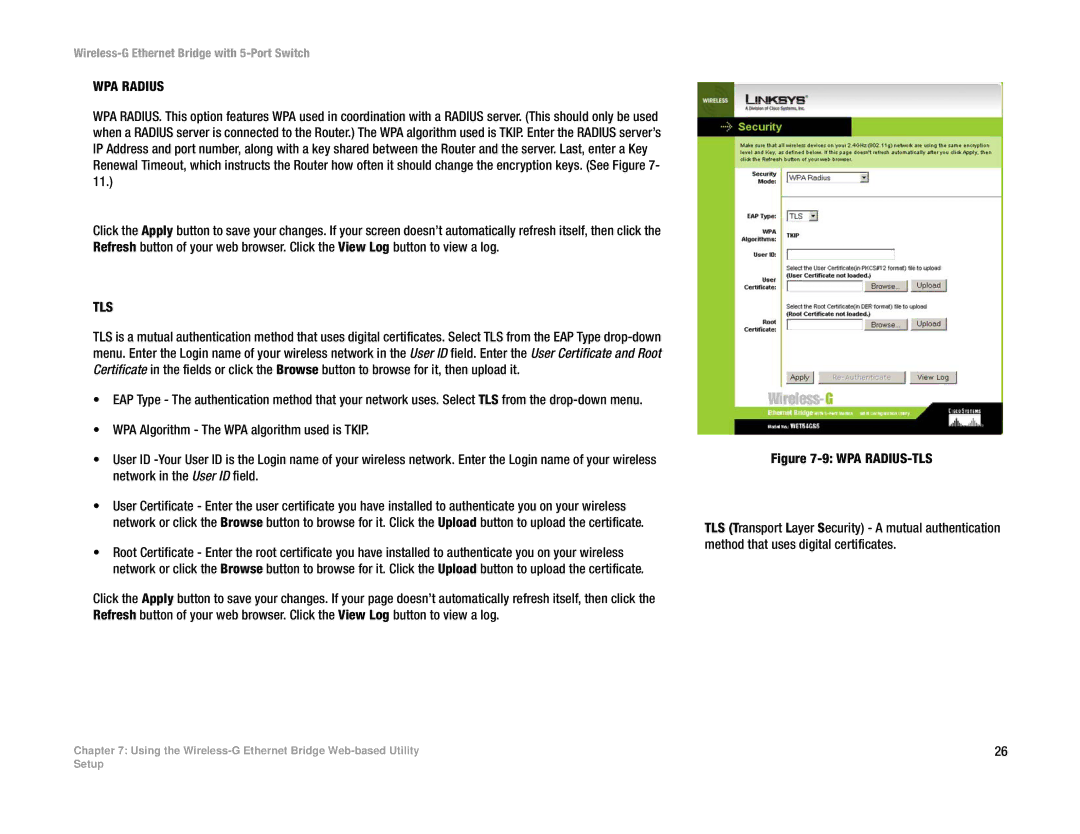
WPA RADIUS. This option features WPA used in coordination with a RADIUS server. (This should only be used when a RADIUS server is connected to the Router.) The WPA algorithm used is TKIP. Enter the RADIUS server’s IP Address and port number, along with a key shared between the Router and the server. Last, enter a Key Renewal Timeout, which instructs the Router how often it should change the encryption keys. (See Figure 7- 11.)
Click the Apply button to save your changes. If your screen doesn’t automatically refresh itself, then click the Refresh button of your web browser. Click the View Log button to view a log.
TLS
TLS is a mutual authentication method that uses digital certificates. Select TLS from the EAP Type
•EAP Type - The authentication method that your network uses. Select TLS from the
•WPA Algorithm - The WPA algorithm used is TKIP.
•User ID
•User Certificate - Enter the user certificate you have installed to authenticate you on your wireless network or click the Browse button to browse for it. Click the Upload button to upload the certificate.
•Root Certificate - Enter the root certificate you have installed to authenticate you on your wireless network or click the Browse button to browse for it. Click the Upload button to upload the certificate.
Click the Apply button to save your changes. If your page doesn’t automatically refresh itself, then click the Refresh button of your web browser. Click the View Log button to view a log.
Figure 7-9: WPA RADIUS-TLS
TLS (Transport Layer Security) - A mutual authentication method that uses digital certificates.
Chapter 7: Using the | 26 |
Setup